ASR
Block executable content from email client and webmail
BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550
Block all Office applications from creating child processes
D4F940AB-401B-4EFC-AADC-AD5F3C50688A
Block Office applications from creating executable content
3B576869-A4EC-4529-8536-B80A7769E899
Block Office applications from injecting code into other processes
75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84
Block JavaScript or VBScript from launching downloaded executable content
D3E037E1-3EB8-44C8-A917-57927947596D
Block execution of potentially obfuscated scripts
5BEB7EFE-FD9A-4556-801D-275E5FFC04CC
Block Win32 API calls from Office macro
92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B
Block executable files from running unless they meet a prevalence, age, or trusted list criterion
01443614-CD74-433A-B99E-2ECDC07BFC25
Use advanced protection against ransomware
C1DB55AB-C21A-4637-BB3F-A12568109D35
Block credential stealing from the Windows local security authority subsystem (lsass.exe)
9E6C4E1F-7D60-472F-BA1A-A39EF669E4B2
Block process creations originating from PSExec and WMI commands
D1E49AAC-8F56-4280-B9BA-993A6D77406C
Block untrusted and unsigned processes that run from USB
B2B3F03D-6A65-4F7B-A9C7-1C7EF74A9BA4
Block Office communication application from creating child processes
26190899-1602-49E8-8B27-EB1D0A1CE869
Block Adobe Reader from creating child processes
7674BA52-37EB-4A4F-A9A1-F0F9A1619A2C
Block persistence through WMI event subscription
E6DB77E5-3DF2-4CF1-B95A-636979351E5B
Block process creations from Win32 system binaries:
1E99423B-41E0-4FE0-BAEA-1DBD9FA9C9F4
Block process creations originating from PSExec and other remote management tools
9E6B2D5F-9C79-4CB2-AFEA-8BDE36EAD7DD
Block Office applications from creating files in user profile paths
CA1F5E86-BBCE-4375-A5E0-44C6A9153ABA
Block execution of binaries from compressed and encrypted archives
BE1A3039-4BD6-4523-A7BC-4B8A0E0D452A
Block Office applications from creating child processes through OLE
9B5E5345-4B75-4B0F-8212-AC128AD5A033
Block code from running in PowerShell unless it's signed by a trusted publisher
0F3B97A3-2C43-4F31-8B46-9F9D80269B60
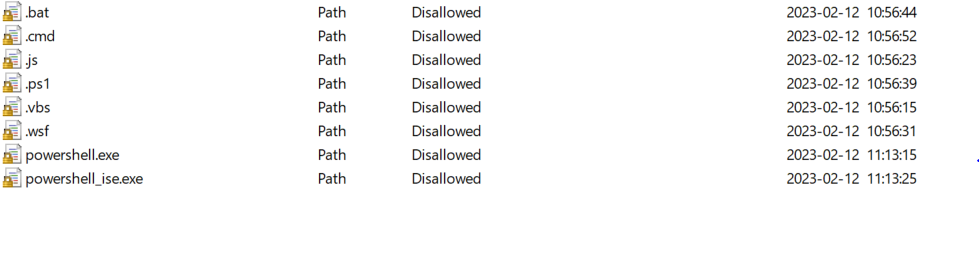
Block PowerShell entirely
9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2
Creditentials
Do not display network selection UI Enabled
Enumerate local users on domain-joined computers Disabled
Enumerate administrator accounts on elevation Disabled
Require trusted path for credential entry Enabled (Windows 11 install splash screen prevented me to do anything, so I disabled it)
Prevent the use of security questions for local accounts Enabled
Disable or enable software Secure Attention Sequence Disabled
Sign-in last interactive user automatically after a system-initiated restart Disabled
Interactive logon: Do not require CTRL+ALT+DEL Disabled (Disable will ask the CTRL+ALT+DEL)
Early Malware
Boot-Start Driver Initialization Policy Enabled
Choose the boot-start drivers that can be initialized: Good and unknown
Defender
Turn off Microsoft Defender Antivirus Disabled
Configure detection for potentially unwanted applications Enabled
Configure local setting override for reporting to Microsoft MAPS Disabled
Configure the ‘Block at First Sight’ feature Enabled
Join Microsoft MAPS Enabled
Send file samples when further analysis is required Enabled
Configure extended cloud check Enabled
Specify the extended cloud check time in seconds: 50
Select cloud protection level Enabled
Select cloud blocking level: High blocking level or Zero Tolerance
Turn off real-time protection Disabled
Turn on behavior monitoring Enabled
Scan all downloaded files and attachments Enabled
Monitor file and program activity on your computer Enabled
Turn on raw volume write notifications Enabled
Turn on process scanning whenever real-time protection is enabled Enabled
Define the maximum size of downloaded files and attachments to be scanned Enabled
Configure local setting override for turn on behavior monitoring Disabled
Configure local setting override for scanning all downloaded files and attachments Disabled
Configure local setting override for monitoring file and program activity on your computer Disabled
Configure local setting override to turn on real-time protection Disabled
Configure local setting override for monitoring for incoming and outgoing file activity Disabled
Configure monitoring for incoming and outgoing file and program activity Enabled (Both)
Check for the latest virus and spyware definitions before running a scheduled scan Enabled
Scan archive files Enabled
Scan packed executables Enabled
Scan removable drives Enabled
Turn on e-mail scanning Enabled
Turn on heuristics Enabled
Configure detection for potentially unwanted application Enabled
Configure Windows Defender smartscreen Enabled
Bitlocker
BitLocker Drive Encryption
Choose drive encryption method and cipher strength
Select the encryption method for operating system drives: XTS AES 256-bit
Select the encryption method for fixed data drives: XTS AES 256-bit
Select the encryption method for removable data drives: AES-CBC 256-bit
Disable new DMA devices when this computer is locked Enabled
Prevent memory overwrite on restart Disabled
Fixed Data Drives
Choose how BitLocker-protected removable drives can be recovered Enabled
Allow data recovery agent
Allow 48-digit recovery password
Allow 256-bit recovery key
Save BitLocker recovery information to AD DS for operating system drives
Backup recovery passwords and key packages
Configure use of passwords for fixed data drives Enabled
Allow password complexity
Minimum password length for fixed data drive: 14
Operating System Drives
Allow devices compliant with InstantGo or HSTI to opt out of pre-boot PIN. Disabled
Allow Secure Boot for integrity validation Enabled
Choose how BitLocker-protected operating system drives can be recovered Enabled
Allow data recovery agent
Allow 48-digit recovery password
Allow 256-bit recovery key
Save BitLocker recovery information to AD DS for operating system drives
Store recovery passwords and key packages
Configure minimum PIN length for startup Enabled
Minimum characters: 14
Configure use of passwords for operating system drives Enabled
Allow password complexity
Minimum password length for operating system drive: 14
Disallow standard users from changing the PIN or password Enabled
Require additional authentication at startup Enabled
UNCHECKED Allow BitLocker without a compatible TPM (requires a password or a startup key on a USB flash drive)
Allow TPM
Allow startup PIN with TPM
Allow startup key with TPM
Allow startup key and PIN with TPM
Reset platform validation data after BitLocker recovery Enabled
Removable Data Drives
Choose how BitLocker-protected removable drives can be recovered Enabled
Allow data recovery agent
Allow 48-digit recovery password
Allow 256-bit recovery key
Omit recovery options from the BitLocker setup wizard
Save BitLocker recovery information to AD DS for operating system drives
Backup recovery passwords and key packages
Do not enable BitLocker until recovery information is stored to AD DS for operating system drives
Configure use of passwords for fixed data drives Enabled
Allow password complexity
Minimum password length for fixed data drive: 14
Control use of BitLocker on removable drives Enabled
Allow users to apply BitLocker protection on removable data drives
Allow users to suspend and decrypt BitLocker on removable data drives
Other
Prevent access to 16-bit applications Enabled
Block executable content from email client and webmail
BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550
Block all Office applications from creating child processes
D4F940AB-401B-4EFC-AADC-AD5F3C50688A
Block Office applications from creating executable content
3B576869-A4EC-4529-8536-B80A7769E899
Block Office applications from injecting code into other processes
75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84
Block JavaScript or VBScript from launching downloaded executable content
D3E037E1-3EB8-44C8-A917-57927947596D
Block execution of potentially obfuscated scripts
5BEB7EFE-FD9A-4556-801D-275E5FFC04CC
Block Win32 API calls from Office macro
92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B
Block executable files from running unless they meet a prevalence, age, or trusted list criterion
01443614-CD74-433A-B99E-2ECDC07BFC25
Use advanced protection against ransomware
C1DB55AB-C21A-4637-BB3F-A12568109D35
Block credential stealing from the Windows local security authority subsystem (lsass.exe)
9E6C4E1F-7D60-472F-BA1A-A39EF669E4B2
Block process creations originating from PSExec and WMI commands
D1E49AAC-8F56-4280-B9BA-993A6D77406C
Block untrusted and unsigned processes that run from USB
B2B3F03D-6A65-4F7B-A9C7-1C7EF74A9BA4
Block Office communication application from creating child processes
26190899-1602-49E8-8B27-EB1D0A1CE869
Block Adobe Reader from creating child processes
7674BA52-37EB-4A4F-A9A1-F0F9A1619A2C
Block persistence through WMI event subscription
E6DB77E5-3DF2-4CF1-B95A-636979351E5B
Block process creations from Win32 system binaries:
1E99423B-41E0-4FE0-BAEA-1DBD9FA9C9F4
Block process creations originating from PSExec and other remote management tools
9E6B2D5F-9C79-4CB2-AFEA-8BDE36EAD7DD
Block Office applications from creating files in user profile paths
CA1F5E86-BBCE-4375-A5E0-44C6A9153ABA
Block execution of binaries from compressed and encrypted archives
BE1A3039-4BD6-4523-A7BC-4B8A0E0D452A
Block Office applications from creating child processes through OLE
9B5E5345-4B75-4B0F-8212-AC128AD5A033
Block code from running in PowerShell unless it's signed by a trusted publisher
0F3B97A3-2C43-4F31-8B46-9F9D80269B60
Block PowerShell entirely
9e6c4e1f-7d60-472f-ba1a-a39ef669e4b2
Creditentials
Do not display network selection UI Enabled
Enumerate local users on domain-joined computers Disabled
Enumerate administrator accounts on elevation Disabled
Require trusted path for credential entry Enabled (Windows 11 install splash screen prevented me to do anything, so I disabled it)
Prevent the use of security questions for local accounts Enabled
Disable or enable software Secure Attention Sequence Disabled
Sign-in last interactive user automatically after a system-initiated restart Disabled
Interactive logon: Do not require CTRL+ALT+DEL Disabled (Disable will ask the CTRL+ALT+DEL)
Early Malware
Boot-Start Driver Initialization Policy Enabled
Choose the boot-start drivers that can be initialized: Good and unknown
Defender
Turn off Microsoft Defender Antivirus Disabled
Configure detection for potentially unwanted applications Enabled
Configure local setting override for reporting to Microsoft MAPS Disabled
Configure the ‘Block at First Sight’ feature Enabled
Join Microsoft MAPS Enabled
Send file samples when further analysis is required Enabled
Configure extended cloud check Enabled
Specify the extended cloud check time in seconds: 50
Select cloud protection level Enabled
Select cloud blocking level: High blocking level or Zero Tolerance
Turn off real-time protection Disabled
Turn on behavior monitoring Enabled
Scan all downloaded files and attachments Enabled
Monitor file and program activity on your computer Enabled
Turn on raw volume write notifications Enabled
Turn on process scanning whenever real-time protection is enabled Enabled
Define the maximum size of downloaded files and attachments to be scanned Enabled
Configure local setting override for turn on behavior monitoring Disabled
Configure local setting override for scanning all downloaded files and attachments Disabled
Configure local setting override for monitoring file and program activity on your computer Disabled
Configure local setting override to turn on real-time protection Disabled
Configure local setting override for monitoring for incoming and outgoing file activity Disabled
Configure monitoring for incoming and outgoing file and program activity Enabled (Both)
Check for the latest virus and spyware definitions before running a scheduled scan Enabled
Scan archive files Enabled
Scan packed executables Enabled
Scan removable drives Enabled
Turn on e-mail scanning Enabled
Turn on heuristics Enabled
Configure detection for potentially unwanted application Enabled
Configure Windows Defender smartscreen Enabled
Bitlocker
BitLocker Drive Encryption
Choose drive encryption method and cipher strength
Select the encryption method for operating system drives: XTS AES 256-bit
Select the encryption method for fixed data drives: XTS AES 256-bit
Select the encryption method for removable data drives: AES-CBC 256-bit
Disable new DMA devices when this computer is locked Enabled
Prevent memory overwrite on restart Disabled
Fixed Data Drives
Choose how BitLocker-protected removable drives can be recovered Enabled
Allow data recovery agent
Allow 48-digit recovery password
Allow 256-bit recovery key
Save BitLocker recovery information to AD DS for operating system drives
Backup recovery passwords and key packages
Configure use of passwords for fixed data drives Enabled
Allow password complexity
Minimum password length for fixed data drive: 14
Operating System Drives
Allow devices compliant with InstantGo or HSTI to opt out of pre-boot PIN. Disabled
Allow Secure Boot for integrity validation Enabled
Choose how BitLocker-protected operating system drives can be recovered Enabled
Allow data recovery agent
Allow 48-digit recovery password
Allow 256-bit recovery key
Save BitLocker recovery information to AD DS for operating system drives
Store recovery passwords and key packages
Configure minimum PIN length for startup Enabled
Minimum characters: 14
Configure use of passwords for operating system drives Enabled
Allow password complexity
Minimum password length for operating system drive: 14
Disallow standard users from changing the PIN or password Enabled
Require additional authentication at startup Enabled
UNCHECKED Allow BitLocker without a compatible TPM (requires a password or a startup key on a USB flash drive)
Allow TPM
Allow startup PIN with TPM
Allow startup key with TPM
Allow startup key and PIN with TPM
Reset platform validation data after BitLocker recovery Enabled
Removable Data Drives
Choose how BitLocker-protected removable drives can be recovered Enabled
Allow data recovery agent
Allow 48-digit recovery password
Allow 256-bit recovery key
Omit recovery options from the BitLocker setup wizard
Save BitLocker recovery information to AD DS for operating system drives
Backup recovery passwords and key packages
Do not enable BitLocker until recovery information is stored to AD DS for operating system drives
Configure use of passwords for fixed data drives Enabled
Allow password complexity
Minimum password length for fixed data drive: 14
Control use of BitLocker on removable drives Enabled
Allow users to apply BitLocker protection on removable data drives
Allow users to suspend and decrypt BitLocker on removable data drives
Other
Prevent access to 16-bit applications Enabled
Last edited:
