The WHHLight_Package_1000.exe was quarantined by F-Secure.
After reporting it to F-Secure, it got an safe verdict and was advised to restore it from quarantine.
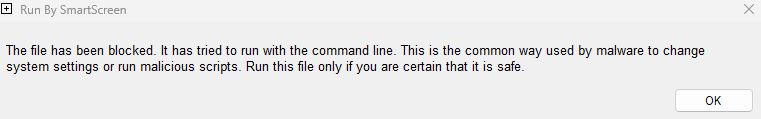
Running it now with SWH and WDAC enabled.
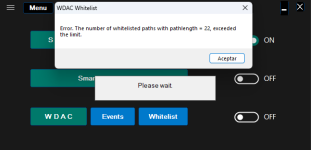
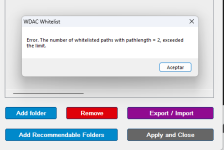
Got 2 WDAC EXE/DLL blocks:
Event[9]:
Event Id = 3077
Local Time: 2023/08/17 09:06:31
Attempted Path = \Device\HarddiskVolume3\Users\Gandalf\Downloads\Software\PatchMyPC\PatchMyPC.exe
Parent Process = \Device\HarddiskVolume3\Windows\explorer.exe
Policy Name = UserSpace Lock
Policy GUID = {a5ee6c14-b6ae-488c-8fc1-9ce316cc2461}
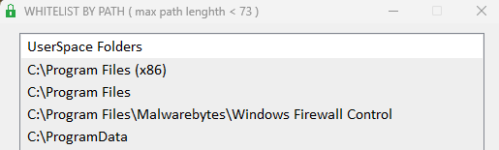
This one is solved by adding the folder Users\Gandalf\Downloads\Software to the Whitelist.
Event[0]:
Event Id = 3077
Local Time: 2023/08/17 09:36:39
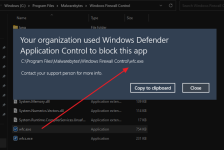
Attempted Path = \Device\HarddiskVolume3\Windows\System32\wbem\WMIC.exe
Parent Process = \Device\HarddiskVolume3\Program Files\WindowsApps\38002AlexanderFrangos.TwinkleTray_1.15.4.0_x64__m7qx9dzpwqaze\app\Twinkle Tray.exe
Policy Name = UserSpace Lock
Policy GUID = {a5ee6c14-b6ae-488c-8fc1-9ce316cc2461}
I don't know how to solve this one.
The program TwinkleTray uses WMIC.exe to control the brightness of my external monitor.
Any ideas?