"He who knows, knows" ... This is the answer that a great guitarist gave me, when I asked him about the compas, one of the fundamental things of Music ... I say the same ... "He who knows, knows"
Danger TairikuOkami's Crippled Windows
- Thread starter TairikuOkami
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Last updated
- Dec 22, 2018
- Windows Edition
- Home
- Security updates
- Check for updates and Notify
- User Access Control
- Always notify
- Real-time security
- UltraDNS Threat Protection
Windows Defender Firewall
- Firewall security
- Microsoft Defender Firewall
- Periodic malware scanners
- Random (CureIt/FRST/KVRT/NPE)
- Malware sample testing
- I do not participate in malware testing
- Browser(s) and extensions
- Yandex Browser - https://yandex.com/support/browser/security
AdBlocker for Youtube (effectively removes annoying contents, ads, and banners from YouTube)
Cache Killer (clears the browser cache automatically on opening a new tab or refreshing a tab)
Cookie AutoDelete (auto-delete unused cookies from closed tabs while keeping the ones you want)
Context Menu Search (use the right-click menu to search for selected text in any search engines)
Decentraleyes (protects against tracking through "free", centralized, content delivery)
Dictionary Lookup (look up any word in an inline frame with a simple click)
h264ify (makes YouTube stream H.264 videos instead of VP8/VP9 videos)
I don't care about cookies (get rid of annoying cookie warnings from almost all websites)
IDN Safe (blocks internationalized domain names to prevent visiting probable fake sites)
Netcraft (blocks XSS attacks, phishing and suspicious sites)
Poper Blocker (blocks annoying popups and some cryptomining)
Privacy Badger (blocks trackers and WebRTC, not ADs generally)
Youtube Auto HD + FPS (Automatically set the videos' quality on YouTube)
- Maintenance tools
- Autoruns
Disc Cleanup
Driver Easy
Driver Store Explorer
Geek Uninstaller
Process Hacker Nightly
Windows Repair Toolbox
Wise Disk Cleaner
Wise Registry Cleaner
- File and Photo backup
- Copy/Paste - automatic backups deleted my files, twice, I will not fall for that again
- System recovery
- None - System Backup trashed my system, besides, I can reinstall everything within an hour anyway
- Computer specs
- http://steamcommunity.com/id/tairikuokami
risky configuration, but if you like it and you do not have any problems with the infections, then you have a
happiness
I would not risk it that way.
happiness
I would not risk it that way.
- Jan 16, 2017
- 1,470
- 13,500
- 2,379
Since only exe with a valid digital signatures is allowed to run, that should take care of like 99% of them.Have you thought of using SRP or anti exes?
In order to use SRP, I would have to allow scripts, Windows Event Log, etc, that is too much of a compromise.
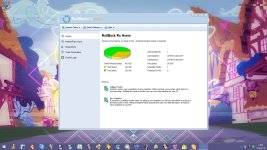
Currently testing RollBack Rx Home Edition, it seems pretty idiot proof, so that might be just what I need.
Still I do not get, where does it store snapshots. They say, that snapshots are magically hidden somewhere.
Where is the snapshot and what is the filename - Horizon DataSys Community Forum
Attachments
Last edited:
Go to snapshots choose Explore Snapshot and there you will see that they are loaded on C:
I am not sure if that is all correct because i have removed RB RX about a month now so i can't be sure
I am not sure if that is all correct because i have removed RB RX about a month now so i can't be sure
Explore will only mount them in VM. I need to know, where they are to see the size, since my partition is tiny, but I guess it will pop up eventually. Windows already refuses to upgrade, because ~50GB is minimum. I could not even install the last update at first, it cried out, that I do not a sufficient space (with 25 GB free). 
Where is the snapshot and what is the filename - Horizon DataSys Community Forum
Read the last answer, i think it answers your question.
Read the last answer, i think it answers your question.
You can adopt SRP and set SRP Default Security Level to Disallowed - this applies extended VBScript and CMD script protection. There are two easy solutions for running scripts with active SRP:Since only exe with a valid digital signatures is allowed to run, that should take care of like 99% of them.
In order to use SRP, I would have to allow scripts, Windows Event Log, etc, that is too much of a compromise.
Currently testing RollBack Rx Home Edition, it seems pretty idiot proof, so that might be just what I need.
Still I do not get, where does it store snapshots. They say, that snapshots are magically hidden somewhere.
Where is the snapshot and what is the filename - Horizon DataSys Community Forum
1. Copy all useful scripts to Program Files or Windows subfolder - those folders can be safely whitelisted in SRP.
or
2. Run the file manager (like Total Commander) as administrator for executing the scripts. This will bypass SRP.
.
That is not true that you are 99% safe using the EXE protection via valid digital signatures. The UAC setting ValidateAdminCodeSignatures=1, allows running any EXE that does not need to elevate. It also allows all UAC bypasses (not many on Windows 10). The protection is probably closer to 80%.
.
Anyway, If you use Windows 10 + Fortinet + RB RX + your tweaks + ValidateAdminCodeSignatures, and have no happy clicker habits, then you have a pretty much secure setup.
.
I would add only a pendrive or DVD external rescue system, to troubleshoot the event when your system disk will not start (broken partition).
- Apr 28, 2015
- 9,400
- 1
- 84,830
- 8,389
@TairikuOkami: You config will remain in Risky temporally until You enable OS File Reputation (SmartScreen), also consider to add full System Image Backup Solution to Your system.
Thanks for sharing Your config
Thanks for sharing Your config
That will never happen, since I would not like SWAT team knocking down my doors, MS is known to report everything and helped to arrest many people already.You config will remain in Risky temporally until You enable OS File Reputation (SmartScreen)
Anyway I reverted back to my original config, I got tired of running AV (hard to test other AVs then) and Rollback was taking too much space. So back to square 1.
You might say, that VM or a system imaging would help to test other AVs, but no, that is cheating. I need to know, how well it installs/uninstalls and if there are conflicts with previously installed AVs due to remains (Panda leaves such a mess, just like Zemana). I always like to do it the hard way, it is more fun and it teaches how to clean.
Attachments
Last edited:
TairikuOkami,
Everything is beautiful, everything is sparse.... without morbid Yandex, Sir... So your config are truly RISKY.
- because of it....
Everything is beautiful, everything is sparse.... without morbid Yandex, Sir... So your config are truly RISKY.
- because of it....
Just a little/big update:
Added: K9 Web Protection
Disabled some Windows drivers.
Since 1803, it is no longer possible to uninstall network protocols, MS said: Because we say so ... .
So I have disabled their drivers, plus a few drivers related to remote management/sharing, thanks MS.
I have Server/Workstation disabled, that should take care of the "Client for Microsoft Network" & "File and Printer Sharing".
Cannot uninstall protocols such as client for Microsoft networks
Added: K9 Web Protection
Disabled some Windows drivers.
Since 1803, it is no longer possible to uninstall network protocols, MS said: Because we say so ... .
So I have disabled their drivers, plus a few drivers related to remote management/sharing, thanks MS.
I have Server/Workstation disabled, that should take care of the "Client for Microsoft Network" & "File and Printer Sharing".
Cannot uninstall protocols such as client for Microsoft networks
Code:
rem Link-Layer Topology Discovery Responder / Default - 2
reg add "HKLM\System\CurrentControlSet\Services\rspndr" /v "Start" /t REG_DWORD /d "4" /f
rem Link-Layer Topology Discovery Mapper I/O Driver / Default - 2
reg add "HKLM\System\CurrentControlSet\Services\lltdio" /v "Start" /t REG_DWORD /d "4" /f
rem Microsoft LLDP Protocol Driver / Default - 2
reg add "HKLM\System\CurrentControlSet\Services\MsLldp" /v "Start" /t REG_DWORD /d "4" /f
rem Microsoft Virtual Network Adapter Enumerator / Default - 3
reg add "HKLM\System\CurrentControlSet\Services\NdisVirtualBus" /v "Start" /t REG_DWORD /d "4" /f
rem QoS for storage I/O traffic / Default - 2
reg add "HKLM\System\CurrentControlSet\Services\storqosflt" /v "Start" /t REG_DWORD /d "4" /f
rem QoS Multimeda Class Scheduler / Default - 2
reg add "HKLM\System\CurrentControlSet\Services\MMCSS" /v "Start" /t REG_DWORD /d "4" /f
rem QoS Packet Scheduler / Default - 1
reg add "HKLM\System\CurrentControlSet\Services\Psched" /v "Start" /t REG_DWORD /d "4" /f
rem Named pipe service trigger provider / Default - 1
rem https://msdn.microsoft.com/en-us/library/windows/desktop/aa365590(v=vs.85).aspx
reg add "HKLM\System\CurrentControlSet\Services\npsvctrig" /v "Start" /t REG_DWORD /d "4" /f
rem NetBIOS Interface / Default - 1
reg add "HKLM\System\CurrentControlSet\Services\NetBIOS" /v "Start" /t REG_DWORD /d "4" /f
rem NetBIOS over TCP/IP / Default - 1
reg add "HKLM\System\CurrentControlSet\Services\NetBT" /v "Start" /t REG_DWORD /d "4" /f
rem Remote Desktop Device Redirector Bus Driver / Default - 3
reg add "HKLM\System\CurrentControlSet\Services\rdpbus" /v "Start" /t REG_DWORD /d "4" /f
rem The framework for network mini-redirectors / Default - 1
rem https://docs.microsoft.com/en-us/windows-hardware/drivers/ifs/the-redirected-drive-buffering-subsystem
reg add "HKLM\System\CurrentControlSet\Services\rdbss" /v "Start" /t REG_DWORD /d "4" /f
rem A little bonus - Disable IPv6/LMHOSTS lookup/NetBIOS and Set DNS Servers
netsh int ipv6 isatap set state disabled
netsh int teredo set state disabled
netsh interface ipv6 6to4 set state state=disabled undoonstop=disabled
reg add "HKLM\System\CurrentControlSet\Services\Tcpip6\Parameters" /v "DisabledComponents" /t REG_DWORD /d "255" /f
wmic nicconfig where DHCPEnabled=TRUE call SetDNSServerSearchOrder ("1.1.1.1")
reg add "HKLM\System\CurrentControlSet\Services\NetBT\Parameters" /v "EnableLMHOSTS" /t REG_DWORD /d "0" /f
wmic nicconfig where TcpipNetbiosOptions=0 call SetTcpipNetbios 2
wmic nicconfig where TcpipNetbiosOptions=1 call SetTcpipNetbios 2Important changes to be made:
- Have Smartscreen turned on
- Backup files using either Macrium Reflect or Aomei Backupper
Smartscreen doesn't do anything like arrest people or any other fake news propaganda crap.
Things you could add to your config:
- Have Smartscreen turned on
- Backup files using either Macrium Reflect or Aomei Backupper
Smartscreen doesn't do anything like arrest people or any other fake news propaganda crap.
Things you could add to your config:
- OSArmor combined with VoodooShield
- Syshardener & UnChecky for Windows Firewall/OS Hardening & PUP aspects
- Sandboxie for web browser security/privacy
- PrivaZer for privacy cleanup ppr junk files
D
Deleted member 178
come on...you seriously believes that?That will never happen, since I would not like SWAT team knocking down my doors, MS is known to report everything and helped to arrest many people already.
I
illumination
It is amazing how many do believe such things.come on...you seriously believes that?
come on...you seriously believe that?
Yeah.
Don't buy that conspiracy theory.
I can assure you, MS is not interested in doing law enforcement activities on your machine. They don't make any money out of that. Yes, they will comply with law enforcement subpoenas and passively resist software piracy mostly for MS products... but that's about it.
@TairikuOkami
You need to remove similar extensions from your browser such as Cookie autodelete & I don't care about cookies. You can install uBO or BD Traffic light for added protection.
As for DNS, use the DNS server in your router and or use DNS query using Windows and switch to Quad9.
As for W10 telemetry, use donotspy10 or O&O Shutup 10 to do the job. Disable sihclient and similar( In task scheduler) if you want to disable Auto WU w/o user consent over metered connections. You can use WUMT wrapepr script to block WU and enable them when needed.
Macrium reflect has a freeware version for Image backup.
You need to remove similar extensions from your browser such as Cookie autodelete & I don't care about cookies. You can install uBO or BD Traffic light for added protection.
As for DNS, use the DNS server in your router and or use DNS query using Windows and switch to Quad9.
As for W10 telemetry, use donotspy10 or O&O Shutup 10 to do the job. Disable sihclient and similar( In task scheduler) if you want to disable Auto WU w/o user consent over metered connections. You can use WUMT wrapepr script to block WU and enable them when needed.
Macrium reflect has a freeware version for Image backup.
MS reported it on its own blog just this year, mostly for onedrive, but the same EULA applies to all services. But it was obvious before, since MS helped to arrest people dozen of times, it was all over the news, but I guess some people are only interested in security news.come on...you seriously believes that?
2004 - Police: Microsoft helped catch suspect
2014 - Microsoft alerts police to child porn (onedrive)
Cookie autodelete removes cookies. I don't care about cookies blocks cookie notices caused by EU laws.You need to remove similar extensions from your browser such as Cookie autodelete & I don't care about cookies.
You may add decentraleyes,HTTPS everywhere. & regarding Cookie autodelete & I don't care about cookies, it won't conflict. If you use adguard,you can enable I don't care about cookies in its filter & don't need d extension.
btw do you use yandex stable or beta?
btw do you use yandex stable or beta?
D
Deleted Member 3a5v73x
What criminal activities you are doing online to be worried about that?That will never happen, since I would not like SWAT team knocking down my doors, MS is known to report everything and helped to arrest many people already
Last edited by a moderator:
You may also like...
-
Poll Paid vs Free Antivirus in 2026: What are you using, and is it worth paying for?
- Started by Bot
- Replies: 96
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
-
Serious Discussion Orion Malware Cleaner (OMC) - By Trident
- Started by Trident
- Replies: 23