We had the same idea
View attachment 286880
Surprised it's still the 24th in India
It's 26th here in Germany, 1 PM
Submission was done about 3 hours ago
Self-Made Fortran Malware Analysis
- Thread starter HydraDragonAntivirus
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
Agree, was in Nepal just one week ago, and it's "only" 4:45h ahead of local time here (but i think they have different time zones in that small country).No its system that not updated its time....
Update: It's actually one time zone, but two different calendars, depending on which you look at - Nepal is currently in August (or close to September) 2081
Last edited:
Nepal has 1 time zone (The IANA time zone database contains one zone for Nepal in the file zone. tab, named Asia/Kathmandu.)We have 1 time zone in india but we need at least 3 time zones.. btw India is 4 hours and 30 minutes ahead of GermanyAgree, was in Nepal just one week ago, and it's "only" 4:45h ahead of local time here (but i think they have different time zones in that small country).
Last edited:
Yes, maybe I confused somethingNepal has 1 time zone (The IANA time zone database contains one zone for Nepal in the file zone. tab, named Asia/Kathmandu.)We have 1 time zone in india but we need at least 3 time zones.. btw India is 4 hours and 30 minutes ahead of Germany
Thank you for the insight
I'm quoting harlan but this is directed to everyone.Hum... the method of changing the hash just editing the exe, and adding for example 2 letters "xx" at the end of the code, and save, it is not the best way to do so, since it directly makes the executable unusable:
View attachment 286876
View attachment 286875
So no, the way of modifing the hash with Notepad is not valid, it should be via changing the programming code...
Adding values like, "xx" at the end of the code is obviously going to break the file.
The easiest and safe way to do for an average user who are not sure would be to use a program like this:
GitHub - ewwink/MD5-Hash-Changer: C# Application to Change MD5 Hash of any file
C# Application to Change MD5 Hash of any file. Contribute to ewwink/MD5-Hash-Changer development by creating an account on GitHub.
Regarding Rising, it doesn't use Kaspersky engine, I think. What it does is simply copies Virustotal detection of Kaspersky and a couple of other products. Rising is not alone in this. Some other products also do this. Sophos also add things from Virustotal and most of the time initially they are detected as, PUP by their engine. Those are cloud based detection based on Virustotal which they try to hide.
Microsoft Defender has mechanism to search for malware IOCs on Twitter/X and these are detected as, "xxxxx....Casdet", at the end of the detection name. Here Casdet means, "Casandra Detection". But they don't just blindly add detection, they have some failsafe methods for that. But it's still a cheat code like method.
The entire point of the lesson with gdi_shaka . e x e is the following:
1. Even when you have antivirus or internet security installed on a system, if you execute code then you run the risk of compromise; and
2. The only effective protection is not to execute code on the system in the first place.
i) It does not matter if you are a "user that wants to use stuff."
ii) The system must be locked-down 24/7/365.
iii) Good/Bad notifications and users making the decision to Allow/Block have a predictable outcome of infected or compromised systems.
I don't want to get into the debate "But computers are made for users to use stuff." No. They were not. Read the device EULA and any related OEM Terms of Service. The content of those documents will quickly dispel the wide-spread notion that OEMs produce systems with the intent that users can do whatever they wish on them.
PS - Since we got the whole flag thingy going, I am joining in.
1. Even when you have antivirus or internet security installed on a system, if you execute code then you run the risk of compromise; and
2. The only effective protection is not to execute code on the system in the first place.
i) It does not matter if you are a "user that wants to use stuff."
ii) The system must be locked-down 24/7/365.
iii) Good/Bad notifications and users making the decision to Allow/Block have a predictable outcome of infected or compromised systems.
I don't want to get into the debate "But computers are made for users to use stuff." No. They were not. Read the device EULA and any related OEM Terms of Service. The content of those documents will quickly dispel the wide-spread notion that OEMs produce systems with the intent that users can do whatever they wish on them.
PS - Since we got the whole flag thingy going, I am joining in.
Last edited:
but everyone who uses Xcitium you guys know VirusScope detected this gdi malware so you are protectedvery unlikely you can try
By changing the hash of the sample above as so far no av was able on detection so far with a fresh hash
Tried virus scope and sent to open tip both failed with a new hash
VirusTotal - The problem is that if you just add 0 at the end in notepad, it's not 0 but an ASCI character, which breaks Exe and it won't start at all. I added a zero at the end in HxD and all the basic detections are in place with a completely new hash.Change the hahs and try again
(Open the exe in notepad and add something in the end of the file )
Captain, you've submitted through ticket option or by mail attachment??I submitted at 12 pm Indian Standard Time andK7 already detected by Trojan(0001140e1).

Thank God some one used HxD..VirusTotal - The problem is that if you just add 0 at the end in notepad, it's not 0 but an ASCI character, which breaks Exe and it won't start at all. I added a zero at the end in HxD and all the basic detections are in place with a completely new hash.
VirusTotal - The problem is that if you just add 0 at the end in notepad, it's not 0 but an ASCI character, which breaks Exe and it won't start at all. I added a zero at the end in HxD and all the basic detections are in place with a completely new hash.
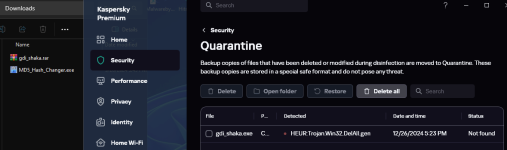
Kaspersky, ESET and Avast! continue to detect it after your modification, which is in line with my theory: they have performed a Hexa detection on the malware.
I used both.Captain, you've submitted through ticket option or by mail attachment??
But, it's just a micro hash change. I'm not sure if the detections will remain if you change the code a little bit, literally add some useless if, better ask the author of the topic @XylentAntivirus , I don't want to figure out how to compile Fortran.Kaspersky, ESET and Avast! continue to detect it after your modification, which is in line with my theory: they have performed a Hexa detection on the malware.
with a quick tweak, I've got Microsoft Defender waking up
=> Microsoft : Program:Win32/Wacapew.C!ml
Also K7 antivirus detected the tweak version with same trojan (0005bee901)
with a quick tweak, I've got Microsoft Defender waking up
=> Microsoft : Program:Win32/Wacapew.C!ml
Last edited:
- Apr 28, 2015
- 9,398
- 1
- 84,820
- 8,389
Kaspersky detection was .gen, so probably They added a generic signature to detect similar attacks...Kaspersky, ESET and Avast! continue to detect it after your modification, which is in line with my theory: they have performed a Hexa detection on the malware.
So do K7, Avast,Eset...Kaspersky detection was .gen, so probably They added a generic signature to detect similar attacks...
- Apr 28, 2015
- 9,398
- 1
- 84,820
- 8,389
- Status
- Not open for further replies.
You may also like...
-
-
-
Malware News Emojis in PureRAT’s Code Point to AI-Generated Malware Campaign
- Started by Brownie2019
- Replies: 11
-
AVLab.pl Analysis of system protection against active online malware – July 2025
- Started by Adrian Ścibor
- Replies: 165