Yes it's fixed now
NoVirusThanks OSArmor
- Thread starter Evjl's Rain
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Here is a new v1.4 (pre-release) test51:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test51.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved detection of WannaCry ransomware
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive please let me know.
Just a quick update.
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test51.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved detection of WannaCry ransomware
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive please let me know.
Just a quick update.
Another quick update (sorry  )
)
Here is a new v1.4 (pre-release) test52:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test52.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Block execution of nslookup.exe
+ Block processes executed from regasm.exe
+ Block netsh.exe "import" and "exec" commands
+ Improved Block suspicious command-lines
+ Improved Block suspicious processes
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
We're planning to release v1.4 on 10 April (Tuesday), let me know if you find any FPs.
Here is a new v1.4 (pre-release) test52:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test52.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Block execution of nslookup.exe
+ Block processes executed from regasm.exe
+ Block netsh.exe "import" and "exec" commands
+ Improved Block suspicious command-lines
+ Improved Block suspicious processes
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
We're planning to release v1.4 on 10 April (Tuesday), let me know if you find any FPs.
you shouldn't be sorry about rapid development.Another quick update (sorry)
Here is a new v1.4 (pre-release) test52:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test52.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Block execution of nslookup.exe
+ Block processes executed from regasm.exe
+ Block netsh.exe "import" and "exec" commands
+ Improved Block suspicious command-lines
+ Improved Block suspicious processes
+ Minor fixes and optimizations
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
We're planning to release v1.4 on 10 April (Tuesday), let me know if you find any FPs.
We're planning to release v1.4 on 10 April (Tuesday), let me know if you find any FPs.
@NoVirusThanks
On the taskbar clock when I try to change date and time settings, this still appears:
Date/Time: 07/04/2018 05:04:56 p.m.
Process: [1488]C:\Windows\System32\control.exe
Parent: [1592]C:\Windows\explorer.exe
Rule: BlockSuspiciousCmdlines
Rule Name: Block execution of suspicious command-line strings
Command Line: "C:\Windows\System32\control.exe" "C:\Windows\system32\timedate.cpl",
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
With build 52
Thanks.
NVTOA it does a excelent work on my windows 7. thank you for free software product. I just ask you please enlarge the configurator box to be expandable so that don't depend on the scrollbar and the mouse wheel inside that little configurator box, because it is very uncomfortable to work a huge list in a small box .. This program does not is for small screen of smarthpone, most of us have screens with 1920x1080 and upper.
Last edited:
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
I think it's not really a FP: when using @Andy Ful 's Configure Defender the powershell commands gets blocked:
Made an exclusion:
And all is working fine 
Code:
Date/Time: 7-4-2018 18:35:53
Process: [2796]C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe
Parent: [8012]D:\Downloads\Software\ConfigureDefender_1.0.0.1\ConfigureDefender_x64.exe
Rule: BlockPowerShellMalformedCommands
Rule Name: Block execution of PowerShell malformed commands
Command Line: c:\Windows\System32\WindowsPowerShell\v1.0\PowerShell -NonInteractive -WindowStyle hidden $Preferences=Get-MpPreference;$path='HKLM:\SOFTWARE\Policies\Microsoft\Windows\safer_Hard_Configurator\Defender\TEMP'; New-ItemProperty -Path $path -Name 'PreferencesTest' -Value $Preferences.DisableRealtimeMonitoring -PropertyType String -Force | Out-Null; function SetRegistryKey ([string]$name){$svalue=$Preferences.$name;New-ItemProperty -Path $path -Name $name -Value $svalue -PropertyType DWORD -Force | Out-Null}; SetRegistryKey('EnableNetworkProtection'); SetRegistryKey( 'EnableControlledFolderAccess');SetRegistryKey('DisableRealtimeMonitoring'); SetRegistryKey('DisableBehaviorMonitoring'); SetRegistryKey('DisableBlockAtFirstSeen'); SetRegistryKey('MAPSReporting');SetRegistryKey('SubmitSamplesConsent');SetRegistryKey('DisableIOAVProtection'); SetRegistryKey('DisableScriptScanning'); SetRegistryKey('PUAProtection'); SetRegistryKey('ScanAvgCPULoadFactor');
Signer:
Parent Signer:
User/Domain:
Integrity Level: High
Code:
[%PROCESS%: C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe] [%PROCESSCMDLINE%: c:\Windows\System32\WindowsPowerShell\v1.0\PowerShell -NonInteractive -WindowStyle hidden $Preferences=Get-MpPreference;$path='HKLM:\SOFTWARE\Policies\Microsoft\Windows\safer_Hard_Configurator\Defender\TEMP'; New-ItemProperty -Path $path -Name 'PreferencesTest' -Value $Preferences.DisableRealtimeMonitoring -PropertyType String -Force | Out-Null; function SetRegistryKey ([string]$name){$svalue=$Preferences.$name;New-ItemProperty -Path $path -Name $name -Value $svalue -PropertyType DWORD -Force | Out-Null}; SetRegistryKey('EnableNetworkProtection'); SetRegistryKey( 'EnableControlledFolderAccess');SetRegistryKey('DisableRealtimeMonitoring'); SetRegistryKey('DisableBehaviorMonitoring'); SetRegistryKey('DisableBlockAtFirstSeen'); SetRegistryKey('MAPSReporting');SetRegistryKey('SubmitSamplesConsent');SetRegistryKey('DisableIOAVProtection'); SetRegistryKey('DisableScriptScanning'); SetRegistryKey('PUAProtection'); SetRegistryKey('ScanAvgCPULoadFactor');] [%PARENTPROCESS%: D:\Downloads\Software\ConfigureDefender_1.0.0.1\ConfigureDefender_x64.exe]Here is a new v1.4 (pre-release) test54:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test54.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved Block suspicious command-lines
+ Improved Block suspicious processes
+ Improved Block suspicious Svchost.exe process behaviors
+ Block execution of unsigned processes on user space
+ Block unsigned processes to run with high or system privileges
+ Block processes executed from netsh.exe
+ Block possible UAC bypass attempts [method 1]
+ Block possible UAC bypass attempts [method 2] (disabled at the moment, need to complete this)
+ Block execution of ftp\tftp\telnet.exe
+ Block suspicious process elevation attempts
+ Block InfDefaultInstall.exe if executed by unknown processes
+ Some rules have been moved to their appropriate section
+ Added text-link to reset statistics on Main GUI
+ Configurator GUI can be maximized and is resizeable
+ Added a dark-gray frame on the notification window
+ Removed Block ALL autoelevate system processes
+ Removed Block known system files used for UAC-bypass
+ Show parent process integrity level on log file
+ Show process md5 hash on log file
+ Minor fixes and optimizations
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know (official release will be postponed of some days).
Here is a screenshot:
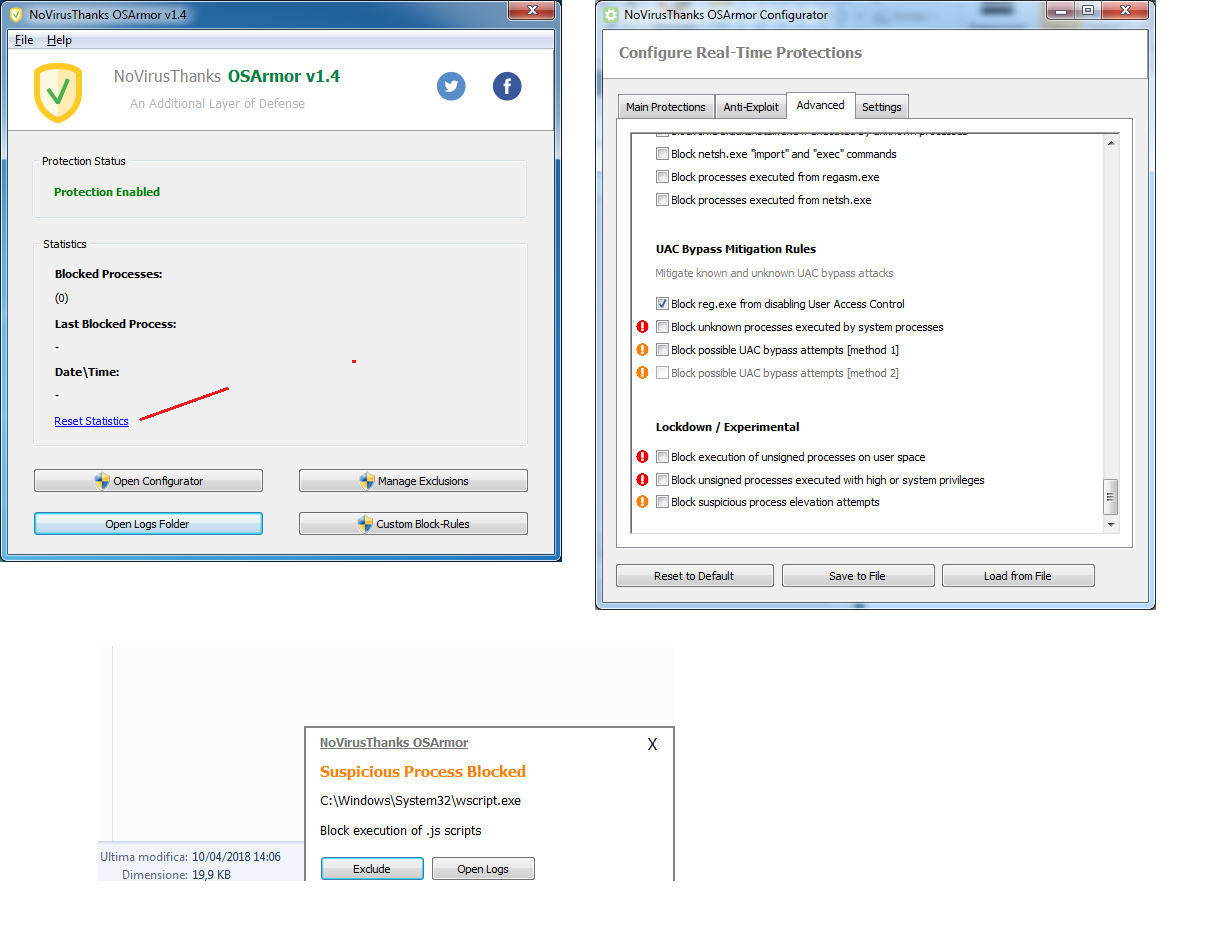
@128BPM
Should be fixed now.
@MeltdownEnemy
Done.
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test54.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved Block suspicious command-lines
+ Improved Block suspicious processes
+ Improved Block suspicious Svchost.exe process behaviors
+ Block execution of unsigned processes on user space
+ Block unsigned processes to run with high or system privileges
+ Block processes executed from netsh.exe
+ Block possible UAC bypass attempts [method 1]
+ Block possible UAC bypass attempts [method 2] (disabled at the moment, need to complete this)
+ Block execution of ftp\tftp\telnet.exe
+ Block suspicious process elevation attempts
+ Block InfDefaultInstall.exe if executed by unknown processes
+ Some rules have been moved to their appropriate section
+ Added text-link to reset statistics on Main GUI
+ Configurator GUI can be maximized and is resizeable
+ Added a dark-gray frame on the notification window
+ Removed Block ALL autoelevate system processes
+ Removed Block known system files used for UAC-bypass
+ Show parent process integrity level on log file
+ Show process md5 hash on log file
+ Minor fixes and optimizations
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know (official release will be postponed of some days).
Here is a screenshot:
@128BPM
Should be fixed now.
@MeltdownEnemy
Done.
@NoVirusThanks
Thanks, previous FPs were fixed, but:
Date/Time: 10/04/2018 12:43:19 p.m.
Process: [2764]C:\Windows\System32\control.exe
Process MD5 Hash: FD3F34830C39F4B554106ADA19924F4E
Parent: [1632]C:\Windows\explorer.exe
Rule: BlockUnknownProcessesOnWindowsFolder
Rule Name: Block unknown processes on Windows folder
Command Line: "C:\Windows\System32\control.exe" "C:\Windows\system32\timedate.cpl",
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
Date/Time: 10/04/2018 04:54:27 p.m.
Process: [456]C:\Windows\System32\SndVol.exe
Process MD5 Hash: C3489639EC8E181044F6C6BFD3D01AC9
Parent: [1512]C:\Windows\explorer.exe
Rule: BlockUnknownProcessesOnWindowsFolder
Rule Name: Block unknown processes on Windows folder
Command Line: SndVol.exe -f 49546462 26531
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
Date/Time: 10/04/2018 04:54:46 p.m.
Process: [4460]C:\Windows\SysWOW64\dllhost.exe
Process MD5 Hash: A63DC5C2EA944E6657203E0C8EDEAF61
Parent: [768]C:\Windows\System32\svchost.exe
Rule: BlockUnknownProcessesOnWindowsFolder
Rule Name: Block unknown processes on Windows folder
Command Line: C:\Windows\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B}
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: System
Thanks, previous FPs were fixed, but:
Date/Time: 10/04/2018 12:43:19 p.m.
Process: [2764]C:\Windows\System32\control.exe
Process MD5 Hash: FD3F34830C39F4B554106ADA19924F4E
Parent: [1632]C:\Windows\explorer.exe
Rule: BlockUnknownProcessesOnWindowsFolder
Rule Name: Block unknown processes on Windows folder
Command Line: "C:\Windows\System32\control.exe" "C:\Windows\system32\timedate.cpl",
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
Date/Time: 10/04/2018 04:54:27 p.m.
Process: [456]C:\Windows\System32\SndVol.exe
Process MD5 Hash: C3489639EC8E181044F6C6BFD3D01AC9
Parent: [1512]C:\Windows\explorer.exe
Rule: BlockUnknownProcessesOnWindowsFolder
Rule Name: Block unknown processes on Windows folder
Command Line: SndVol.exe -f 49546462 26531
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
Date/Time: 10/04/2018 04:54:46 p.m.
Process: [4460]C:\Windows\SysWOW64\dllhost.exe
Process MD5 Hash: A63DC5C2EA944E6657203E0C8EDEAF61
Parent: [768]C:\Windows\System32\svchost.exe
Rule: BlockUnknownProcessesOnWindowsFolder
Rule Name: Block unknown processes on Windows folder
Command Line: C:\Windows\SysWOW64\DllHost.exe /Processid:{06622D85-6856-4460-8DE1-A81921B41C4B}
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: System
Here is a new v1.4 (pre-release) test55:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test55.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Fixed Block suspicious processes
+ Block "tricks" used to run UAC-bypass system processes
+ Block unsigned processes to run with high privileges
+ Block unsigned processes to run with system privileges
+ Renamed and improved UAC-bypass mitigation rules
+ Renamed Block execution of unsigned processes on Common AppData (\ProgramData\)
+ Readded Block execution of ALL "autoelevate" system processes
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
Here is a screenshot of the new rules:
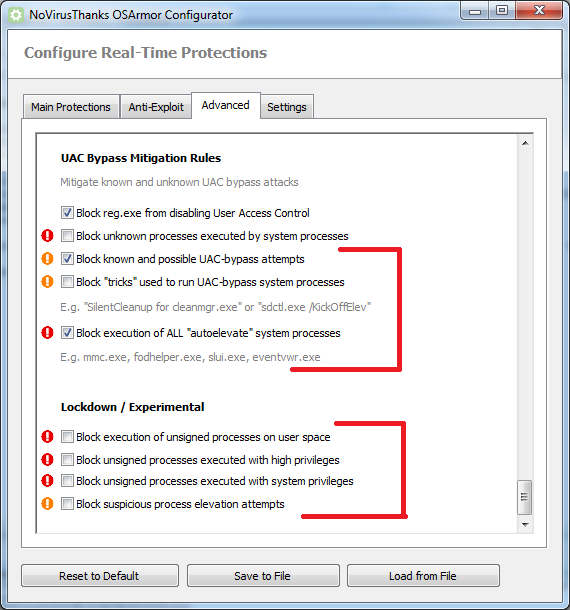
@128BPM
Should be fixed now.
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test55.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Fixed Block suspicious processes
+ Block "tricks" used to run UAC-bypass system processes
+ Block unsigned processes to run with high privileges
+ Block unsigned processes to run with system privileges
+ Renamed and improved UAC-bypass mitigation rules
+ Renamed Block execution of unsigned processes on Common AppData (\ProgramData\)
+ Readded Block execution of ALL "autoelevate" system processes
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
Here is a screenshot of the new rules:
@128BPM
Should be fixed now.
@NoVirusThanks
Previous FPs are fixed, now:
Date/Time: 10/04/2018 07:50:36 p.m.
Process: [3376]C:\Windows\System32\rundll32.exe
Process MD5 Hash: C36BB659F08F046B139C8D1B980BF1AC
Parent: [2568]C:\Windows\System32\control.exe
Rule: PreventRundll32Control_RunDLL
Rule Name: Prevent rundll32.exe from using Control_RunDLL (shell32.dll)
Command Line: "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\system32\timedate.cpl",
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
Date/Time: 10/04/2018 08:07:11 p.m.
Process: [5100]C:\Windows\System32\mmc.exe
Process MD5 Hash: 007665F8DE4B18F82CEC63313F8ADCD2
Parent: [1548]C:\Windows\explorer.exe
Rule: BlockMSCScripts
Rule Name: Block execution of .msc scripts
Command Line: "C:\Windows\system32\mmc.exe" C:\Windows\system32\devmgmt.msc
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: High
Parent Integrity Level: Medium
Date/Time: 10/04/2018 08:08:18 p.m.
Process: [4620]C:\Windows\System32\DeviceDisplayObjectProvider.exe
Process MD5 Hash: 7E2EB3A4AE11190EF4C8A9B9A9123234
Parent: [764]C:\Windows\System32\svchost.exe
Rule: BlockSuspiciousSvchostBehaviors
Rule Name: Block suspicious Svchost.exe process behaviors
Command Line: C:\Windows\system32\DeviceDisplayObjectProvider.exe -Embedding
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: System
Note: Could you add an option to reset the log?
Thanks.
Previous FPs are fixed, now:
Date/Time: 10/04/2018 07:50:36 p.m.
Process: [3376]C:\Windows\System32\rundll32.exe
Process MD5 Hash: C36BB659F08F046B139C8D1B980BF1AC
Parent: [2568]C:\Windows\System32\control.exe
Rule: PreventRundll32Control_RunDLL
Rule Name: Prevent rundll32.exe from using Control_RunDLL (shell32.dll)
Command Line: "C:\Windows\system32\rundll32.exe" Shell32.dll,Control_RunDLL "C:\Windows\system32\timedate.cpl",
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
Date/Time: 10/04/2018 08:07:11 p.m.
Process: [5100]C:\Windows\System32\mmc.exe
Process MD5 Hash: 007665F8DE4B18F82CEC63313F8ADCD2
Parent: [1548]C:\Windows\explorer.exe
Rule: BlockMSCScripts
Rule Name: Block execution of .msc scripts
Command Line: "C:\Windows\system32\mmc.exe" C:\Windows\system32\devmgmt.msc
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: High
Parent Integrity Level: Medium
Date/Time: 10/04/2018 08:08:18 p.m.
Process: [4620]C:\Windows\System32\DeviceDisplayObjectProvider.exe
Process MD5 Hash: 7E2EB3A4AE11190EF4C8A9B9A9123234
Parent: [764]C:\Windows\System32\svchost.exe
Rule: BlockSuspiciousSvchostBehaviors
Rule Name: Block suspicious Svchost.exe process behaviors
Command Line: C:\Windows\system32\DeviceDisplayObjectProvider.exe -Embedding
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: System
Note: Could you add an option to reset the log?
Thanks.
Last edited:
I have a feature suggestion. It would be nice to have an option to block (unauthorized) access to camera and microphone. Most of the time these devices are not in use by regular programs and applications should not have access without the user knowing about it. This could prevent spying on user through webcam and microphone.
Keep up the good work, awesome software.
Keep up the good work, awesome software.
... I'm sure this is well-intentioned, but I'm not a supporter of feature "bloat" which strays from OSA's core of threat protection.I have a feature suggestion.
... I'm sure this is well-intentioned, but I'm not a supporter of feature "bloat" which strays from OSA's core of threat protection.
I am also not a supporter of feature bloat but i think this would be a nice addition. I disagree that this strays away from osa core as this is about protecting camera and microphone threat.
Here is a new v1.4 (pre-release) test56:
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test56.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved showing of main GUI via tray icon -> Show/Hide Window
+ Improved Block suspicious Svchost.exe process behaviors
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
@Carphedon
Will discuss about it, in case we can create a specific program for that.
@128BPM
Fixed all FPs, except:
That is normal behavior, you may uncheck:
Block execution of .msc scripts
And instead check this:
Block execution of .msc scripts outside System folder
Sure, added in the todo list.
http://downloads.novirusthanks.org/files/osarmor_setup_1.4_test56.exe
*** Please do not share the download link, we will delete it when we'll release the official v1.4 ***
So far this is what's new compared to the previous pre-release:
+ Improved showing of main GUI via tray icon -> Show/Hide Window
+ Improved Block suspicious Svchost.exe process behaviors
+ Fixed some false positives
To install it, first uninstall the previous build, then reboot (not really needed but may help), and install the new build.
If you find any false positive or issue please let me know.
@Carphedon
Will discuss about it, in case we can create a specific program for that.
@128BPM
Fixed all FPs, except:
Date/Time: 10/04/2018 08:07:11 p.m.
Process: [5100]C:\Windows\System32\mmc.exe
Process MD5 Hash: 007665F8DE4B18F82CEC63313F8ADCD2
Parent: [1548]C:\Windows\explorer.exe
Rule: BlockMSCScripts
Rule Name: Block execution of .msc scripts
Command Line: "C:\Windows\system32\mmc.exe" C:\Windows\system32\devmgmt.msc
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: High
Parent Integrity Level: Medium
That is normal behavior, you may uncheck:
Block execution of .msc scripts
And instead check this:
Block execution of .msc scripts outside System folder
Note: Could you add an option to reset the log?
Sure, added in the todo list.
Uploaded a new video, used OSArmor 1.4 (pre-release) build 56 with default settings:
We received today 12 April 2018 an email "Re: Purchase order" with a .DOC (MS Word) file named PO0045.2018.doc. The DOC file is malicious and thanks to OSArmor the payload has been blocked.
@NoVirusThanks
The FPs were fixed, for now I think that only this one remains:
Date/Time: 11/04/2018 04:54:30 p.m.
Process: [1980]C:\Windows\System32\control.exe
Process MD5 Hash: FD3F34830C39F4B554106ADA19924F4E
Parent: [2800]C:\Windows\System32\rundll32.exe
Rule: BlockSuspiciousCmdlines
Rule Name: Block execution of suspicious command-line strings
Command Line: "C:\Windows\System32\control.exe" "C:\Windows\system32\intl.cpl",,/p:"date"
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
This appears in the option "change calendar settings"
If I find more, I'll let you know.
Thanks.
The FPs were fixed, for now I think that only this one remains:
Date/Time: 11/04/2018 04:54:30 p.m.
Process: [1980]C:\Windows\System32\control.exe
Process MD5 Hash: FD3F34830C39F4B554106ADA19924F4E
Parent: [2800]C:\Windows\System32\rundll32.exe
Rule: BlockSuspiciousCmdlines
Rule Name: Block execution of suspicious command-line strings
Command Line: "C:\Windows\System32\control.exe" "C:\Windows\system32\intl.cpl",,/p:"date"
Signer:
Parent Signer:
User/Domain: PC/PC
Integrity Level: Medium
Parent Integrity Level: Medium
This appears in the option "change calendar settings"
If I find more, I'll let you know.
Thanks.
Uploaded a new video, used OSArmor 1.4 (pre-release) build 56 with default settings:
Andreas,
I used to add a rules that that Word as a parent process was not allowed to start other programs (except print spool and touch screen keyboard processes). I see that the video blocks launching word processes from user space. Two questions:
1. Is starting other programs covered by the anti-exploit option of Word?
2. Do you have made allow exceptions for print spool and touch keyboard?
I am asking because for wscript.exe you have:
- "Block any process executed from wscript" (in Main Protections) AND
- "Protect Windows Script" (Microsoft processes secrion of Anti-Exploit)
So I thought Exploit protection only blocks execution from user space.
Thx
Regards Kees
Last edited:
The new OSArmor build is compatible now with ConfigureDefender. Thanks, Andreas.
D
Deleted member 178
It wasn't?The new OSArmor build is compatible now with ConfigureDefender. Thanks, Andreas.
You may also like...
-
On Sale! Avast Premium Security 1 Device 1 Year 9.99€
- Started by Brownie2019
- Replies: 0
-
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Privacy News Windows 11 24H2/25H2 Flaw Keeps Task Manager Running After You Close It
- Started by Brownie2019
- Replies: 5