I agree with you on this. which is why I consider Windows Defender as only a secondary line of defense against malware.Windows Defender protection against scripts is poor by default, so is not stopping anything unless it's flagged as known malware.
Advice Request Windows Defender disabled by malware
- Thread starter Templarware
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
- Aug 17, 2014
- 12,736
- 123,873
- 8,399
I found this thread on Reddit, where a user is claiming that Windows Defender can be easily disabled by malware and even trusted applications.
Thoughts?
My first doubt is the source... there we can find a lot of threads where people complaining about free AVs or even paid AV.
Everyone should always searching for certain information on different places on the web!
To be more on topic, I trust more what is said by real experts (working for AV companies) than to believe what is reported by average users.
Here in the forum, MD users already knows to increase protection against malicious scripts by using Simple Windows Hardening:

New Update - Simple Windows Hardening
Post updated in September 2024. SWH works with Windows 10 and 11 (all versions including 24H2) SWH ver. 2.1.1.1 - July 2023 (added support for Windows 11 ver. 22H2) https://github.com/AndyFul/Hard_Configurator/raw/master/Simple%20Windows%20Hardening/SimpleWindowsHardening_2111.zip SWH ver...
 malwaretips.com
malwaretips.com
Seems you misunderstand how this has been abused in the past, which forced Microsoft hand with Anti-Tamper (which is still useless to an extent), Windows Defender can indeed be easily disabled.
Is pretty obvious the payload is only downloaded after disabling WD, the script that disables WD itself is not supposed to be detected, nor it is the real malware.
That is not a contradiction. The script itself is malware and needs to evade detection by Defender before it can disable Defender.
While reading this thread I was reminded of Iobit
I thought the fake Iobit malware disabled Defender but no. I thought wrong. It just added itself to the exclusions
I thought the fake Iobit malware disabled Defender but no. I thought wrong. It just added itself to the exclusions
You should not say this. It is clear that your knowledge about the current Defender's anti-script protection requires the update.Windows Defender protection against scripts is poor by default, so is not stopping anything unless it's flagged as known malware.
Anyway, it is true that any popular Home AV on default settings has only mediocre anti-script protection.
Microsoft knows better if it is useless or not on the basis of successful attacks in the wild. It can be probably sufficient for now, but far from being a comprehensive solution - still, the attack surface is too big. Some other AVs (like Kaspersky) have stronger anti-tampering (the AV services cannot be disabled even with TrustedInstaller privileges).Tamper Protection is useless cause you can still disable WD in the current session (it won't turn back on, already tested), only after a restart that WD is back on (and only if not corrupted by malware already), and by then is too late.
You are right that the method of the attack from the OP is clearly a kind of vulnerability. It could be used in the wild as a primary infection vector (sometimes even successfully). Fortunately, it has also many drawbacks as the primary infection vector so it is very unpopular despite the fact that it is known for many years.Microsoft had to go as far as removing regedit entries for WD, cause it was that easy to bypass Tamper Protection, and it still is unfortunately.
Do you know any example of such an attack in the wild? I know only the examples where this method was used by the malware as one of many post-infection actions (not primary infection vector).
Furthermore, this method can be easily detected by behavior-based modules. If it is not for now (I do not know) then this would strongly suggest that it is not used in the wild as a primary infection vector (or used very rarely).
Last edited:
Let's look at two methods of theft:

One example of such prevention would be installing the weapon detector and do not allow entering people with weapons. This would be analogous to use script blocking, SmartScreen, etc.
The situation is different when professional criminals want to attack the house with strong protection to get something very precious (worth killing). They can use another strategy:
Sneak into the neighbor's house which is not protected so well, and kill the host. Observe the target house, gather information, concentrate more people and more weapons. Use the weak point in the security to attack the target house at a suitable moment.
This method is analogous to the lateral movement in Enterprises.
- Sneak into the house with weapons, kill the host, and steal what you want.
- Sneak into the house, avoid the family members, and steal what you want.
One example of such prevention would be installing the weapon detector and do not allow entering people with weapons. This would be analogous to use script blocking, SmartScreen, etc.
The situation is different when professional criminals want to attack the house with strong protection to get something very precious (worth killing). They can use another strategy:
Sneak into the neighbor's house which is not protected so well, and kill the host. Observe the target house, gather information, concentrate more people and more weapons. Use the weak point in the security to attack the target house at a suitable moment.
This method is analogous to the lateral movement in Enterprises.
Last edited:
Hi Andy,It is clear that your knowledge about the current Defender's anti-script protection requires the update.
Anyway, it is true that any popular Home AV on default settings has only mediocre anti-script protection.
isn't Defender's script protection only available to Enterprises via the Attack Surface Reduction (ASR) component? Also if I'm not mistaken, many threats will obfuscate the script sent in a .zip file that often evades AV. Sodinokibi Ransomeware, for example, does this.
Script protection via ASR rules and AMSI behavior-based detections (also post-execution detections) are available in all Windows editions.Hi Andy,
isn't Defender's script protection only available to Enterprises via the Attack Surface Reduction (ASR) component? Also if I'm not mistaken, many threats will obfuscate the script sent in a .zip file that often evades AV. Sodinokibi Ransomeware, for example, does this.
Because this thread was rather speculative, I created the POC. Unfortunately (but fortunately for users), Microsoft recently patched most of UAC bypasses on Windows 10 (also fodhelper and cleanmgr), so I could not prepare the POC with UAC bypass. If one knows a working UAC bypass then please send me one and then I will create the new POC. I am not sure if the modified POCmight work because UAC bypass can make it more suspicious and can trigger Defender actions.
The POC should be downloaded from email or URL, unpacked, and executed. The user has to allow elevation. It fully disables Defender on default settings and runs payload which is hidden in a password-protected archive (password is hardcoded). In my POC the payload file is named pld.exe (renamed powershell.exe). Defender cannot check this payload on access and the payload is run after deactivating Defender.
In the POC folder, the Defender Control is included (dc.exe file with hidden attribute), so one can easily enable Defender.
Please let me know If someone from MalwareHub wants to try this POC. After few days I will submit it to Microsoft.
The POC should be downloaded from email or URL, unpacked, and executed. The user has to allow elevation. It fully disables Defender on default settings and runs payload which is hidden in a password-protected archive (password is hardcoded). In my POC the payload file is named pld.exe (renamed powershell.exe). Defender cannot check this payload on access and the payload is run after deactivating Defender.
In the POC folder, the Defender Control is included (dc.exe file with hidden attribute), so one can easily enable Defender.
Please let me know If someone from MalwareHub wants to try this POC. After few days I will submit it to Microsoft.
Last edited:
Don't understand why they not adding something like this.
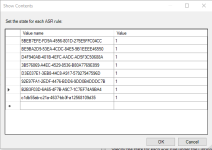
You can take a look here and here if you are wanting to use powershell to enable ASR rules for Windows 10 Home instead of Andy's tool. He just makes it a lot easier.Hi Andy,
isn't Defender's script protection only available to Enterprises via the Attack Surface Reduction (ASR) component? Also if I'm not mistaken, many threats will obfuscate the script sent in a .zip file that often evades AV. Sodinokibi Ransomeware, for example, does this.
L
Local Host
I do not require any update on Windows Defender script protection, if you relying on AMSI you already lost.You should not say this. It is clear that your knowledge about the current Defender's anti-script protection requires the update.
Anyway, it is true that any popular Home AV on default settings has only mediocre anti-script protection.
Microsoft knows better if it is useless or not on the basis of successful attacks in the wild. It can be probably sufficient for now, but far from being a comprehensive solution - still, the attack surface is too big. Some other AVs (like Kaspersky) have stronger anti-tampering (the AV services cannot be disabled even with TrustedInstaller privileges).
You are right that the method of the attack from the OP is clearly a kind of vulnerability. It could be used in the wild as a primary infection vector (sometimes even successfully). Fortunately, it has also many drawbacks as the primary infection vector so it is very unpopular despite the fact that it is known for many years.
Do you know any example of such an attack in the wild? I know only the examples where this method was used by the malware as one of many post-infection actions (not primary infection vector).
Furthermore, this method can be easily detected by behavior-based modules. If it is not for now (I do not know) then this would strongly suggest that it is not used in the wild as a primary infection vector (or used very rarely).
Crippling Windows Defender is pretty much a basic feature most malware has nowadays, considering it comes pre-installed with Windows 10, so it is more popular than you believe.
Most malware targeted at Home Users is not hidden, nor it needs to, they simply wanna do as much damage as possible.Let's look at two methods of theft:
The first method is very noisy, unpredictable, and very unpopular among professional thieves. The same is true for the method from the OP (as the primary infection vector). Although the first method is possible, most people do not use additional protection to prevent it.
- Sneak into the house with weapons, kill the host, and steal what you want.
- Sneak into the house, avoid the family members, and steal what you want.
One example of such prevention would be installing the weapon detector and do not allow entering people with weapons. This would be analogous to use script blocking, SmartScreen, etc.
The situation is different when professional criminals want to attack the house with strong protection to get something very precious (worth killing). They can use another strategy:
Sneak into the neighbor's house which is not protected so well, and kill the host. Observe the target house, gather information, concentrate more people and more weapons. Use the weak point in the security to attack the target house at a suitable moment.
This method is analogous to the lateral movement in Enterprises.
@Local Host,
I hope that your statement:
"Windows Defender protection against scripts is poor by default, so is not stopping anything unless it's flagged as known malware."
was a simple mistake.
No offense. You should be more cautious when posting about something you do not like.
I hope that your statement:
"Windows Defender protection against scripts is poor by default, so is not stopping anything unless it's flagged as known malware."
was a simple mistake.
No offense. You should be more cautious when posting about something you do not like.
The way I see it, Windows Defender is the most popular/used in the world, due to being built in, so not only is more susceptible AV crippling attacks but Windows crippling attacks as well. Having the best prevention and tempering protection is really a must.
Last edited:
Which better anti-script solution is applied in popular Home AVs?I do not require any update on Windows Defender script protection, if you relying on AMSI you already lost.
Yes, I hope that Microsoft remembers about it. But for now, it is doing pretty well:The way I see it, Windows Defender is the most popular/used in the world, due to being built in, so not only is more susceptible AV crippling attacks but Windows crippling attacks as well. Having the best prevention and tempering protection is really a must.

The best Home AV protection 2019-2020
Real-World tests include fresh web-originated samples. Malware Protection tests include older samples (several days old) usually delivered via USB drives or network drives. Real-World 2019-2020: SE Labs, AV-Comparatives, AV-Test (7659 samples in 24 tests) -------------------Missed samples...
 malwaretips.com
malwaretips.com
Of course, Defender has its own cons not related to pure protection.
The AV testing Labs do not support your claims.Crippling Windows Defender is pretty much a basic feature most malware has nowadays, considering it comes pre-installed with Windows 10, so it is more popular than you believe.
Defender (default settings) seems to be as effective as most other Home AVs (default settings) and the chances of infection are not great.

How big are your chances to be infected?
How big are your chances to be infected? My idea is simple. First I will gather the data from 2 last years about the samples missed by popular AVs and compare this to the total number of samples. Next, I will calculate the chances to be infected in the next 10 years, assuming that the user can...
 malwaretips.com
malwaretips.com
Of course, Defender anti-tampering is weaker compared to many AVs. This could be exploited by malc0ders, If they want.
Last edited:
I can already hear people complaining: I am installing 3rd party AV and MS does not want to let me, arghhh! Majority of users do not care about security, extra popup = bloatware.Don't understand why they not adding something like this.

Microsoft is now showing a popup asking users to try Edge when they try to install third-party browsers
Since the launch of Microsoft Edge, the company has been trying to get users to use the browser instead of switching to third-party counterparts. However, Microsoft hasn’t been successful in doing so and the market share numbers are the proof of that. However, it looks like the company is...
 mspoweruser.com
mspoweruser.com
Thanks Andy,Script protection via ASR rules and AMSI behavior-based detections (also post-execution detections) are available in all Windows editions.
good grief, I should have known this
L
Local Host
In Home AVs, you better off relying on Behaviour Blockers like System Watcher.Which better anti-script solution is applied in popular Home AVs?
I don't even need to go far to see both Kaspersky and WD in action on the Malware Hub, which confirms how poor WD is against scripts even with your configuration, in comparison to Kaspersky.
We even had a recent example here, Q&A - Drive-by downloads: Can you get malware just from visiting a website?
Kaspersky blocked the custom script I wrote for testing that, while WD didn't even flinch as I expected, so much for that superior script protection you rely so much on.
AMSI is pretty basic and it won't detect a good chunk of scripts, there's a good reason AMSI is complemented by Windows Defender ATP monitoring in the Enterprise, in the case of Kaspersky they have Adaptive Anomaly Control.
Last edited:
You may also like...
-
New Update Microsoft removing Defender Application Guard from Office
- Started by Parkinsond
- Replies: 1
-
Help Needed: Suspicious Activity & Possible Malware on Windows 10 PC
- Started by Thomas Ellias
- Replies: 4
-
-
Malware News New Multi-Stage Windows Malware Disables Microsoft Defender Before Dropping Malicious Payloads
- Started by Brownie2019
- Replies: 6