Very light on resource and Robust.OSArmor Personal v1.6.8:
NoVirusThanks OSArmor
- Thread starter Evjl's Rain
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
We've released OSArmor v1.6.8:
Here is the changelog:
If you find false positives or issues please let me know.
// Everyone
If you are running the test builds please update to this final version.

Download OSArmor for Windows 7, 8, 10, 11 (32 & 64-bit) | OSArmor
Download the setup file for OSArmor Personal, Business and Enterprise version for Windows 7, 8, 10, 11 (32 & 64-bit). All executable files are digitally signed and free from adware.
www.osarmor.com
Here is the changelog:
Code:
+ Fixed all reported false positives
+ Fixed some false positives on Windows Server 2016
+ Added more signers to Trusted Vendors list
+ Added Block execution of any process related to Python
+ Added Block any process related to Jernej Simončič (wget & netcat signed)
+ Added Block execution of wget.exe
+ Include process and parent process file size in blocked-process events
+ Improved monitoring of processes with large file size (e.g 50+ MB)
+ Improved internal rules to block suspicious behaviors
+ Improved detection of malformed/obfuscated command-lines
+ Improved installer and uninstaller scripts
+ Minor improvementsIf you find false positives or issues please let me know.
// Everyone
If you are running the test builds please update to this final version.
Interesting....there is more fallout from the latest NVIDIA hacking incident where the group stole a LOT of important data--incl. a certificate which can then be used to sign malware. And it seems this has already happened.
Good to know OSA can block this malicious process, provided the proper setting/s are enabled.
Good to know OSA can block this malicious process, provided the proper setting/s are enabled.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 1 for OSArmor Personal v1.6.9:

 www.wilderssecurity.com
www.wilderssecurity.com
This is the changelog so far:
+ Fixed all reported false positives
+ Added new internal rules to block suspicious behaviors
+ Improved the pre-filled text of exclusion rule when button "Exclude" is clicked
+ Updated NVT License Manager with latest version
+ Added more signers to Trusted Vendors list
+ Minor improvements
Please let me know if you find issues or FPs.
Thanks guys!
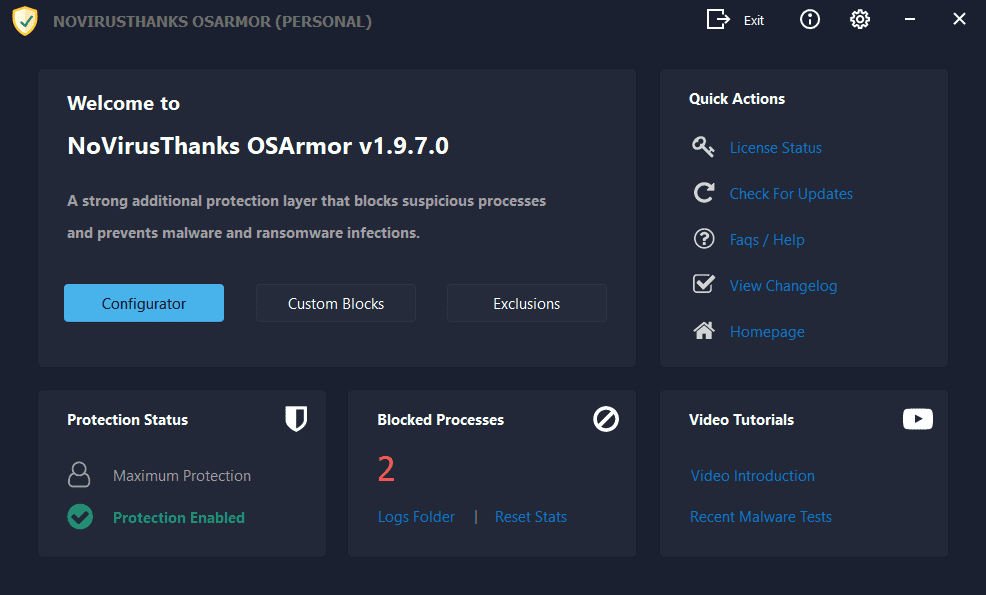
NoVirusThanks OSArmor: An Additional Layer of Defense
Oh, OK, and you know, I seem to remember this little issue coming up before somewhere. Maybe I should've searched first. OK, thanks for the info,...
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 2 for OSArmor Personal v1.6.9:

 www.wilderssecurity.com
www.wilderssecurity.com
NoVirusThanks OSArmor: An Additional Layer of Defense
Oh, OK, and you know, I seem to remember this little issue coming up before somewhere. Maybe I should've searched first. OK, thanks for the info,...
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 5 for OSArmor Personal v1.6.9:

 www.wilderssecurity.com
www.wilderssecurity.com
+ Added support for a dark theme if Windows Dark Mode is enabled
Screenshot of OSA when Windows Dark Mode is enabled:
* To test the dark theme, exit OSA GUI via OSA system tray icon -> Exit GUI -> Confirm action
* Now enable Windows Dark Mode and then start OSArmor UI
* In shorts, OSA GUI needs to be restarted
Please let me know if you find issues or FPs.
Thanks guys!
NoVirusThanks OSArmor: An Additional Layer of Defense
The exclusion popup is also hard to read, even on 1.6.9 pre test2. I understand the concern, definitely. I just tried it out again, enabling block of...
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 7 for OSArmor Personal v1.6.9:
 This issue:
This issue:

 www.wilderssecurity.com
www.wilderssecurity.com
This new test version fixes the issue reported by itman.
NoVirusThanks OSArmor: An Additional Layer of Defense
The exclusion popup is also hard to read, even on 1.6.9 pre test2. I understand the concern, definitely. I just tried it out again, enabling block of...
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
We've released OSArmor v1.6.9:
Download OSArmor for Windows 7, 8, 10, 11 (32 & 64-bit) | OSArmor
Here is the changelog:
:
+ Fixed all reported false positives
+ Added new internal rules to block suspicious behaviors
+ Improved the pre-filled text of exclusion rule when button "Exclude" is clicked
+ Updated NVT License Manager with latest version
+ Added more signers to Trusted Vendors list
+ Added support for a dark theme if Windows Dark Mode is enabled
+ Minor improvements
If you find false positives or issues please let me know.
// Everyone
If you are running the test builds please update to this final version.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 1 for OSArmor Personal v1.7.0:

 www.wilderssecurity.com
www.wilderssecurity.com
This is the changelog so far:
+ Fixed all reported false positives
+ Added new internal rules to block suspicious behaviors
+ Improved installer and uninstaller scripts
+ Minor improvements
Let me know if you find issues or FPs.
NoVirusThanks OSArmor: An Additional Layer of Defense
@novirusthanks -- OSArmor's license manager constantly uses cpu. AFAIK, none of my other security apps have a separate, real-time license manager using...
Thanks for the link. Have not used this product for a few years now but it's certainly a nice tool to have in your arsenal.Here is a pre-release test 1 for OSArmor Personal v1.7.0:

NoVirusThanks OSArmor: An Additional Layer of Defense
@novirusthanks -- OSArmor's license manager constantly uses cpu. AFAIK, none of my other security apps have a separate, real-time license manager using...www.wilderssecurity.com
G
Guilhermesene
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 10 for OSArmor Personal v1.7.0:

 www.wilderssecurity.com
www.wilderssecurity.com
This is the changelog so far:
+ Fixed all reported false positives
+ Added Block system processes on user space
+ Added new internal rules to block suspicious behaviors
+ Added more signers to Trusted Vendors list
+ Allow to use wildcards on IgnoredNotifications.db
+ Added Copy to Clipboard popup option on Manage Ignored Notifications
+ Improved installer and uninstaller scripts
+ Minor improvements
Let me know if you find any issues.
This rule "Block system processes on user space" is mostly oriented to companies and blocks system processes found in user space (i.e WerFault.exe copied to a user-writable folder and used to load wer.dll -malicious- in the same folder).
In my tests it didn't generate any alerts of legit behaviors, but it may depend on how you utilize the PC.
The rule needs to be enabled manually, it is not enabled in any protection profile at the moment.
We'll start working on SysHardener this week.
Currently SH works fine on W10 and W11, we're going to make it simpler and add new OS hardening tweaks.
NoVirusThanks OSArmor: An Additional Layer of Defense
far away from human brain, more like reptile brain Perhaps you underestimate some reptiles? ;)
We've released OSArmor v1.7.0:

Here is the changelog:
If you find false positives or issues please let me know.
// Everyone
If you are running the test builds please update to this final version.

Download OSArmor for Windows 7, 8, 10, 11 (32 & 64-bit) | OSArmor
Download the setup file for OSArmor Personal, Business and Enterprise version for Windows 7, 8, 10, 11 (32 & 64-bit). All executable files are digitally signed and free from adware.
www.osarmor.com
Here is the changelog:
Code:
+ Fixed all reported false positives
+ Added Block system processes on user space
+ Added new internal rules to block suspicious behaviors
+ Added more signers to Trusted Vendors list
+ Allow to use wildcards on IgnoredNotifications.db
+ Added Copy to Clipboard popup option on Manage Ignored Notifications
+ Improved installer and uninstaller scripts
+ Minor improvementsIf you find false positives or issues please let me know.
// Everyone
If you are running the test builds please update to this final version.
- Oct 25, 2014
- 2,636
- 7,291
- 3,588
- 40
We've released OSArmor v1.7.1:
Fixed all reported false positives
Added new internal rules to block suspicious behaviors
Minor improvements


With best Regards
Mops21
Fixed all reported false positives
Added new internal rules to block suspicious behaviors
Minor improvements

Changelog History | OSArmor
Here you can find what we have changed and updated on OSArmor software. We constantly improve our product with bugs fixes, features and rules to block suspicious processes.
www.osarmor.com

Download OSArmor for Windows 7, 8, 10, 11 (32 & 64-bit) | OSArmor
Download the setup file for OSArmor Personal, Business and Enterprise version for Windows 7, 8, 10, 11 (32 & 64-bit). All executable files are digitally signed and free from adware.
www.osarmor.com
With best Regards
Mops21
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 1 version of OSArmor PERSONAL v1.7.2:
Here is the changelog so far:
+ Fixed all reported false positives
+ Added "Protection Option" button on Configurator GUI
+ Added new internal rules to block suspicious behaviors
+ Improved blocking of malicious .ISO files behaviors
+ Minor improvements
Let me know if you find any issue or FP.
@plat1098 @LoneWolf
"Now that you mention it, it would be nice if the Protection Modes were somehow placed into the main body of the Configurator"
Good point, added the button "Protection Options" in the "Protections" tab that should make things easier to select protection profiles:
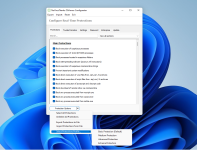
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 2 version of OSArmor PERSONAL v1.7.2:

 www.wilderssecurity.com
www.wilderssecurity.com
Just added some minor improvements on internal rules.
Let me know if you find issues or FPs.
NoVirusThanks OSArmor: An Additional Layer of Defense
Edit: oh, I see where you did say that it's intermittent for you. OK, well, maybe some other people can post also if they have this issue. It still...
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 4 version of OSArmor PERSONAL v1.7.2:
Let me know if you find issues or FPs.
NoVirusThanks OSArmor: An Additional Layer of Defense
Edit: oh, I see where you did say that it's intermittent for you. OK, well, maybe some other people can post also if they have this issue. It still...
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 5 version of OSArmor PERSONAL v1.7.2:
Let me know if you find issues or FPs.
We are discussing about enabling the following protection options in the Extreme Protection profile:
Block signers not present in Trusted Vendors List
Block processes signed with an expired certificate
Block unsigned processes on user space
Block system processes on user space
NoVirusThanks OSArmor: An Additional Layer of Defense
Hi @novirusthanks thank you for the latest release. I've encountered an issue: From the Configurator-> Protection Options->Export Protections to...
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 6 version of OSArmor PERSONAL v1.7.2:
Here is what changed:
+ Block execution of curl is now enabled on Basic Protection profile
+ Improved blocking of processes with fake file extension
+ Improved many internal rules to block suspicious behaviors
Let me know if you find issues or FPs.
NoVirusThanks OSArmor: An Additional Layer of Defense
Hi @novirusthanks thank you for the latest release. I've encountered an issue: From the Configurator-> Protection Options->Export Protections to...
- Jan 16, 2017
- 1,470
- 13,500
- 2,379
The installer size has gotten a lot bigger compared to the last time I used it few years back. There must've been a lot of new features added.
You may also like...
-
On Sale! Avast Premium Security 1 Device 1 Year 9.99€
- Started by Brownie2019
- Replies: 0
-
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Privacy News Windows 11 24H2/25H2 Flaw Keeps Task Manager Running After You Close It
- Started by Brownie2019
- Replies: 5