Thread response to News: Proton Pass Retains Passwords in Cleartext Form in Memory
Reddit discussion: Continue reading
Q: Found all passwords, url's and usernames in memory (shared July 2023)
With Proton Pass for Firefox all vault passwords can be found plain in memory (RAM). This can be done if you create a memory dump file of all browser processes and then edit the images. This works even with the extension is locked. Probably it has to be unlocked first to load the passwords in RAM.
I did not see the sam behavior with other popular password managers like 1Password. They only hold the master password in memory.
Maybe somebody can reproduce this?
A: Proton Team
Most open-source password managers (as we can't verify the closed source ones) don't encrypt the passwords in memory. What they do instead is obfuscate them, which doesn't really add to the security as it can be easily reverse-engineered. Obfuscation is like writing a sentence in reverse order to keep it secret.
Memory dump attacks are out of Proton Pass scope at the moment as this attack is almost an end-game scenario. That being said, we are considering some options:
a. Adding an option to automatically log you out after a certain time.
b. Encrypting in-memory data using a combination of PIN code and some backend tokens. PIN code isn't enough, as once an attacker downloads your memory, they can perform a brute force attack at their convenience, like what happened with LastPass. However, this requires you having the internet access at all times, which is against our target of supporting offline mode.
In any case, we'll keep you informed when these options become available.
Q: Glomeg123
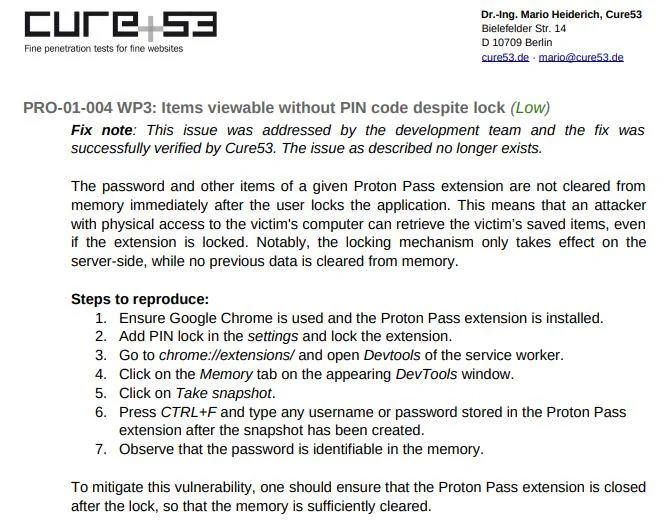
Thank you for this detailed explanation. I just don't understand one thing. If you read the latest Proton Pass security audit by cure53 it describes exact this problem. The issue is named PRO-01-004 WP3: Items viewable without PIN code despite lock. And now it get's weired. There is a fix note which says that this problem is solved and verified by Cure53. Today I reproduced the steps writen in this issue and you wonder what happend. The issue still exits of course. It's just funny that this issue is marked as solved by Cure53 and it still exits. This doesn't leave a trustfully feeling at me. Can you please explain that?
A: Proton Team
There seem to be two different questions spliced together here:
An upcoming version will also obfuscate this data further. Obfuscation, however, isn't encryption and can be quite simply reverse-engineered so basic security measures are still recommended.
- The lack of obfuscation -- this isn't a bug, as every app needs to load data into memory. As pointed out above, the memory dump attacks are out of Proton Pass's scope and are almost an end-game scenario. However, we do plan to introduce obfuscation of this data (more below).
- Data not being removed from memory immediately after the extension is locked -- this is indeed a bug (discovered yesterday) and is getting fixed in a matter of hours. We have submitted the new version (1.6.2) that removes all the data in memory as soon as you lock the extension. This version is currently in review and should be available on Chrome & Firefox stores in the coming hours.
Regarding the audit, the version the auditors checked would remove all the data in memory as soon as the extension is locked. We have in the meantime introduced a regression, which did not do it immediately, but with a delay (which is what you have noticed). As pointed out above, the upcoming version 1.6.2 fixes this.
Reddit discussion: Continue reading

