I have used it for some time now, Man I love itI see what you mean now... yeah, anything outside the built in Program Files folders is going to be scrutinized much harder than the built in / environmental variable ones. But for example, if there was a reg edit that allowed you to change the built in path, VS would automatically assume that these folders on the D drive are your program file folders.
BTW, I figured out why the AirVPN command lines are being blocked... it is as easy fix. It will be included in the next release. AirVPN is pretty cool btw, I have never tried it before.
VoodooShield discussion
- Thread starter Evjl's Rain
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
OP, try switching to PeaZip, VS seems to love it, and more attention is paid to security than with 7zip, try it you will see what I mean:Cool, thank you, I will download the video and watch it after dinner, thank you!
PeaZip | Free archiver, free RAR TAR ZIP files utility
@danb
Commission some VS wallpapers ? It's great advertisement and your users (me included) would sport them C'mon man
C'mon man 
Commission some VS wallpapers ? It's great advertisement and your users (me included) would sport them
Can PeaZip do that?
Mais naturellement! It includes most compression engines, you'd be hard put to find one it doesn't know about
BACK ON TOPIC!
I believe it can, and here's more, if your interested: FAQ | How to Zip, Unzip, extract Rar, manage encrypted filesOT: One of the things I like about 7zip is its ability to open *exe files. For example...
View attachment 169464
Can PeaZip do that?
disabled BitDefender and install went fine. No issues with 4.06 on Wind 10 64bt
under "Advanced Settings" if I disable everything except "anti-exploit protection", does that mean VS will not be able to take advantage of "Basic" settings like "automatically allow white listed items voodooAI cloud and auto allow approved command lines and items that match a digital signature"? Thanks
under "Advanced Settings" if I disable everything except "anti-exploit protection", does that mean VS will not be able to take advantage of "Basic" settings like "automatically allow white listed items voodooAI cloud and auto allow approved command lines and items that match a digital signature"? Thanks
Likewise. I always install outside the C: drive.a) Win 8.1-64bit
b) No tweaks. Many installers allow you to prescribe the installation path. I just replace "C" with "D" for the most part. For programs that don't allow users to define the installation path (ex VS) I just live with that.
If it matters most of my Windows profile folders (Documents, Downloads, Videos, Pictures, etc.) reside on "E drive". Again that is done simply by changing the "Location" setting under folder properties.
I can't be the only one putting my program installations outside the OS partition. Doing so simplifies imaging backups.
Take full control over your clipboard history
Yeah, the VPN's I have used in the past were all super slow, but AirVPN is great... I have been playing with it a little more and it really is cool.I have used it for some time now, Man I love it
Yeah, thank you for the idea... we will have to do that. I just found a new graphic designer who is super talented, so let's see what he comes up with@danb
Commission some VS wallpapers ? It's great advertisement and your users (me included) would sport themC'mon man

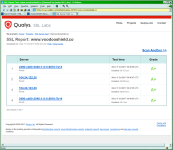
Thank you, I appreciate that! I am not a web security expert, so I cannot tell you how much difference it makes, but either way, since VS is a security company, we should make sure everything is secure. I have a few more adjustments to make, but we will end up with somewhere between a B+ and an A+ rating for the various test sites. See, when you lock things down too tight, it tends to break stuff on the site, so I am not sure there is a way to secure absolutely everything on the site... but will will make it as secure as possible.Way to go Dan!! This is the Qualys SSL Test:
View attachment 169466
I wish a few other sites would make the same effort
BTW, I keep calling Malware Blocker MM... sorry about that MB
It is definitely best to leave most of the settings as their default values, and change only what needs to be changed. VS's settings interact with each other, and if you change tons of settings, it is difficult to say what will happen. Then again, you can experiment with it and see what works for you. Thank you!disabled BitDefender and install went fine. No issues with 4.06 on Wind 10 64bt
under "Advanced Settings" if I disable everything except "anti-exploit protection", does that mean VS will not be able to take advantage of "Basic" settings like "automatically allow white listed items voodooAI cloud and auto allow approved command lines and items that match a digital signature"? Thanks
Hmmm, this means that for some reason VS cannot communicate with the internet. Do you have a firewall that is blocking VS? What happens if you try to execute a non-whitelisted file when this happens? Do you get the same message? Thank you!View attachment 169491 When I drag and drop a file to be scanned with VS, I get th old internet connection popup now.
I studied your video and reproduced EVERYTHING on a test system. To make a long story short, the only safe way a compression utility is going to work properly with VS is if it is installed in the c:\program files or c:\program files (x86) folders. There is a small chance that I might be able to change this in the future, but it would add a lot of extra code, and might present an opportunity for a bypass if it is not implemented correctly. From a security perspective, I am a firm believer that applications need to be installed in the program file folders (which are Windows protected folders), and user data belongs in the user space, and so on. Thank you!OT: One of the things I like about 7zip is its ability to open *exe files. For example...
View attachment 169464
Can PeaZip do that?
Here is VS 4.07b. All of the command line issues should be completely fixed.
I think we are getting close, but if I have overlooked a bug that one of you guys posted on here, please let me know, thank you!
www.voodooshield.co/Download/InstallVoodooShield407beta.exe
I think we are getting close, but if I have overlooked a bug that one of you guys posted on here, please let me know, thank you!
www.voodooshield.co/Download/InstallVoodooShield407beta.exe
I studied your video and reproduced EVERYTHING on a test system. To make a long story short, the only safe way a compression utility is going to work properly with VS is if it is installed in the c:\program files or c:\program files (x86) folders. There is a small chance that I might be able to change this in the future, but it would add a lot of extra code, and might present an opportunity for a bypass if it is not implemented correctly. From a security perspective, I am a firm believer that applications need to be installed in the program file folders (which are Windows protected folders), and user data belongs in the user space, and so on. Thank you!
For clarification, this goes beyond compression utilities. Basically, any program I have on D partition is affected (ex. Potplayer, NitroPro, Notepad++ and so on). So launching PDFs, videos, graphics files, etc., from Chrome (or my search utility, Everything) results in a notification. I tried Custom Folders and marked the D partition Program Files/Program Files (x86) folders to match those on C partition, but there was no change in notification behavior. It does seem odd though that double-clicking a zip file from Windows Explorer launches 7zip from D partition without a notification, but launching that same file through a program like Chrome (which does reside on C partition) gets flagged.
Thanks for looking into this Dan. I guess I'll have to live with that for now.
Cool, thank you. Yeah, I totally get what you are saying, and if there was a way that I could fix this safely, then I wouldFor clarification, this goes beyond compression utilities. Basically, any program I have on D partition is affected (ex. Potplayer, NitroPro, Notepad++ and so on). So launching PDFs, videos, graphics files, etc., from Chrome (or my search utility, Everything) results in a notification. I tried Custom Folders and marked the D partition Program Files/Program Files (x86) folders to match those on C partition, but there was no change in notification behavior. It does seem odd though that double-clicking a zip file from Windows Explorer launches 7zip from D partition without a notification, but launching that same file through a program like Chrome (which does reside on C partition) gets flagged.
Thanks for looking into this Dan. I guess I'll have to live with that for now.
The real issue is when a parent executable is trying to open a child executable, especially when the parent executable is a vulnerable web app. That is... if the parent app is simply trying to open a text file to edit it, there is not an issue. For example, VS will allow powershell to edit a non-whitelisted script, but it will not allow it to execute the non-whitelisted script.
This is why in your last Chrome example from above... Windows Explorer will launch 7 zip, and this is because it is whitelisted. But when you have a risky executable web app like Chrome trying to open a child executable, you have to be very careful, otherwise, the end user will end up in tears, as CS would say.
One very simple quick and dirty test that I always perform on VS is to open Internet Explorer... then go to File | Open | Browse | Change the file filter at the bottom right from web documents to all files | then browse to the Windows\System32 folder, and try to open an executable. I usually use cleanmgr.exe, but you can use most all of them. Anyway, after a couple of Internet Explorer prompts, VS will block the file. If VS did not block this file, I would be deeply concerned.
But yeah, blocks can be a pain, but the whole goal of VS is to provide "Absolute" security, while minimizing the dangerous affirmative user prompt as much as possible, and remaining user friendly. But if there is ever a question, the damn thing needs to be blocked.
As we all know, in cyber security, there is a balance between security and usability / convenience. Well, for the most part this is true... VS blocks a hell of a lot of stuff that some PIA products miss. But in general this is true.
Years ago, before I was self employed, I used to work for Lucent Technologies... and everyone had a saying there. "Do what you can afford."
Some cyber security companies actually believe that they can create a product that is totally silent to the end user, and still block every single attack... like it is FM (freakin magic).
And then others pretty much just block everything and call it a day.
There needs to be a balance. The security industry has a strong tendency to blame the user for not being able to utilize their software properly so that they are sufficiently protected. This is absolutely absurd. If, as a software company, you cannot produce software that 50% (guessing on the % from my experiences) or so of the target user base / market does not understand, then you either designed a crappy product, or you are in the wrong business.
End users are not stupid... they just need user friendly security software. For example, teenagers understand social media apps better than any security dev ever will, but yet, somehow we are unable to understand why they are not able to properly use security products.
Sorry for the rambling... all of these thoughts have been on my mind for a while now... along with many, many more
Last edited:
- Status
- Not open for further replies.
You may also like...
-
Security News ZDI: The December 2025 Security Update Review
- Started by Gandalf_The_Grey
- Replies: 4
-
New Update KB5058499 optional update finally makes Windows 11 24H2 stable for gaming
- Started by Gandalf_The_Grey
- Replies: 8
-
App Review Siyano Antivirus Total Security 2025
- Started by Shadowra
- Replies: 69
-
Advice Request Help: Comodo 2025 - cmdguard.sys - boot fail with newer Nvidia drivers
- Started by Something-x2
- Replies: 33
-
Persistant MDM enrollment/Enterprise management/Autopilot on my personal desktop
- Started by frostyfruits43
- Replies: 3