Windows Defender Impacts
One of the key reasons making Windows Defender a suitable choice is its cost effectiveness. Since it comes built into Windows, making it a suitable option for individual users and businesses alike who might not have the budget for third-party solutions.
Its user-friendly interface lets easy navigation, which makes it accessible even for non-technical users. Moreover, you don’t need to install and hassle with updates due to its integration into the Windows operating system.
User experience shows that Windows Defender impacts very lightly on system’s performance compared to several third-party applications. This minimal footprint allows users to work or game without noticeable slowdowns.
However, with its pros must come cons. While Windows Defender is effective against common threats, it may lag behind in detecting complex cyber-attacks, particularly those that utilize zero-day vulnerabilities or advanced evasion techniques.
Practical Advice
Free antivirus programs are ideal for low-risk users and secondary devices. Basic protection against common threats, with some offering real-time scanning and web browser security. On the other hand, paid premium antivirus software are recommended for users with higher risk, such as those storing sensitive information and running small businesses.

Free Antivirus Vs Paid Antivirus - Do You Really Need To Pay In 2026? - Techtroduce
Free antivirus vs paid antivirus in 2026-do you really need to pay? Covering features, Windows Defender impacts, myths, and practical security advice.www.techtroduce.com
New threads
This page contains the latest threads that were created in our community.
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Malware Hidden in Pirated Games Infects 400,000 Devices
- Parkinsond
- Security News
- Replies: 12
A new strain of Windows-based malware has been circulating through pirated PC games and may have infected over 400,000 devices.
Researchers at cybersecurity vendor Cyderes are warning about the threat, which has been hiding inside cracked games and modified game installers for franchises including Far Cry, Need for Speed, FIFA, and Assassin’s Creed.
The telemetry tracker shows the malware is usually logging about 4,000 to 10,000 visitors per day, with the highest concentration of victims observed in India, the United States
, and Brazil
, the company’s report adds.
The malware has been dubbed “RenEngine loader” because some of the malicious code has been embedded inside a legitimate Ren’Py launcher, an engine used to run visual novel games.
“While these cracked games appear functional, they silently deliver embedded malware alongside the playable content,” the researchers wrote.

Malware Hidden in Pirated Games Infects 400,000 Devices
Security researchers uncover evidence that the Windows-based 'RenEngine loader' malware has infected around 30,000 users in the US alone.www.pcmag.com
O&O Offers HUGE Sale... 10 APPS for $39.00. For 1 PC.... Add 10.00 to get 5PC License.
- annaegorov
- Discounts and Deals
- Replies: 1
|
[td][/td] |
|---|
|
|
|---|
|
|
|---|
The above is not a subscription. This is for 1 PC. Add 10.00 for 5 PC (49.90 for 5 PC)
LINK BELOW...
O&O Software - OnlineShop
|
|
|---|
|
|
[td] 3. Professional data recovery made easy with O&O DiskRecovery 14 Pro O&O DiskRecovery combs every sector of a hard disk, memory card, or digital camera to find lost files. Even when files systems are formatted or destroyed, it is possible to reconstruct once deleted data. Over 400 file types and versions can be recognized and restored, including Word documents, Excel workbooks, Access databases, and virtually every sort of commonly used graphics, photo, movie, and music formats. [td] 4. Delete confidential data safely with O&O SafeErase 20 Pro Stop identity theft with secure data deletion! O&O SafeErase permanently deletes your confidential files using recognized methods so that a recovery is never possible, not even when using the best file recovery software. [td] 5. Optimize storage space and work better with Windows with O&O DiskCommander 5 O&O DiskCommander shows you which files are using how much space in clear lists and diagrams. Whether in the network or on your home PC. Once you have identified the superfluous files and the biggest space wasters, you can eliminate them quickly and easily. In this way you can keep track of your data and save yourself the expense of additional storage media. You’ll be amazed at how much space you gain once you’ve cleared yourself of excess baggage. [td] 6. THE antispy tool for Windows - O&O ShutUp10++ O&O ShutUp10++ means you have full control over which comfort functions under Windows 10 and Windows 11 you wish to use, and you decide when the passing on of your data goes too far. Using a very simple interface, you decide how Windows 10 and Windows 11 should respect your privacy by deciding which unwanted functions should be deactivated. O&O ShutUp10++ does not have to be installed – it can be simply run directly and immediately on your PC. [td] 7. More control over the Windows registry - O&O RegEditor O&O RegEditor is the convenient alternative to Windows’ own registry editor and offers you significantly more control, overview and ease of use when managing the Windows registry. [td] 8. Quick and easy Network Analysis in the LAN - O&O Lanytix When a network grows, transparency becomes a prerequisite: O&O Lanytix provides you with a clear overview of devices, structures and possible anomalies in your environment in the shortest possible time. Whether it’s a quick inventory, targeted troubleshooting or a simple security check – with just a few clicks, you can see what is active in the network and where action is needed. [td] 9. All important system information directly on the desktop - O&O DeskInfo With O&O DeskInfo, you can keep an eye on all relevant system information at all times – clearly arranged and directly on your desktop. The compact display informs you in real time about processor and memory usage, the health and free space of your drives, as well as network connections and current activity. This allows you to see at a glance how your system is doing without having to open additional tools or complicated menus. [td] 10. Easily remove unwanted Windows apps - O&O AppBuster When setting up Windows 10 and 11, Microsoft not only installs the operating system alone, but also a whole range of additional apps – some useful, some less so. O&O AppBuster allows you to remove the unwanted apps easily and quickly. Or, if you accidentally uninstalled one of these apps, you can also retrieve them with one click. |
|---|
|
OpenClaw Partners with VirusTotal to Secure AI Agent Skill Marketplace
- Parkinsond
- Security News
- Replies: 0
OpenClaw announced today a partnership with VirusTotal, Google’s threat intelligence platform, to implement automated security scanning for all skills published to ClawHub, its AI agent marketplace.
The integration marks the first comprehensive security initiative for the emerging AI agent ecosystem.
All skills published to ClawHub will now undergo automatic scanning using VirusTotal’s threat intelligence database and Code Insight capability, an LLM-powered security analysis tool. Skills flagged as malicious will be immediately blocked from download, while suspicious content receives warning labels.

OpenClaw Partners with VirusTotal to Secure AI Agent Skill Marketplace
OpenClaw announced today a partnership with VirusTotal, Google's threat intelligence platform, to implement automated security scanning for all skills published to ClawHub, its AI agent marketplace. The integration marks the first comprehensive security initiative for the emerging AI agent...cybersecuritynews.com
Best camera app for Android?
- aidunno
- AI-Powered Dedicated Forum
- Replies: 7
Best camera app for android?
Cybercriminals Use Malicious Cybersquatting Attacks to Distribute Malware and Hijack
- Parkinsond
- Security News
- Replies: 2
Digital squatting has evolved from a simple trademark nuisance into a dangerous cybersecurity threat.
Security experts warn that criminal networks are now using fake domains not just to sell them for a profit, but to steal customer data, distribute malware, and destroy brand reputations.
How Squatting Works
Cybercriminals use several deceptive tactics to trick users into visiting fraudulent websites:
- Typosquatting: Registering common misspellings of popular sites (e.g., gooogle.com).
- Combosquatting: Adding keywords to legitimate brand names (e.g., netflix-login.com).
- TLD Squatting: Using different extensions, such as registering a .net or .org version of a famous .com business.
- Homograph Attacks: Using visually similar characters from different alphabets to create undetectable fakes.

Cybercriminals Use Malicious Cybersquatting Attacks to Distribute Malware and Hijack Data
Security experts warn that criminal networks are now using fake domains not just to sell them for a profit, but to steal customer data.cybersecuritynews.com
MagFone iPhone Data Recovery 6month free
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Main Features of MagFone iPhone Data Recovery:
- Support recovering lost or deleted data directly from iOS devices.
- Recover iPhone and iPad data from iTunes backups and iCloud backups.
- Restore a wide range of data types like photos, videos, and more.
- Preview and selectively recover specific files without overwriting.
- Work in a safe, read-only mode to ensure data security and privacy.
- Easy to use for all uses with a simple interface and fast scanning speed.
- Support recovering lost or deleted data directly from iOS devices.
- Recover iPhone and iPad data from iTunes backups and iCloud backups.
- Restore a wide range of data types like photos, videos, and more.
- Preview and selectively recover specific files without overwriting.
- Work in a safe, read-only mode to ensure data security and privacy.
- Easy to use for all uses with a simple interface and fast scanning speed.
Hackers Exploit Free Firebase Accounts to Launch Phishing Campaigns
- Brownie2019
- Security News
- Replies: 3
More on:A new wave of phishing campaigns where scammers are abusing Google’s legitimate infrastructure to bypass security filters.
Attackers are now creating free developer accounts on Google Firebase to send fraudulent emails that impersonate well-known brands.
By leveraging the reputation of the Firebase domain, these attackers are successfully landing in users’ inboxes, bypassing standard spam detection systems.
How the Attack Works

Hackers Exploit Free Firebase Accounts to Launch Phishing Campaigns
A new wave of phishing campaigns where scammers are abusing Google’s legitimate infrastructure to bypass security filters.
 gbhackers.com
gbhackers.com
Hackers Linked to State Actors Target Signal Messages of Military Officials and Journalists
- Brownie2019
- Security News
- Replies: 2
Germany’s top security agencies issued an urgent warning yesterday regarding a sophisticated cyber espionage campaign targeting high-ranking officials and journalists across Europe.
The Federal Office for the Protection of the Constitution (BfV) and the Federal Office for Information Security (BSI) revealed that state-sponsored hackers are hijacking Signal accounts to spy on private communications.
The joint advisory, released February 6, identifies the primary targets as military personnel, diplomats, politicians, and investigative journalists.
Unlike traditional hacks that use malware or exploit software bugs, this campaign relies entirely on “social engineering”, tricking victims into using legitimate features against themselves.
The “Fake Support” Trap
The first attack method involves hackers posing as “Signal Support” or a “Signal Security ChatBot.”
They contact targets directly within the app, claiming suspicious activity or a data leak has occurred on the victim’s device.
To “fix” the problem, the fake support bot asks the user to verify their identity by sending a PIN code.
If a victim shares this six-digit code, the hackers immediately register the victim’s phone number on a new device they control.
This locks the legitimate user out of their own account while giving the attackers complete control to impersonate the victim in future chats.
The Silent QR Code Spy
The second method is more subtle and allows hackers to spy on chats without locking the user out.
Attackers use a plausible pretext, such as a request to join a group or verify a device, to trick the victim into scanning a QR code.
Technically, this QR code is a “device linking” request. When a victim scans it, they inadvertently authorize the hacker’s tablet or computer to link to their account.
Once connected, the attacker can silently read all new messages and view chat history from the past 45 days.
This access often persists for weeks because the victim’s phone usually continues to work, masking the intrusion.
Authorities believe a “state-controlled cyber actor” is behind the campaign, given the specific focus on high-value intelligence targets rather than financial theft.
The goal appears to be espionage, involving the mapping of social networks and the interception of sensitive political and military discussions.
Because the attacks use valid Signal features rather than viruses, they bypass most antivirus software.
Security officials urge all users to check their “Linked Devices” list in Signal settings immediately and never to share verification PINs with anyone, even accounts claiming to be support staff.
XenArmor Asterisk Password Recovery Pro 1yr free
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Features
- Automated and Manual Recovery: Users can opt for automated or manual recovery methods, providing flexibility in password retrieval.
- Compatibility with 180+ Windows Apps: The software supports password recovery from over 180 verified Windows applications, ensuring comprehensive coverage.
- Magic Search Icon: Features a magic search icon to reveal passwords in custom text fields, enhancing convenience and customization.
- Command-line Version: Includes a command-line version for easy automation and integration within scripts or programs, ideal for remote password recovery scenarios.
- Backup Password Report: Allows users to save recovered passwords to HTML, CSV, XML, JSON, or SQLite database files, facilitating efficient management and backup.
- User-Friendly GUI Interface: Boasts a user-friendly graphical user interface (GUI) with quick menu and action buttons, ensuring ease of use for both novice and advanced users.
- Recovery from 32-bit & 64-bit Apps: Xenarmor Asterisk Password Recovery is capable of recovering passwords from both 32-bit and 64-bit Windows applications, ensuring compatibility across various platforms.
- Automation of Recovery Process: Saves time and effort by automating the password recovery process, enhancing efficiency and productivity.
- Support for All Windows Platforms: Compatible with all Windows platforms, from Windows Vista to the latest Windows 11, ensuring broad accessibility and usability.
- Featured on Top Download Sites: Recognized and awarded by leading software download sites, attesting to its reliability, effectiveness, and popularity among users.
QILING Safe Disk Standard - Lifetime License
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Giveaway License Coverage
License Type Lifetime License Supported OS Windows 11, 10, 8/8.1, 7, Vista, XP
Features of Qiling Safe Disk
- Create encrypted drives: Create encrypted drives virtually on your computer, which are protected with strong encryption algorithms like AES, Blowfish, GOST, and 3DES. Once created, these virtual drives can only be accessed with the correct password, making them ideal for storing sensitive data.
- Flash drive and USB hard disk support: In addition to local drives, It supports flash media and USB hard disk drives, allowing you to encrypt and protect your data on these external devices as well. This is especially useful if you need to carry sensitive information with you while traveling or working remotely.
- Automatic backup and deduplication: Automatic backup options, allowing you to ensure that your encrypted data is always protected. It also includes deduplication technology, which can automatically eliminate duplicate data and reduce the disk space consumed by data.
- Mounting options: You can mount virtual drives read-only to avoid data on the disk from being infected or tampered with. The software can also automatically unmount the drive when you log out, further protecting your data from unauthorized access.
- Compatibility: Compatible with all Windows operating systems, including Windows 11/10/8/8.1/7/Vista/XP for the Standard Edition and Windows Server 2019/2016/2012/2008/2003 etc. for the Server Edition. It also supports a wide range of hard drives, USB drives, card storage, and large storage devices, including RAID and network-attached storage.
- Fast Disk Encryption: A free, fast AES 128-bit Disk encryption program called Private Disk Light. This program allows you to create a secure space for all your work, exchange encrypted data with others, and feel confident that your information is safe from external and internal manipulation.
I intercepted Brave's network traffic for 48 hours
What do web browsers really do in the background? Privacy advocates have a keen interest in this question. Promising users better privacy and freedom from ads, Brave has made quite a name for themselves with over 100 million monthly active users.
Multiple privacy researchers and engineers have overseen Brave's increasingly active open-source development, and Brave's feature set reflects that. Brave's own researchers continually publish academic papers (like these) in several prestigious venues on topics such as privacy, security, and machine learning. A number of privacy experts and enthusiasts really do endorse Brave. Accordingly, examining Brave's behavior is commonplace.
Brave Rewards has suffered from intermittent issues with helper components loading in the background even when turned off. It was never universal and stemmed from different variables in a user's setup coinciding around the original design as well as background extension unloading bugs in early Chromium versions. Importantly, when turned off, background helpers didn't generate unwanted network activity. Multiple fixes and improvements to cleanup/unloading code (including Chromium's) worked to remedy it for affected users over time. Resetting Rewards additionally helps resolve lingering cases. Nevertheless, Brave Rewards is designed for privacy and transparency when used, and it was always opt-in.
Brave obviously isn't the only browser ever to have had bugs or imperfect cleanup. It's complex software.
Without further ado, here's how I set out to record Brave's network activity. Using the latest version of HTTP Toolkit (v1.24.4), I took advantage of its respected toolset to intercept network requests made by Brave over the course of 48 hours. A Brave session was started with a fresh profile and launched with command-line switches to force the use of HTTP Toolkit's proxy and CA certificate. The temporary profile eliminates extra noise from extensions.
I verified that the proxy was working properly, and I disabled the QUIC (HTTP/3) protocol. There is no DNS adblocking in effect.
HTTP Toolkit started the new session by loading a simple webpage of its own:

Brave was quiet during those 48 hours. Just three tiny, anonymous pings took place to help Brave estimate active users. No unwanted privacy-preserving analytics (P3A) or Brave Rewards connections.

Finally, I navigated to

Multiple privacy researchers and engineers have overseen Brave's increasingly active open-source development, and Brave's feature set reflects that. Brave's own researchers continually publish academic papers (like these) in several prestigious venues on topics such as privacy, security, and machine learning. A number of privacy experts and enthusiasts really do endorse Brave. Accordingly, examining Brave's behavior is commonplace.
Brave Rewards has suffered from intermittent issues with helper components loading in the background even when turned off. It was never universal and stemmed from different variables in a user's setup coinciding around the original design as well as background extension unloading bugs in early Chromium versions. Importantly, when turned off, background helpers didn't generate unwanted network activity. Multiple fixes and improvements to cleanup/unloading code (including Chromium's) worked to remedy it for affected users over time. Resetting Rewards additionally helps resolve lingering cases. Nevertheless, Brave Rewards is designed for privacy and transparency when used, and it was always opt-in.
Brave obviously isn't the only browser ever to have had bugs or imperfect cleanup. It's complex software.
Without further ado, here's how I set out to record Brave's network activity. Using the latest version of HTTP Toolkit (v1.24.4), I took advantage of its respected toolset to intercept network requests made by Brave over the course of 48 hours. A Brave session was started with a fresh profile and launched with command-line switches to force the use of HTTP Toolkit's proxy and CA certificate. The temporary profile eliminates extra noise from extensions.
I verified that the proxy was working properly, and I disabled the QUIC (HTTP/3) protocol. There is no DNS adblocking in effect.
HTTP Toolkit started the new session by loading a simple webpage of its own:
amiusing.httptoolkit.tech. This generated five requests whose contents and responses are open to inspection. The only other request is Brave's usage ping that I left enabled. Looking into it, no identifiers are present—the X-Brave-API-Key header is uniformly hardcoded for all users. Usage pings can be turned off. I've opted out of analytics, however. From here, I let the browser sit idle to do its thing.Brave was quiet during those 48 hours. Just three tiny, anonymous pings took place to help Brave estimate active users. No unwanted privacy-preserving analytics (P3A) or Brave Rewards connections.
Finally, I navigated to
wikipedia.org. Autocomplete in the address bar produced no network activity. Brave loaded the website, 10 requests in total, and refrained from making its own requests. I was satisfied and stopped the experiment here.Windows 11 is finally killing off legacy printer drivers in 2026
- Gandalf_The_Grey
- Windows 11
- Replies: 3
Microsoft is moving forward with a long-planned cleanup of the Windows 11 printing stack. Starting with the non-security update released in January 2026, Windows 11 no longer supports legacy V3 and V4 printer drivers, a change that will affect devices running versions 24H2 and 25H2 as the rollout gradually expands.
The company first announced the deprecation of V3 and V4 printer drivers in September 2023, giving hardware partners and customers more than two years to prepare. As the final cutoff now approaching, Microsoft is signaling that the transition to modern printing is no longer optional for Windows 11 users.
In the official support page, the company notes that starting in "January 2026, Windows will no longer support V3 and V4 printer drivers. These older driver models were announced as deprecated in September 2023."

Microsoft is pulling the plug on old printer drivers — here’s what it means
The next system update for Windows 11 could break your printer. Here's what you need to know.
 www.windowscentral.com
www.windowscentral.com
Disney+ Disables Dolby Vision and HDR10+ in Some European Countries Due to Technical Challenges
- Gandalf_The_Grey
- Technology News
- Replies: 1
Disney+ has disabled Dolby Vision and HDR10 for Premium subscribers in several European countries, citing “technical challenges.” 3D movies on the Apple Vision Pro, which are also streamed in the Dolby Vision format, are also currently unavailable in affected markets.
FlatPanelsHD received the following statement from Disney+ about the issue. The publication also noticed that all references to Dolby Vision have been quietly removed from the Disney+ support page about video quality, including the US version.
This statement doesn’t tell the full story, however. Last month, German website Heise reported that there’s a patent dispute between Disney and Interdigital, a US company developing advanced video technologies. A German court recently issued an injunction “over “Disney’s infringement of an InterDigital patent related to the streaming of video content using high dynamic range (HDR) technology.”“Dolby Vision support for content on Disney+ is currently unavailable in several European countries due to technical challenges. We are actively working to restore access to Dolby Vision and will provide an update as soon as possible. 4K UHD and HDR support remain available on supported devices.”
If you’re in Europe and are paying for Disney+ Premium, you can still watch content in 4K and standard HDR. However, it’s currently unclear when support for the premium High Dynamic Range formats will come back.

Disney+ Disables Dolby Vision and HDR10+ in Some European Countries Due to "Technical Challenges"
Disney+ has disabled Dolby Vision and HDR10 for Premium subscribers in several European countries, citing “technical challenges.”
Privacy vs. Profit: The Impact of Google’s Manifest Version 3 (MV3) Update on Ad Blocker Effectiveness (Research Article)
- Parkinsond
- General Privacy Discussions
- Replies: 56
Our results reveal no statistically significant reduction in ad-blocking or anti-tracking effectiveness for MV3 ad blockers compared to their MV2 counter parts, and in some cases, MV3 instances even exhibit slight improvements in blocking trackers.
AISURU/Kimwolf Botnet Launches Record-Setting 31.4 Tbps DDoS Attack
- Miravi
- Security News
- Replies: 1
The distributed denial-of-service (DDoS) botnet known as AISURU/Kimwolf has been attributed to a record-setting attack that peaked at 31.4 Terabits per second (Tbps) and lasted only 35 seconds.
Cloudflare, which automatically detected and mitigated the activity, said it's part of a growing number of hyper-volumetric HTTP DDoS attacks mounted by the botnet in the fourth quarter of 2025. The attack took place in November 2025.
AISURU/Kimwolf has also been linked to another DDoS campaign codenamed The Night Before Christmas that commenced on December 19, 2025. Per Cloudflare, the average size of the hyper-volumetric DDoS attacks during the campaign was 3 billion packets per second (Bpps), 4 Tbps, and 54 requests per second (Mrps), with the maximum rates touching 9 Bpps, 24 Tbps, and 205 Mrps.
"DDoS attacks surged by 121% in 2025, reaching an average of 5,376 attacks automatically mitigated every hour," Cloudflare's Omer Yoachimik and Jorge Pacheco said. "In 2025, the total number of DDoS attacks more than doubled to an incredible 47.1 million."
The web infrastructure company noted that it mitigated 34.4 million network-layer DDoS attacks in 2025, compared to 11.4 million in 2024. In Q4 2025 alone, network-layer DDoS attacks accounted for 78% of all DDoS attacks. Put together, the number of DDoS attacks surged by 31% over the previous quarter and 58% over 2024.
In 2025 Q4, hyper-volumetric attacks increased by 40% compared to the previous quarter, witnessing a jump from 1,304 to 1,824. A total of 717 attacks were recorded in Q1 2025. The spike in the number of attacks has been complemented by an uptick in the size of these attacks, growing by over 700% compared to the large attacks seen in late 2024.

AISURU/Kimwolf Botnet Launches Record-Setting 31.4 Tbps DDoS Attack
AISURU/Kimwolf launched a record 31.4 Tbps DDoS attack as 2025 saw 47.1M incidents, rising botnet scale, and Android device abuse.
 thehackernews.com
thehackernews.com
Claude Opus 4.6 Finds 500+ High-Severity Flaws Across Major Open-Source Libraries
- Miravi
- Security News
- Replies: 2
Artificial intelligence (AI) company Anthropic revealed that its latest large language model (LLM), Claude Opus 4.6, has found more than 500 previously unknown high-severity security flaws in open-source libraries, including Ghostscript, OpenSC, and CGIF.
Claude Opus 4.6, which was launched Thursday, comes with improved coding skills, including code review and debugging capabilities, along with enhancements to tasks like financial analyses, research, and document creation.
Stating that the model is "notably better" at discovering high-severity vulnerabilities without requiring any task-specific tooling, custom scaffolding, or specialized prompting, Anthropic said it is putting it to use to find and help fix vulnerabilities in open-source software.
"Opus 4.6 reads and reasons about code the way a human researcher would—looking at past fixes to find similar bugs that weren't addressed, spotting patterns that tend to cause problems, or understanding a piece of logic well enough to know exactly what input would break it," it added.
Prior to its debut, Anthropic's Frontier Red Team put the model to test inside a virtualized environment and gave it the necessary tools, such as debuggers and fuzzers, to find flaws in open-source projects. The idea, it said, was to assess the model's out-of-the-box capabilities without providing any instructions on how to use these tools or providing information that could help it better flag the vulnerabilities.
The company also said it validated every discovered flaw to make sure that it was not made up (i.e., hallucinated), and that the LLM was used as a tool to prioritize the most severe memory corruption vulnerabilities that were identified.

Claude Opus 4.6 Finds 500+ High-Severity Flaws Across Major Open-Source Libraries
Anthropic’s Claude Opus 4.6 identified 500+ unknown high-severity flaws in open-source projects, advancing AI-driven vulnerability detection.
 thehackernews.com
thehackernews.com
Tenant from Hell: Prometei's Unauthorized Stay in Your Windows Server
- Khushal
- Security News
- Replies: 2

Tenant from Hell: Prometei's Unauthorized Stay in Your Windows Server
Learn about the Prometei botnet that gets deployed on a Windows server, including a comprehensive breakdown of Prometei’s technical operations, and how organizations can stay ahead of this threat.www.esentire.com
In January 2026, eSentire's Threat Response Unit (TRU) detected a malicious command attempting to deploy Prometei on a Windows Server belonging to a customer in the Construction industry.
Prometei is a botnet suspected to be of Russian origin and has been active since 2016. It features extensive capabilities, including remote control functionality, credential harvesting, crypto-mining (Monero), lateral movement, Command and Control (C2) over both the clearweb and TOR network, and self-preservation measures that harden compromised systems against other threat actors, to maintain exclusive access.
This blog provides a comprehensive breakdown of Prometei's technical operations including its installation process, persistence mechanisms, encryption methods, C2 communication protocols, and the additional modules it employs.
Help with Samsung phone infected by a fake scanner app
- Pirate pete
- Mobile Malware Removal Help & Support
- Replies: 1
Hi, I need help with my android phone. Today i had a pop-up whilst using a pdf scaner app on my samsung phone which said i needed to update the software or loose all scanned files. I clicked on the update link and it obviously was a virus which basically changed my phone's homescreen immediately and the layout of all my apps. It seems to have downloaded something called Document Reader-PDF launcher on my homescreen and i can not uninstall it or remove it
I do not know how to get my phone back to how it was setup? Any help would be greatly appreciated
I do not know how to get my phone back to how it was setup? Any help would be greatly appreciated
Has anybody at MT used CheckMal AntiRansomware and can provide any feedback?
Anyone who has used this program called AppCheck? Can you please provide any feedback about its protection?
Milano Cortina 2026 cyberattacks – Italy blames Russia
- Brownie2019
- Security News
- Replies: 1
Italy says Russian-linked cyberattack hit Olympic Winter Games
Cyberattacks “of Russian origin” have already targeted Milano Cortina 2026 infrastructure, with attempted disruptions tied to government systems and Olympic-related networks, Italian officials said.
Foreign Minister Antonio Tajani said the activity included foreign ministry portals and touched Olympics-adjacent services in Cortina.
While he did not publicly detail the malware or modus operandi nor clarify whether the activity appears state-directed or driven by aligned groups, the timing puts Olympic cybersecurity on high alert.
Winter Olympics cybersecurity faces DDoS and hacktivist pressure
Major sporting events are prime targets because they combine global attention with sprawling vendor ecosystems, including ticketing, transport, hospitality and official web properties. Recent reports link the attempted disruptions to pro-Russia hacktivist-style operations, including denial-of-service (DoS) tactics aimed at knocking services offline.
The UK’s National Cyber Security Centre has also warned against underestimating state-aligned hacktivists that focus on disruptions over stealth. This is exactly the kind of tactics meant to rattle public trust during live, high-audience events.
Cloudflare-Italy dispute raises questions about defensive capacity
Separately, a regulatory clash is adding friction to the security picture. Italy’s communications regulator fined Cloudflare over anti-piracy compliance tied to its DNS and related services, prompting the company’s CEO to publicly threaten to pull infrastructure and withdraw free protections for the Games.
For Olympic organizers, the concern is less about attribution and more about resilience. Large-scale sporting events depend on uninterrupted digital services ranging from accreditation services to transport coordination and public-facing platforms.
With early competitions already underway and geopolitical tensions looming, Italy’s ability to maintain cyber resilience throughout the games may prove as crucial as physical security on the event grounds.
EDR, Email, and SASE Miss This Entire Class of Browser Attacks
- Brownie2019
- Security News
- Replies: 1
Full Story:Most enterprise work now happens in the browser. SaaS applications, identity providers, admin consoles, and AI tools have made it the primary interface for accessing data and getting work done.
Yet the browser remains peripheral to most security architectures. Detection and investigation still focus on endpoints, networks, and email, layers that sit around the browser, not inside it.
The result is a growing disconnect. When employee-facing threats occur, security teams often struggle to answer a basic question: what actually happens in the browser?
That gap defines an entire class of modern attacks.
At Keep Aware, we’ve called this a “safe haven” problem for attackers, where the target has now become this central point of failure
Browser Attacks Seen in 2026 Leaving Little Traditional Evidence

EDR, Email, and SASE Miss This Entire Class of Browser Attacks
Many modern attacks happen entirely inside the browser, leaving little evidence for traditional security tools. Keep Aware shows why EDR, email, and SASE miss browser-only attacks and how visibility changes prevention.
Flickr Notifies Users of Data Breach After External Partner Security Flaw
- Brownie2019
- Security News
- Replies: 1
Read more on:Flickr says a third-party email vendor flaw may have exposed user names, emails, IP data, and activity logs, though passwords and payments stayed secure.
A security flaw at a third-party email service provider has potentially exposed the personal details of Flickr members. On February 5, 2026, the popular photo-sharing platform was alerted to a vulnerability within a system managed by one of its external vendors. This loophole may have allowed unauthorised individuals to view specific member data.
Flickr, currently operated by SmugMug, acted quickly to address the issue, disabling access to the compromised system within hours of the discovery. For your information, this incident follows a similar pattern to a recent security report involving Substack, newsletter platform. As reported by Hackread.com, a hacker using the alias ‘w1kkid’ claimed on February 2, 2026, to have extracted over 662,000 user records from Substack, a breach the company’s CEO only confirmed days later.
Details of the Data Exposure

Flickr Notifies Users of Data Breach After External Partner Security Flaw
Flickr says a third party email vendor flaw may have exposed user names, emails, IP data and activity logs, though passwords and payments stayed secure.
 hackread.com
hackread.com
Photomizer 3 Premium for free
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Features:
-Optimizes your photos automatically with object recognition, redistribution of tonality, white balance, resharpening and setting of shades, saturation, contrast optimization, and bright/dark correction.-It effectively and automatically removes disruptive noise, for example, for snapshots under unfavorable light conditions.
-Thanks to this nostalgic package, Photomizer 3 sends each image in an instant on a time travel into the past. Different retro effects create pure nostalgia.
-High contrast, vibrant colors: Create HDR-similar images with one single photo.
-The tilt-shift module is an unparalleled tool that produces stunning effects. Without any expensive equipment and expertise—normal cell phone photos from the top view and this module are completely enough.
-In addition to the usual formats jpg, BMP, and TIFF, Photomizer 3 also supports many RAW formats: HDP, WDP, ICO, RAW, ORF, 3FR, RAF, NRW, DNG, ARW, NEF, X3F, SRW, PEF, and RW2.
-Repair Module for Scanned Photos.
-Time-saving batch mode
Download:
Coolmuster PDF Locker 1yr free
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Features
- Add a user password to protect your own PDF files.
- Apply the owner’s password to control the access permission of PDF files, such as copying, modifying, and quality printing.
- 3 encryption security levels for your reference.
- Various options for PDF security, such as resolution settings, document printing, and copying.
- Support drag and drop operation.
- The batch process is supported.
Softorbits Batch Picture Resizer
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Features
- Process many photos in just a few clicks.
- Resize images in batch mode,
- Attach text, logotypes, and picture watermarks.
- Change photos between multiple forms,
- Available for GUI and command line,
- Automatically turn around JPEG images based on EXIF information.
- Lossless picture rotation, flipping, and mirroring for JPEG files,
- Preserves EXIF tags,
- Changes in canvas size,
- Help RAW images (CRW, CR2, NEF, PEF, RAF, RAW, DNG, MNG, etc.),
- Batch photo renaming,
- Prompt-free overwrite or saving into new files,
- Automatic level adjustment and color optimization,
- Greyscale conversion,
- Supports Windows 7 and 8, Explorer menu integration
- Compression rate and DPI change for output files
Dutch Authorities Seized Servers of Windscribe VPN Provider
- Parkinsond
- Security News
- Replies: 9
The server, a standard VPN node, was physically removed by law enforcement seeking potential logs tied to criminal activity. Unlike routine data requests, where Windscribe responds that it holds no user information, this marked a direct hardware confiscation.
Windscribe employs RAM-only (diskless) servers that erase all data upon power loss or reboot, reloading a pristine Ubuntu installation each time. This eliminates persistent storage of connection timestamps, IP addresses, or browsing activity, aligning with its audited no-identifying-logs policy.
Security experts note that RAM disks effectively block casual forensics but warn that advanced techniques, such as live memory dumps, if a seized device is powered on, could theoretically capture transient data, though unlikely here. Past incidents, such as the 2021 Ukraine seizures exposing unencrypted configs, prompted Windscribe’s full RAM pivot.

Dutch Authorities Seized Servers of Windscribe VPN Provider
Dutch authorities seized a Windscribe VPN server located in the Netherlands as part of an undisclosed investigation. The Canadian provider quickly highlighted how its privacy-focused design thwarted any data recovery efforts.cybersecuritynews.com
Black Basta: Defense Evasion Capability Embedded in Ransomware Payload
- Khushal
- Security News
- Replies: 3
A recent Black Basta attack campaign was notable because the ransomware contained a bring-your-own-vulnerable-driver (BYOVD) defense evasion component embedded within the ransomware payload itself.
Normally the BYOVD defense evasion component of an attack would involve a distinct tool that would be deployed on the system prior to the ransomware payload in order to disable security software. However, in this attack, the vulnerable driver (an NsecSoft NSecKrnl driver) was bundled with the ransomware itself.

Black Basta: Defense Evasion Capability Embedded in Ransomware Payload
BYOVD component included in ransomware payload itself, rather than as a separate tool.
Fake CrystalDiskMark website
- Parkinsond
- General Security Discussions
- Replies: 2
Reported here:
The fake website:
 crystaldiskmark.org
crystaldiskmark.org
Detected on VT:
Detected by Norton safe web:
The official website:
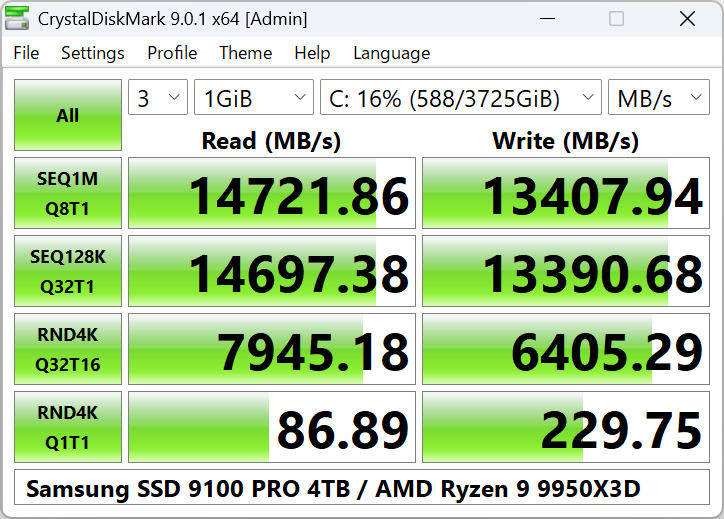
The fake website:
CrystalDiskMark - Drive Speed Benchmarking
CrystalDiskMark is a disk benchmarking tool to measure the performance of HDDs, SSDs, and USB drives, aiding in storage device comparisons.
 crystaldiskmark.org
crystaldiskmark.org
Detected on VT:
Detected by Norton safe web:
The official website:

CrystalDiskMark
About CrystalDiskMark CrystalDiskMark is a simple disk benchmark software. Download Standard Edition Aoi Edition Shizuku Edition System Requirements OS Windows XP/Vista/7/8/8.1/10/11Windows Server 2003/2008/2012/2016/2019/2022/2025 Architecture x86/x64/ARM64 Key Features Important Notice -> FAQ U...
crystalmark.info
Western Digital unveils massive 40TB HDD with energy-assisted recording tech — plans 100TB HAMR hard drives by 2029
- Parkinsond
- Hardware Discussions
- Replies: 1
Western Digital on Tuesday announced plans to extend its energy-assisted perpendicular magnetic recording (ePMR) technology to 60TB, thus producing ePMR-based hard drives along with its heat-assisted magnetic recording (HAMR) for several years down the road to guarantee steady availability of high-capacity drives.
The company intends to release its 40TB UltraSMR hard drive in the second half of this year, with its HAMR-based counterpart following in 2027. By 2029, Western Digital plans to offer 100TB HAMR-based HDDs.

Western Digital unveils massive 40TB HDD with energy-assisted recording tech — plans 100TB HAMR hard drives by 2029
HAMR HDDs to be accompanies by ePMR drives for several years.www.tomshardware.com
New from VMRay Labs: Climbing the Pyramid of Lumma Pain
- Khushal
- Security News
- Replies: 2
Infostealers like Lumma aren’t just widespread — they’re evolving fast. In this new Labs blog, Julian Wolf breaks down how Lumma operates across delivery, evasion, and monetization, and what defenders can do to move from reactive cleanup to meaningful disruption.

How threat actors abuse SVGs for phishing
How malware analysis reveals Lumma Stealer C2 infrastructure patterns and helps defenders climb the Pyramid of Pain.www.vmray.com
Stan Ghouls targeting Russia and Uzbekistan with NetSupport RAT
- Khushal
- Security News
- Replies: 2
This Kaspersky analysis details a new campaign carried out by the Stan Ghouls threat group, which primarily targeted organizations within the industrial manufacturing, IT, and financial sectors across Uzbekistan. The activity also produced secondary impacts in Russia, Kazakhstan, and a few unintended locations.
In total, over 60 entities were affected—an unusually large number for such a highly targeted operation—indicating the group’s substantial operational investment. Despite their scale, Stan Ghouls continue to rely on a familiar toolkit centered around the legitimate NetSupport remote administration tool and their signature custom Java-based loader. Their main updates appear to concern infrastructure, as this campaign introduced two new domains for hosting the malicious loader and another dedicated to distributing NetSupport RAT files.
An unexpected finding was the presence of Mirai-related files on a domain previously linked to the group, hinting that Stan Ghouls may be experimenting with IoT malware, though this remains uncertain.
Kaspersky continues to monitor the group’s activities closely and assures users that its products are capable of defending against the Stan Ghouls campaign throughout all stages of an attack.

Comprehensive analysis of initial attack samples exploiting CVE-2023-23397 vulnerability
We will highlight the key points and then focus on the initial use of the CVE-2023-23397 vulnerability by attackers before it became public.
The struggle against Ransomware for big name AV continues.
- Khushal
- Video Reviews - Security and Privacy
- Replies: 20
First it was ESET in a lab test.
Now it is Bugdefender.
How I disabled 13 AI features in Windows 11 safely, no third-party apps needed
- Gandalf_The_Grey
- Windows 11
- Replies: 4
In 2026, all major consumer-focused operating systems have AI baked in. However, Windows 11 is the only one getting all the hate, and it can all be laid at Microsoft’s door.
The company went too far too fast, and made a desktop OS, with 1 billion users, a testing ground for their half-cooked AI companion – the infamous Copilot.
While Copilot itself has an app, with its own dedicated key in all the latest Windows laptops, Microsoft made the daring decision to integrate the AI and its logo in all its popular applications, including the Edge browser, Notepad, File Explorer, the Office suite, and even the Windows 11 Taskbar.
Unsurprisingly, this aggressive AI push has earned Microsoft the unflattering moniker of “Microslop”. Frustrated users now use Microslop to describe what Windows 11 has become in their eyes. An OS with the Copilot logo slapped everywhere, powering features nobody asked for. And for users who simply want a fast, reliable desktop without an AI assistant waiting desperately for every other click, the obvious question is, can you completely disable Copilot in Windows 11?
Well, in this guide, we will show you how to remove Copilot and other AI components from Windows 11, disable AI integrations, and reclaim a clean, distraction-free Windows.

How I disabled 13 AI features in Windows 11 safely, no third-party apps needed
Learn how to remove Copilot from Windows 11, including Edge, Search, Photos, Notepad, File Explorer, Paint, and other built-in AI features.
LanguageTool ends free use of Browser Extension, Are There Good Alternatives?
- lokamoka820
- Web Extensions
- Replies: 9
Today, a web page popped up on my browser saying that LanguageTool has ended free use of its browser extension:

 languagetool.org
languagetool.org
Are there good alternatives?
We have made the difficult decision to limit the use of LanguageTool’s browser extension to Premium users only. The rise of generative AI has made it more challenging to sustainably monetize our offering. A majority of users use our products for free, and the relatively small percentage of Premium subscribers is all that is subsidizing our continuously increasing server costs. To improve our Premium experience and to sustain our business model, we’ll be making the LanguageTool browser extension available exclusively for paying customers.

Important: Upgrade Required - LanguageTool
Instantly check grammar, punctuation, and spelling errors with LanguageTool's AI-powered grammar checker. Enhance your writing in over 30 languages with ease.
Are there good alternatives?
FreeCommander XE Updates Thread
- lokamoka820
- Other software
- Replies: 3
FreeCommander is an easy-to-use alternative to the standard windows file manager. The program helps you with daily work in Windows. Here you can find all the necessary functions to manage your data stock. You can take FreeCommander anywhere – just copy the installation directory on a CD or USB-Stick – and you can evenwork with this program on a foreign computer.
Help-Online
Website: FreeCommander
Main features in FreeCommander:
- Dual-panel technology – horizontal and vertical (one panel possible too)
- Tabbed interface
- Full access to desktop
- Optional tree view for each panel
- Built-in file viewer to view files in hex, binary, text or image format
- File viewer and thumbnail view inside archives too
- Built-in archive handling: ZIP (read, write)
- Nested archive handling
- Plugins for other archive (RAR, 7z, …)
- Plain view – structureless view for files and folders
- Linked browsing
- Easy access to system folders, control panel, desktop and start menu
- Copy, move, delete, rename files and folders (alternatively as Windows or FreeCommander operation)
- Drag&drop
- File searching (inside archive too)
- Searching duplicates
- Create and verify MD5 and SHA checksums
- Wipe files
- Multi rename tool
- Paths longer than 255 characters can be opened, copied, moved and renamed
- File properties and context menu
- Calculation of folder size
- Folder comparison
- Folder synchronization
- Modification of file date and attributes
- Folder / program favorites
- File filters (regexp possible too) for display and file operations
- User defined columns for detailed views
- Automatic views
- Simple FTP/SFTP client (SFTP only 64 bit)
- Access to mobile devices (e.g. smartphones, tablets)
- DOS command line
- Quick viewer
- Quick search
- Quick filter
- Quick starter
- Desktop snapshots
- All keyboard shortcuts are definable
- Flexible configuration of almost all features
- Color schemes
- Multiple language support
Help-Online
Website: FreeCommander
Use ChatGPT to Flag Scams Instantly With Malwarebytes
- lokamoka820
- Malwarebytes
- Replies: 18
Malwarebytes has integrated its threat intelligence into ChatGPT, allowing users to instantly check suspicious links, emails, texts, and phone numbers for scams. This free tool works across all ChatGPT plans, helping flag phishing attempts, fake alerts, and malicious domains quickly, though it’s not a full replacement for antivirus software.
What It Does
- Connects ChatGPT to Malwarebytes’ live threat database updated from millions of devices.
- Lets users paste links, emails, texts, phone numbers, or screenshots into ChatGPT for scam analysis.
- Provides detailed explanations of why something is flagged (e.g., newly registered domains, impersonation signs).
- Free to use — no Malwarebytes account required.
Everyday Scam Detection
- Flags common scams like:
- Fake delivery alerts
- Urgent bank/account verification messages
- Phishing job offers or giveaway scams
- Unknown numbers posing as customer support
- Warns about dangerous domains that may lead to malware such as data stealers.
How to Use
- In ChatGPT, go to Apps → Search for Malwarebytes → Connect.
- Paste suspicious content and tag @Malwarebytes.
- Receive scam analysis with reasons and recommended actions.
- If uncertain, the tool may respond with “unknown” and advise caution.
Performance
- Strengths: Excellent at spotting known scam patterns, reused phishing messages, and malicious domains.
- Limitations:
- May miss brand‑new scams not yet in the database.
- Doesn’t block threats on your device.
- Works best as a first check, not a substitute for antivirus/anti‑malware protection.
The ChatGPT Malwarebytes scam checker is a practical, free upgrade for anyone using ChatGPT. It helps users make faster, safer decisions when faced with suspicious messages, but should be paired with traditional security tools for full protection.

Use ChatGPT to Flag Scams Instantly With Malwarebytes - Make Tech Easier
Use the ChatGPT Malwarebytes scam checker to flag suspicious links, emails, and texts instantly inside ChatGPT for free.
Seattle-area neurologist warns 13,500 people of data breach that leaked SSNs, medical info
- Miravi
- Security News
- Replies: 1
Neurological Associates of Washington near Seattle this week confirmed it notified 13,500 state residents of a December 2025 data breach that compromised the following info:
A cybercriminal group called DragonForce took credit for the attack on December 27, 2025, saying it stole 1.4 TB of data from the clinic. To prove its claim, DragonForce posted sample images of what it says are documents stolen from Neurological Associates of Washington.
- Names
- Social Security numbers
- Diagnoses
- Disability codes
- Medical info
- Dates of birth
- Addresses
- Other types of information
Neurological Associates of Washington cited DragonForce as the attacker, but Comparitech cannot verify the authenticity of the allegedly stolen data. We do not know if Neurological Associates of Washington paid a ransom, how much DragonForce demanded, or how attackers breached the clinic’s network. Comparitech contacted Neurological Associates of Washington for comment and will update this article if it replies.
“Our facilities server that stored medical records from 2019-2025 was attacked and encrypted. We discovered some of the data one of our computers was stolen,” says the clinic’s notice to victims.
Neurological Associates of Washington is offering eligible data breach victims 12 months of free credit monitoring.

Seattle-area neurologist warns 13,500 people of data breach that leaked SSNs, medical info - Comparitech
Neurological Associates of Washington warned 13,500 people of a ransomware breach that leaked SSNs and medical info. DragonForce took credit.
Depreciated Microsoft Browser Protection extension
- LinuxFan58
- Web Extensions
- Replies: 13
Recognize this? Installed a security extension in your browser, because you have perfected your setup, because the downside of a (near) perfect setup is that there is nothing left to tweak or improve!
Happened to me: so I installed the M$ browser protection while development should have been stopped. Just for fun to check out how effective this (over) aged extensions still was ... TO MY SURPRISE ...
it did surprisingly well when throwing malware, phishing and fake shops (scams) at it!
Its name Microsoft Defender Browsing Protection.
So Idecided to add it to my work profile (which are mostly M$ cloud services, so I don' t mind M$ learning what websites I am visiting for work).
Anyone still using it on a Chromium (non Edge) based browser (like me on Brave)?
Happened to me: so I installed the M$ browser protection while development should have been stopped. Just for fun to check out how effective this (over) aged extensions still was ... TO MY SURPRISE ...
it did surprisingly well when throwing malware, phishing and fake shops (scams) at it!
Its name Microsoft Defender Browsing Protection.
So Idecided to add it to my work profile (which are mostly M$ cloud services, so I don' t mind M$ learning what websites I am visiting for work).
Anyone still using it on a Chromium (non Edge) based browser (like me on Brave)?
Absolute Software Data Protect - 1 Year $9.99
- Brownie2019
- Discounts and Deals
- Replies: 0
If your device is missing, you need your personal files and information protected against fraudulent activity, no matter who's pushing the buttons. Installing Absolute Data Protect on your laptop lets you locate your device, lock it from unauthorized use, and permanently erase your sensitive data, all from your remote location. Your important files, pictures, saved passwords, and personal information are secure, and your identity is safe.
DoYourData Uninstaller Free
- Brownie2019
- Other software
- Replies: 1
Best Free Uninstaller for Windows 11/10/8/8.1/7/Server
 www.doyourdata.com
www.doyourdata.com
- Uninstall unwanted programs one-by-one or in batches.
- Remove all leftovers including registry files, logs, caches, related junk data, etc.
- Easy-to-use uninstaller: select, uninstall, complete!
- Uninstall app types of programs including crashed or stubborn programs.
Powerful Free PC Uninstaller | DoYourData Uninstaller Free[Windows 11 Supported]
DoYourData Uninstaller Free, free all-in-one PC uninstaller, can help you easily uninstall programs, Windows Apps, plug-ins one by one or in batches. And clean up all leftovers.
An AI plush toy exposed thousands of private chats with children
- Brownie2019
- Security News
- Replies: 3
Full Story:Bondu’s AI plush toy exposed a web console that let anyone with a Gmail account read about 50,000 private chats between children and their cuddly toys.

An AI plush toy exposed thousands of private chats with children
Around 50,000 chat transcripts between children and Bondu’s AI dinosaur plushie were accessible to anyone with a Google account.
Open the wrong “PDF” and attackers gain remote access to your PC
- Brownie2019
- Security News
- Replies: 5
Cybercriminals behind a campaign dubbed DEAD#VAX are taking phishing one step further by delivering malware inside virtual hard disks that pretend to be ordinary PDF documents. Open the wrong “invoice” or “purchase order” and you won’t see a document at all. Instead, Windows mounts a virtual drive that quietly installs AsyncRAT, a backdoor Trojan that allows attackers to remotely monitor and control your computer.
It’s a remote access tool, which means attackers gain remote hands‑on‑keyboard control, while traditional file‑based defenses see almost nothing suspicious on disk.
From a high-level view, the infection chain is long, but every step looks just legitimate enough on its own to slip past casual checks.
Victims receive phishing emails that look like routine business messages, often referencing purchase orders or invoices and sometimes impersonating real companies. The email doesn’t attach a document directly. Instead, it links to a file hosted on IPFS (InterPlanetary File System), a decentralized storage network increasingly abused in phishing campaigns because content is harder to take down and can be accessed through normal web gateways.
The linked file is named as a PDF and has the PDF icon, but is actually a virtual hard disk (VHD) file. When the user double‑clicks it, Windows mounts it as a new drive (for example, drive Einstead of opening a document viewer. Mounting VHDs is perfectly legitimate Windows behavior, which makes this step less likely to ring alarm bells.
Inside the mounted drive is what appears to be the expected document, but it’s actually a Windows Script File (WSF). When the user opens it, Windows executes the code in the file instead of displaying a PDF.
After some checks to avoid analysis and detection, the script injects the payload—AsyncRAT shellcode—into trusted, Microsoft‑signed processes such as RuntimeBroker.exe, OneDrive.exe, taskhostw.exe, or sihost.exe. The malware never writes an actual executable file to disk. It lives and runs entirely in memory inside these legitimate processes, making detection and eventually at a later stage, forensics much harder. It also avoids sudden spikes in activity or memory usage that could draw attention.
For an individual user, falling for this phishing email can result in:
Theft of saved and typed passwords, including for email, banking, and social media.
Exposure of confidential documents, photos, or other sensitive files taken straight from the system.
Surveillance via periodic screenshots or, where configured, webcam capture.
Use of the machine as a foothold to attack other devices on the same home or office network.
How to stay safe
Because detection can be hard, it is crucial that users apply certain checks:
Don’t open email attachments until after verifying, with a trusted source, that they are legitimate.
Make sure you can see the actual file extensions. Unfortunately, Windows allows users to hide them. So, when in reality the file would be called invoice.pdf.vhd the user would only see invoice.pdf. To find out how to do this, see below.
Use an up-to-date, real-time anti-malware solution that can detect malware hiding in memory.
Showing file extensions on Windows 10 and 11
To show file extensions in Windows 10 and 11:
Open Explorer (Windows key + E)
In Windows 10, select View and check the box for File name extensions.
In Windows 11, this is found under View > Show > File name extensions.
Alternatively, search for File Explorer Options to uncheck Hide extensions for known file types.
Beware of Fake Traffic Ticket Portals that Harvest Your PII and Credit Card Data
- Parkinsond
- Security News
- Replies: 1
I had one few months ago.A sophisticated phishing campaign targeting Canadian citizens has emerged, using fake traffic ticket payment portals to steal personal and financial information.
The scam begins when individuals receive text messages or encounter malicious advertisements claiming they have unpaid traffic fines.
The fake websites mimic the appearance of legitimate government platforms, complete with provincial logos and official-looking designs that build trust and credibility.

Beware of Fake Traffic Ticket Portals that Harvest Your PII and Credit Card Data
Fake traffic ticket scams target Canadians using SEO-poisoned sites posing as provincial portals to steal personal and financial data.cybersecuritynews.com
SMS asking to visit website to pay a traffic ticket.
Used PC, not phone, to open the link.
Redirected to a website identical to the official one, even the domain is well-crafted and raises no suspicion.
Not blocked by ControlD DNS, SmartScreen, Symantec browser protection, Norton safe web, McAfee web advisor, nor Avast web shield.
The only thing that make me suspect, the SMS did not contain the car registration number.
Inside a Multi-Stage Android Malware Campaign Leveraging RTO-Themed Social Engineering
- Khushal
- Security News
- Replies: 3
Seqrite researchers identified a three-stage Android malware campaign in India that impersonates RTO and government portals and spreads via WhatsApp. It uses cryptomining, persistence, and data theft with a cloud-backed C2, infecting about 7,400 devices.

Inside a Multi-Stage Android Malware Campaign Leveraging RTO-Themed Social Engineering | Seqrite
In recent years, Android malware campaigns in India have increasingly abused the trust associated with government services and official digital platforms. By imitating well-known portals and leveraging social engineering through messaging applications, threat actors exploit user urgency and lack...www.seqrite.com

Hunting Lazarus Part IV: Real Blood on the Wire Part IV
- Khushal
- Security News
- Replies: 2
Hunting Lazarus Part IV: Real Blood on the WirePart IV: https://redasgard.com/blog/hunting-lazarus-part4-real-blood-on-the-wire
Part III: https://redasgard.com/blog/hunting-lazarus-part3-infrastructure-too-perfect
Part II: https://redasgard.com/blog/hunting-lazarus-part2-blockchain-dead-drop
Part I: https://redasgard.com/blog/hunting-lazarus-contagious-interview-c2-infrastructure
Amaranth-Dragon: Weaponizing CVE-2025-8088 for Targeted Espionage in the Southeast Asia
- Khushal
- Security News
- Replies: 3
In 2025, Amaranth-Dragon APT weaponized the popular WinRAR CVE-2025-8088 for targeted espionage across Southeast Asia. Custom loader, Telegram RAT, geofenced C2, and event-themed lures.


Amaranth-Dragon: Weaponizing CVE-2025-8088 for Targeted Espionage in the Southeast Asia - Check Point Research
Key Points Introduction Check Point Research has identified several campaigns targeting multiple countries in the Southeast Asian region. These related activities have been collectively categorized under the codename “Amaranth-Dragon”. The campaigns demonstrate a clear focus on government...research.checkpoint.com
Antropic releases New Coding AI. Indian Tech Stocks Fell
- Victor M
- Technology News
- Replies: 22

Anthropic AI: Explained: What is Anthropic's AI tool that wiped $285 billion off software stocks in a single day | - The Times of India
Tech News News: Anthropic's newly launched AI plugins have triggered what analysts are calling a 'SaaSpocalypse'—a brutal selloff that wiped out roughly $285 billion .
Opera statement on the F.B.(FluffBusting)Purity add-on false positive
- Opera Team
- Opera
- Replies: 0
Hi Opera users,
We would like to address an issue involving F.B.(FluffBusting)Purity, an add-on developed by st333v and hosted on Opera’s Add-ons Store. We wish to reiterate that the F.B.(FluffBusting)Purity add-on is safe, and st333v is a verified developer in good standing.
Keeping users safe is a high priority for us. Browser add-ons can be powerful and can be vulnerable to exploitation. This is why we have manual reviews and systems in place to identify potential issues before they reach users. In this blog, we wish to discuss this specific event where our security system returned a false positive, and to apologize to the developer.
15 January 2026, 16:03 CET: Developer st333v uploads a new version of his add-on, F.B.(FluffBusting)Purity, on the Add-ons store. By mistake, he uploads a Manifest V2 version of the add-on, which Opera’s Add-ons store no longer supports for new add-ons.
15 January 2026, 16:40 CET: st333v requests assistance with removing this version, so that the correct version of the add-on can have the same version number as in other browser stores and avoid discrepancies.
15 January 2026, 16:58 CET: An Opera team member assists with this task, and the correct version is uploaded by st333v on the same day, at 19:14 CET.
16 January 2026, 08:24 CET: The new version is approved and published on Opera’s Add-ons store.
19 January 2026, 00:24 CET: The developer and users of the add-on notice that F.B.(FluffBusting)Purity has been flagged by the system as malicious, and users have received notifications that the add-on has been blacklisted. The developer raises the issue with Opera.
19 January 2026, 11:23 CET: Our team begins investigating in order to address the error and restore the add-on.
22 January 2026, 12:30 CET: The system problems are resolved and the developer is invited to re-upload the correct version of the add-on.
22 January 2026, 14:25 CET: st333v re-uploads the correct version.
22 January 2026, 14:50 CET: The new version is approved and published on Opera’s Add-ons store.
We apologize for the confusion and inconvenience that this incident caused, particularly to st333v. We appreciate his collaboration and patience while we worked to resolve the issue as quickly as possible.
We have addressed the bug that led to this development, and we are taking steps to ensure that incidents such as this are not repeated in the future.
The F.B.(FluffBusting)Purity add-on is fully restored on Opera’s Add-ons store and is safe to use, as it always has been.
We thank everyone for their patience and understanding.
Source: Opera statement on the F.B.(FluffBusting)Purity add-on false positive
We would like to address an issue involving F.B.(FluffBusting)Purity, an add-on developed by st333v and hosted on Opera’s Add-ons Store. We wish to reiterate that the F.B.(FluffBusting)Purity add-on is safe, and st333v is a verified developer in good standing.
Keeping users safe is a high priority for us. Browser add-ons can be powerful and can be vulnerable to exploitation. This is why we have manual reviews and systems in place to identify potential issues before they reach users. In this blog, we wish to discuss this specific event where our security system returned a false positive, and to apologize to the developer.
What happened
15 January 2026, 16:03 CET: Developer st333v uploads a new version of his add-on, F.B.(FluffBusting)Purity, on the Add-ons store. By mistake, he uploads a Manifest V2 version of the add-on, which Opera’s Add-ons store no longer supports for new add-ons.
15 January 2026, 16:40 CET: st333v requests assistance with removing this version, so that the correct version of the add-on can have the same version number as in other browser stores and avoid discrepancies.
15 January 2026, 16:58 CET: An Opera team member assists with this task, and the correct version is uploaded by st333v on the same day, at 19:14 CET.
16 January 2026, 08:24 CET: The new version is approved and published on Opera’s Add-ons store.
19 January 2026, 00:24 CET: The developer and users of the add-on notice that F.B.(FluffBusting)Purity has been flagged by the system as malicious, and users have received notifications that the add-on has been blacklisted. The developer raises the issue with Opera.
19 January 2026, 11:23 CET: Our team begins investigating in order to address the error and restore the add-on.
22 January 2026, 12:30 CET: The system problems are resolved and the developer is invited to re-upload the correct version of the add-on.
22 January 2026, 14:25 CET: st333v re-uploads the correct version.
22 January 2026, 14:50 CET: The new version is approved and published on Opera’s Add-ons store.
An apology, and next steps
We apologize for the confusion and inconvenience that this incident caused, particularly to st333v. We appreciate his collaboration and patience while we worked to resolve the issue as quickly as possible.
We have addressed the bug that led to this development, and we are taking steps to ensure that incidents such as this are not repeated in the future.
The F.B.(FluffBusting)Purity add-on is fully restored on Opera’s Add-ons store and is safe to use, as it always has been.
We thank everyone for their patience and understanding.
Source: Opera statement on the F.B.(FluffBusting)Purity add-on false positive
Hasleo BitLocker Anywhere Professional 1yr for free
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Encryption Process & Functions
The encryption process in Hasleo BitLocker Anywhere follows a similar approach to Microsoft’s built-in BitLocker Drive Encryption.
Encrypt Drive: it detects and shows all the installed storage media on the PC. You can activate BitLocker Drive Encryption on a chosen drive by right-clicking on the drive.
Decrypt Drive: Similar to Encryption, you can right-click and select “Unlock Drive”. It’s also possible to do this on “This PC”.
Export Key: When encrypting a drive, it ask you to export the BitLocker recovery key, which is a unique code separate from your password. This key is essential if you ever forget your password or lose access to your decryption method.
The encryption process in Hasleo BitLocker Anywhere follows a similar approach to Microsoft’s built-in BitLocker Drive Encryption.
Encrypt Drive: it detects and shows all the installed storage media on the PC. You can activate BitLocker Drive Encryption on a chosen drive by right-clicking on the drive.
Decrypt Drive: Similar to Encryption, you can right-click and select “Unlock Drive”. It’s also possible to do this on “This PC”.
Export Key: When encrypting a drive, it ask you to export the BitLocker recovery key, which is a unique code separate from your password. This key is essential if you ever forget your password or lose access to your decryption method.
Features
- Encrypt Hard Drives and Data Partitions with BitLocker
- Decrypt BitLocker-Encrypted Drives
- Encrypt and Start Windows 7 with a password
- Encrypt and decrypt volumes larger than 2TB
- Export BitLocker recovery key and startup key
SoftOrbits AI Photo Editor for free
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Features
- Clean up distractions in your photos with a click of a button!
- Smart Select, Smart Mask, and Smart Background
- Remove objects such as distracting shadows, power poles or simply random passers-by.
- Tidy up your pictures
- Select and remove unwanted objects,
- Enhance photos automatically or under your supervision,
- sharpen up the details,
- leveling horizon
- Framing the picture just right.
- A fully featured toolbox of photo editing tools.
- Automatically fix small imperfections and correct the red-eye effect,
- Control brightness and contrast,
- Adjust white balance, Frame, rotate, flip and frame pictures
- Make your photo Web-ready
- Choosing all the right resolution, sharpening and compression settings
- Manage Your Photo Collection
- Scan through your photo collection,
- A convenient file manager
- Navigate through your entire photo collection
- Delete duplicates in just a few clicks.
Leawo Photo BG Remover 1yr for free
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Features of Leawo Photo BG Remover
- Automatically remove background from image in batch easily with smart algorithm.
- Manually remove photo background with practical tools.
- Erase background from image and isolate object to a transparent background.
- Change photo background to any solid color or photo.
- Remove background around hair, fur, feather, and more.
- Erase background from transparent objects.
- Easy to use and get started.
- No technical skills required.
- Mainstream graphic formats supported, including JPG, PNG, TIFF, WEBP, etc.
- Multilingual support.
Microsoft Develops Scanner to Detect Backdoors in Open-Weight Large Language Models
- Brownie2019
- Security News
- Replies: 1
Full Story:Microsoft on Wednesday said it built a lightweight scanner that it said can detect backdoors in open-weight large language models (LLMs) and improve the overall trust in artificial intelligence (AI) systems.
The tech giant's AI Security team said the scanner leverages three observable signals that can be used to reliably flag the presence of backdoors while maintaining a low false positive rate.
"These signatures are grounded in how trigger inputs measurably affect a model's internal behavior, providing a technically robust and operationally meaningful basis for detection," Blake Bullwinkel and Giorgio Severi said in a report shared with The Hacker News.
LLMs can be susceptible to two types of tampering: model weights, which refer to learnable parameters within a machine learning model that undergird the decision-making logic and transform input data into predicted outputs, and the code itself.

Microsoft Develops Scanner to Detect Backdoors in Open-Weight Large Language Models
Microsoft develops a lightweight scanner that detects backdoors in open-weight LLMs using three behavioral signals, improving AI model security and tr
 thehackernews.com
thehackernews.com
Microsoft rolls out native Sysmon monitoring in Windows 11
- Brownie2019
- Technology News
- Replies: 1
Story on:Microsoft has started rolling out built-in Sysmon functionality to some Windows 11 systems enrolled in the Windows Insider program.
Microsoft first revealed plans to integrate Sysmon natively into Windows 11 and Windows Server in November, when it also confirmed that it will soon release detailed documentation.
Sysmon (short for System Monitor) is a free Microsoft Sysinternals tool (and a Windows system service and device driver) that monitors for and blocks malicious/suspicious activity, logging it to the Windows Event Log.

Microsoft rolls out native Sysmon monitoring in Windows 11
Microsoft has started rolling out built-in Sysmon functionality to some Windows 11 systems enrolled in the Windows Insider program.
McAfee R136
- KnownStormChaser
- McAfee
- Replies: 1
After three months, McAfee has finally released the new version R136.
Here are the translated changes:
The Neo engine upgrade is now separate from the main program version upgrade; even if the main program hasn't been updated to R136, the Neo engine has already been upgraded to the latest version.
The new version of the Neo engine adds a PDF parsing module.
Here are the translated changes:
The Neo engine upgrade is now separate from the main program version upgrade; even if the main program hasn't been updated to R136, the Neo engine has already been upgraded to the latest version.
The new version of the Neo engine adds a PDF parsing module.
McAfee R136更新_McAfee_国外杀毒软件 卡饭论坛 - 互助分享 - 大气谦和!
帖子《McAfee R136更新》,,来自《McAfee》,国外杀毒软件,《卡饭论坛》
bbs.kafan.cn
Egypt blocks online platform Roblox over concerns about children’s online safety
- Parkinsond
- Technology News
- Replies: 11
Egypt’s Supreme Council for Media Regulation (SCMR) has decided to officially block the online gaming platform Roblox in Egypt, citing concerns over risks to children and adolescents, SCMR Vice Chairman Essam El-Amir announced on Sunday.
The move follows a proposal submitted days earlier by Senator Walaa Hermas Radwan, calling for the regulation of the electronic gaming platform Roblox to protect children’s moral and educational values, limit associated psychological and behavioural risks, and organize the operation of electronic gaming platforms more broadly.
Egypt would not be alone in taking action against the gaming platform Roblox, as several countries have previously moved to block, restrict, or regulate the platform over child-safety and content concerns.
Iraq and Algeria have imposed nationwide bans citing risks related to inappropriate content, online harassment, and exposure of minors to strangers, while access to Roblox is blocked in China under broader internet censorship regulations.
Turkey has also temporarily banned the platform pending stricter compliance with local content rules, and a number of Gulf countries, including Saudi Arabia and the UAE, have imposed limitations on features such as in-game chat and content moderation rather than a full ban.
Can We Talk About This Now? Shai-Hulud Wave 2 Targeting npm
- Khushal
- Security News
- Replies: 3
Shai-Hulud Wave 2 is here — and it’s far more destructive.
Back in September, Morphisec and Kaspersky warned that Wave 1 of this npm-targeting worm was just the beginning.
Now Wave 2 has arrived — and the escalation is dramatic:
25,000+ infected repositories
1,000 new infections every 30 minutes
Credential theft + destructive wiper behavior
Docker-based privilege escalation to root
Advanced persistence through GitHub workflows
This isn’t just an open-source issue.
It’s a software supply chain crisis — and detection tools alone simply can’t keep up.
If you work in software development, DevOps, security, or supply chain risk — this is a must-read.

Can We Talk About This Now? Shai-Hulud Wave 2 Targeting npm | Morphisec Blog
Shai-Hulud Wave 2 is here—and it’s more destructive than anyone expected. Explore how the npm-targeting malware evolved and why preemptive supply chain defense is critical.www.morphisec.com
Google took out a MASSIVE pool of residential proxies. Threat actors have been having a hard time ever since, whining in hacking forums.
- Khushal
- Security News
- Replies: 2
They are attempting to seek out new providers that don’t have KYC (Know Your Customer/Identity Verification)
This is a huge win for cybersecurity world-widewell done Google Threat Intelligence Group

Disrupting the World's Largest Residential Proxy Network | Google Cloud Blog
IPIDEA’s proxy infrastructure is a component of the digital ecosystem leveraged by a wide array of bad actors.cloud.google.com

Critical React Native Vulnerability Exploited in the Wild
- Miravi
- Security News
- Replies: 2
Threat actors have been exploiting a critical-severity React Native vulnerability in attacks since late December, VulnCheck warns.
Tracked as CVE-2025-11953 (CVSS score of 9.8) and disclosed in early November, the bug impacts the highly popular React Native Community CLI NPM package (@react-native-community/cli), which has roughly two million weekly downloads.
It is part of the React Native Community CLI project, which was extracted from the open source framework for improved maintainability, and provides a set of command-line tools for app building.
While CVE-2025-11953 and other vulnerabilities impacting development servers are typically exploitable only from the developer’s local machine, a second issue in React Native exposes the servers to external attackers, software supply chain security firm JFrog warned in November.
Now, VulnCheck mirrors the warning after observing in-the-wild exploitation of the CVE, despite limited public attention.
“As of late January, public discussion largely frames CVE-2025-11953 as a theoretical risk rather than an active intrusion vector. This disconnect is where defenders are most likely to be caught unprepared,” VulnCheck notes in a fresh report.
The vulnerability intelligence firm, which has named the bug Metro4Shell, observed initial exploitation attempts on December 21, followed by more activity on January 4 and 21, suggesting continuous operational use. Thousands of internet-accessible React Native instances could be at risk.
Critical React Native Vulnerability Exploited in the Wild
Threat actors are exploiting the Metro4Shell React Native vulnerability to deploy malware on Linux and Windows systems.
Hackers Leak 5.1 Million Panera Bread Records
- Miravi
- Security News
- Replies: 3
Data allegedly pertaining to over 5 million Panera Bread customers has emerged online after hackers failed to extort the US bakery-cafe chain.
The ShinyHunters extortion group has claimed the theft of roughly 14 million records from Panera Bread, after compromising a Microsoft Entra single-sign-on (SSO) code.
The attack falls in line with recent ShinyHunters attacks that rely on voice phishing (vishing) and SSO authentication to access victim organizations’ cloud-based software-as-a-service (SaaS) environments.
Last week, ShinyHunters published on its Tor-based leak site a 760GB archive allegedly containing the sensitive information stolen from Panera Bread.
According to the data breach notification site Have I Been Pwned, the data was leaked after the hackers failed to extort the food chain.
The archive includes 5.1 million unique email addresses and likely impacts as many Panera customers. Associated information such as names, addresses and phone numbers was also present in the leak.
While it has not responded to a SecurityWeek inquiry on the incident, Panera Bread has confirmed the intrusion, telling Reuters that the hackers stole “contact information”.
“From a defender’s perspective, 5.1 million compromised accounts still represents a massive downstream risk for credential stuffing, phishing, and identity-based attacks well beyond Panera itself,” SOCRadar CISO Ensar Seker said.
ShinyHunters-branded extortion attacks have been escalating recently, with recent reports suggesting the group was setting up to hit over 100 organizations across multiple sectors. Betterment, Crunchbase, and SoundCloud have confirmed the intrusions.

Hackers Leak 5.1 Million Panera Bread Records
The ShinyHunters extortion group has leaked 14 million records allegedly stolen from US bakery-cafe chain Panera Bread.
Foxit PDF Editor Vulnerabilities Let Attackers Execute Arbitrary JavaScript
- Parkinsond
- Security News
- Replies: 5
Security updates addressing critical cross-site scripting (XSS) vulnerabilities in Foxit PDF Editor Cloud that could allow attackers to execute arbitrary JavaScript code in users’ browsers.
The vulnerabilities were discovered in the application’s File Attachments list and Layers panel, where insufficient input validation and improper output encoding create pathways for malicious code execution.
The application fails to properly encode untrusted input before embedding it into the HTML structure, enabling arbitrary JavaScript execution within the user’s browser context.
An attacker exploiting these vulnerabilities could access sensitive information visible to the authenticated user, including document contents and session data.
Foxit has released security patches addressing both vulnerabilities as part of the February 3, 2026 update to Foxit PDF Editor Cloud.

Foxit PDF Editor Vulnerabilities Let Attackers Execute Arbitrary JavaScript
Foxit PDF Editor Cloud patches XSS flaws in File Attachments and Layers, preventing attackers from executing JavaScript in users’ browsers.cybersecuritynews.com
File Xterminator for free
- Brownie2019
- Giveaways, Promotions and Contests
- Replies: 0
Main Features:
1. Can find files on any folder on your Mac including system folders.
2. Recursive search of folders and sub-folders.
3. You can trash or remove files.
4. Disk space pie graphics representing real-time free and used disk space.
Extra Features:
1. Ability to search for a size range by setting minimum and maximum size of files to look for.
2. Precision on results. You know exactly what you are getting rid of.
3. Fast search.
Download:
1. Can find files on any folder on your Mac including system folders.
2. Recursive search of folders and sub-folders.
3. You can trash or remove files.
4. Disk space pie graphics representing real-time free and used disk space.
Extra Features:
1. Ability to search for a size range by setting minimum and maximum size of files to look for.
2. Precision on results. You know exactly what you are getting rid of.
3. Fast search.
Download:
MyMicroBalance Free
- Brownie2019
- Other software
- Replies: 1
The smart, free budget planner for everyone who wants to make more of their money. Clear, easy to use, for PC and smartphone – and now with AI-powered features.
 www.mymicrobalance.com
www.mymicrobalance.com
Free Budget Planner with PC & App Sync
MyMicroBalance is your private and free budget planner and financial planning software!
Spotify and Major Music Labels Sue Anna’s Archive for $13 Trillion
- Khushal
- Security News
- Replies: 1

Spotify and Major Music Labels Sue Anna’s Archive for $13 Trillion
Follow us on Bluesky, Twitter (X), Mastodon and Facebook at @Hackreadhackread.com
In September 2025, a pirate activist group known as Anna’s Archive successfully copied a gigantic amount of data from the world’s leading streaming platform.
Now, in an unprecedented move, Spotify has joined forces with the Big Three of the music world, Universal Music Group, Sony Music Entertainment, and Warner Music Group, to file a lawsuit against the group.
The price tag for the alleged theft? A jaw-dropping $13 trillion (around £10 trillion) in damages.
2026 OffSec EDR Tier List
- Khushal
- Video Reviews - Security and Privacy
- Replies: 16
OFFICIAL EDR Tier List for 2026! Based on nothing but the people in chat, vibes, guests, opinions and limited experience.
Someone wrote a PoC on how to turn off Defender EDR using AppLocker (even when AppLocker is not active)
- Khushal
- Security News
- Replies: 9
Threat actors could abuse AppLocker to deploy rules that will prevent EDR processes from execution in order to execute arbitrary commands and software on the asset without EDR disruption. Splunk identified a malware called “Azorult loader” back in 2022 that introduced this behaviour.

AppLocker Rules Abuse
AppLocker was introduced by Microsoft in Windows 7 to enable organizations to define which executables, scripts or installers are allowed to run in their environments. AppLocker can reduce the atta…
 ipurple.team
ipurple.team
Cyber Insights 2026: Malware and Cyberattacks in the Age of AI
- Brownie2019
- Security News
- Replies: 2
Read more on:The big takeaway from 2026 onward is the arrival and increasingly effective use of AI, and especially agentic AI, that will revolutionize the attack scenario. The only question is how quickly.
Michael Freeman, head of threat intelligence at Armis, predicts, “By mid-2026, at least one major global enterprise will fall to a breach caused or significantly advanced by a fully autonomous agentic AI system.”
These systems, he continues, “use reinforcement learning and multi-agent coordination to autonomously plan, adapt, and execute an entire attack lifecycle: from reconnaissance and payload generation to lateral movement and exfiltration. They continuously adjust their approach based on real-time feedback. A single operator will now be able to simply point a swarm of agents at a target.”
The UK’s NCSC is slightly more reserved: “The development of fully automated, end-to-end advanced cyberattacks is unlikely [before] 2027. Skilled cyber actors will need to remain in the loop. But skilled cyber actors will almost certainly continue to experiment with automation of elements of the attack chain…”
Both opinions could be accurate. We don’t yet know how the adversarial use of AI will pan out over the next few years. What we do know is that attacks will increase in volume, speed and targeting, assisted by artificial intelligence.
Malware, malicious attacks and AI

Cyber Insights 2026: Malware and Cyberattacks in the Age of AI
How AI and agentic AI are reshaping malware and malicious attacks, driving faster, stealthier, and more targeted campaigns—and what defenders can do to prepare.
Phishing Scam Uses Clean Emails and PDFs to Steal Dropbox Logins
- Brownie2019
- Security News
- Replies: 2
Full Story:A multi-stage phishing campaign is targeting business users by exploiting Vercel cloud storage, PDF attachments, and Telegram bots to steal Dropbox credentials.
If you have ever received a boring email about a business contract or a ‘request order,’ you might have clicked it without thinking twice. But a new report suggests that these routine messages are now part of a planned scam.
Cybersecurity researchers at Forcepoint have discovered a new phishing scam in which attackers are using a “multi-stage” process to stay invisible and achieve their true goal of stealing your login details.
Most email scams are caught by filters because they contain malicious links or viruses. This one is different. It starts with a professional-looking email, usually about a “tender” or “procurement” deal. The email itself is completely clean. It relies on a PDF attachment to do the dirty work.

Phishing Scam Uses Clean Emails and PDFs to Steal Dropbox Logins
Follow us on Bluesky, Twitter (X), Mastodon and Facebook at @Hackread
 hackread.com
hackread.com
Wilders Security Forums will NOT Moving to a New Domain Name [Updated]
- Spiff
- Member Chat
- Replies: 2
Wilders Security Forums is Moving to a New Domain Name
Malicious ClawdBot Skills Target ByBit, Polymarket, Axiom, Reddit and LinkedIn to Install Malware
- Khushal
- Security News
- Replies: 4
Unless you have been living under a rock, you’ve head of ClawdBot and its incredible rise to fame. ClawdBot is an open-source AI personal assistant that runs locally on your device and uses common chat messengers to manage all the things.
Executive Summary
An initial group of 28 malicious skills targeting Claude Code and Moltbot users were published to ClawHub and GitHub between January 27-29, 2026. A second larger group of 386 skills were published January 31-February 2. The skills masquerade as cryptocurrency trading automation tools and deliver information-stealing malware to macOS and Windows systems. All these skills share the same command-and-control infrastructure (91.92.242.30) and use sophisticated social engineering to convince users to execute malicious commands which then steals crypto assets like exchange API keys, wallet private keys, SSH credentials, and browser passwords.

OpenSourceMalware.com - Community Threat Intelligence
Security professionals sharing intelligence on malicious packages, repositories, and CDNs to protect the open source ecosystem.opensourcemalware.com

From Automation to Infection: How OpenClaw AI Agent Skills Are Being Weaponized
The fastest-growing personal AI agent ecosystem just became a new delivery channel for malware. Over the last few days, VirusTotal has detec...blog.virustotal.com
Infostealers without borders: macOS, Python stealers, and platform abuse (A report by Microsoft)
- Khushal
- Security News
- Replies: 1

Infostealers without borders: macOS, Python stealers, and platform abuse | Microsoft Security Blog
How modern infostealers target macOS systems, leverage Python‑based stealers, and abuse trusted platforms and utilities to distribute credential‑stealing payloads.www.microsoft.com
Infostealer threats are rapidly expanding beyond traditional Windows-focused campaigns, increasingly targeting macOS environments, leveraging cross-platform languages such as Python, and abusing trusted platforms and utilities to silently deliver credential-stealing malware at scale. Since late 2025, Microsoft Defender Experts has observed macOS targeted infostealer campaigns using social engineering techniques—including ClickFix-style prompts and malicious DMG installers—to deploy macOS-specific infostealers such as DigitStealer, MacSync, and Atomic macOS Stealer (AMOS).
These campaigns leverage fileless execution, native macOS utilities, and AppleScript automation to harvest credentials, session data, secrets from browsers, keychains, and developer environments. Simultaneously, Python-based stealers are being leveraged by attackers to rapidly adapt, reuse code, and target heterogeneous environments with minimal overhead. Other threat actors are abusing trusted platforms and utilities—including WhatsApp and PDF converter tools—to distribute malware like Eternidade Stealer and gain access to financial and cryptocurrency accounts.
APT28 Leverages CVE-2026-21509 in Operation Neusploit
- Khushal
- Security News
- Replies: 1
In January 2026, Zscaler ThreatLabz identified a new campaign in-the-wild, tracked as Operation Neusploit, targeting countries in the Central and Eastern European region. In this campaign, the threat actor leveraged specially crafted Microsoft RTF files to exploit CVE-2026-21509 and deliver malicious backdoors in a multi-stage infection chain. Due to significant overlaps in tools, techniques, and procedures (TTPs) between this campaign and those of the Russia-linked advanced persistent threat (APT) group APT28, we attribute this new campaign to APT28 with high confidence. Microsoft released an out-of-band update to address CVE-2026-21509 on January 26, 2026. ThreatLabz observed active in-the-wild exploitation on January 29, 2026.
The Chrysalis Backdoor: A Deep Dive into Lotus Blossom’s toolkit, investigation identified a security incident stemming from Notepad++
- Khushal
- Security News
- Replies: 2
Rapid7 Labs, together with the Rapid7 MDR team, has uncovered a sophisticated campaign attributed to the Chinese APT group Lotus Blossom. Active since 2009, the group is known for its targeted espionage campaigns primarily impacting organizations across Southeast Asia and more recently Central America, focusing on government, telecom, aviation, critical infrastructure, and media sectors.
Our investigation identified a security incident stemming from a sophisticated compromise of the infrastructure hosting Notepad++, which was subsequently used to deliver a previously undocumented custom backdoor, which we have dubbed Chrysalis.
The Chrysalis Backdoor: A Deep Dive into Lotus Blossom’s toolkit
Rapid7 Labs, together with the Rapid7 MDR team, has uncovered a sophisticated campaign attributed to the Chinese APT group Lotus Blossom.
www.rapid7.com
PCMatic Antivirus Home 2026
- Shadowra
- Video Reviews - Security and Privacy
- Replies: 9
PC Matic Antivirus is a U.S.-based security solution designed to proactively protect PCs from malware, ransomware, and zero-day threats. Its main strength lies in application whitelisting, which blocks unknown and untrusted programs before they can run.
Let's take a look!
A huge thank you to for @danb buying it! (Without him, we wouldn't have been able to test it.)
Interface :
The product interface is fairly clear and well organized. There are no settings available, which is good for novices but not suitable for power users who are crazy about configuration.
However, you will need to create an account after payment (PCMatic is not available in a trial version... why?) and log in with your account, otherwise the antivirus will not start.
It also has an anti-scam feature and an ad blocker extension (it's Ublock Origin...).
Web protection: 10/10
PCMatic blocks all malicious launches I attempt. One file is damaged (CobaltStrike) and therefore not counted.
Too bad, I didn't see the anti-malware engine… (except on Defender Control ^^ )
Fake crack : N/A
The sample is too old and the site that distributed it was down.
Skipped.
Malware Pack : It is impossible to know the rest. PC Matic does NOT analyze the archive!
So I had to manually launch the 130 samples in my pack.
Overall, it's pretty good. PCMatic blocks SuperShield as an anti-executable but lets MSI installations through.
A script was even able to launch Powershell undetected to install a Trojan horse, without any reaction.
The only two reactions from the “antivirus” were when I ran a RAT, and it offered to delete it. Otherwise, I never saw PCMatic's antimalware engine...
Final scan :
PCMatic : 0
NPE : 2
KVRT : 5

Final opinion:
It's difficult to judge PCMatic.
In itself, the protection it provides is pretty good, especially thanks to SuperShield, which does a great job.
However, several gray areas cloud the picture:
- I don't really appreciate being forced to purchase before testing. It clearly smacks of “crapware,” and it's a practice I hate.
- The anti-malware engine never reacted, except twice when I launched a RAT. Otherwise, only SuperShield intervened.
- A quick scan that checks the network, then empties the temporary files, then checks for updates, etc. It would have been better to offer several scans rather than grouping everything together. Sure, it's better for a novice, but when you just want to do a quick antimalware scan, it should just offer that...
For me, PCMatic is not an antivirus, but rather a supplement.
@annaegorov request
Let's take a look!
A huge thank you to for @danb buying it! (Without him, we wouldn't have been able to test it.)
Interface :
The product interface is fairly clear and well organized. There are no settings available, which is good for novices but not suitable for power users who are crazy about configuration.
However, you will need to create an account after payment (PCMatic is not available in a trial version... why?) and log in with your account, otherwise the antivirus will not start.
It also has an anti-scam feature and an ad blocker extension (it's Ublock Origin...).
Web protection: 10/10
PCMatic blocks all malicious launches I attempt. One file is damaged (CobaltStrike) and therefore not counted.
Too bad, I didn't see the anti-malware engine… (except on Defender Control ^^ )
Fake crack : N/A
The sample is too old and the site that distributed it was down.
Skipped.
Malware Pack : It is impossible to know the rest. PC Matic does NOT analyze the archive!
So I had to manually launch the 130 samples in my pack.
Overall, it's pretty good. PCMatic blocks SuperShield as an anti-executable but lets MSI installations through.
A script was even able to launch Powershell undetected to install a Trojan horse, without any reaction.
The only two reactions from the “antivirus” were when I ran a RAT, and it offered to delete it. Otherwise, I never saw PCMatic's antimalware engine...
Final scan :
PCMatic : 0
NPE : 2
KVRT : 5
Final opinion:
It's difficult to judge PCMatic.
In itself, the protection it provides is pretty good, especially thanks to SuperShield, which does a great job.
However, several gray areas cloud the picture:
- I don't really appreciate being forced to purchase before testing. It clearly smacks of “crapware,” and it's a practice I hate.
- The anti-malware engine never reacted, except twice when I launched a RAT. Otherwise, only SuperShield intervened.
- A quick scan that checks the network, then empties the temporary files, then checks for updates, etc. It would have been better to offer several scans rather than grouping everything together. Sure, it's better for a novice, but when you just want to do a quick antimalware scan, it should just offer that...
For me, PCMatic is not an antivirus, but rather a supplement.
@annaegorov request
Giving away 7 AVG Ultimate keys free includes Internet Security, Unlimited VPN, and TuneUP.
- nickstar1
- Member Chat
- Replies: 7
The first 7 users to private message me asking for the keys will receive them. This is first come, first served, just like all of my giveaways. No private data needed you get the key and your able to activate the product. When the giveaway is complete ill notify moderation by flagging the post with a comment when it's done.
Feb 2026 conclusion?
- DarkJoney
- Software Comparison
- Replies: 37
Hi folks,
Happy to be back to Windows after year of struggle on "the best" macOS.
Then, the question is it's time to refresh my AV positioning. I used mainly Bitdefender and Avira in the last 10 years. I need something to cover my back on my Zephyrus G16 and as I see Bitdefender is not a bulletproof choice anymore.
I am advanced user, not afraid of anything.
Currently, the choice is between:
Bitdefender Total
Emsisoft
Trend Micro
ZoneAlarm Extreme
ESET
Norton 360
or again even AVIRA or Ikarus???
At Nostromo's from comss.ru tests ZoneAlarm and TrendMicro look better than Bitdefender or ESET.
I would appreciate good online protection (despite I use piHole), strong behaviour block, PUP cleaner, sandbox is a plus, strong ransomware detect (since I have lot's of media despite 1-2-3 backups) and that it will not burn out the battery Good license offer on some ebay or key website is also a plus.
Good license offer on some ebay or key website is also a plus.
ASUS is actually comes with McAfee, but dunno.
What's is your opinion? Basically, I want a thing with no compromise.
PLEASE DON'T OFFER KASPERSKY OR DR.WEB, THANKS IN ADVANCE
p.s. sorry to the mods if wrong thread
Happy to be back to Windows after year of struggle on "the best" macOS.
Then, the question is it's time to refresh my AV positioning. I used mainly Bitdefender and Avira in the last 10 years. I need something to cover my back on my Zephyrus G16 and as I see Bitdefender is not a bulletproof choice anymore.
I am advanced user, not afraid of anything.
Currently, the choice is between:
Bitdefender Total
Emsisoft
Trend Micro
ZoneAlarm Extreme
ESET
Norton 360
or again even AVIRA or Ikarus???
At Nostromo's from comss.ru tests ZoneAlarm and TrendMicro look better than Bitdefender or ESET.
I would appreciate good online protection (despite I use piHole), strong behaviour block, PUP cleaner, sandbox is a plus, strong ransomware detect (since I have lot's of media despite 1-2-3 backups) and that it will not burn out the battery
ASUS is actually comes with McAfee, but dunno.
What's is your opinion? Basically, I want a thing with no compromise.
PLEASE DON'T OFFER KASPERSKY OR DR.WEB, THANKS IN ADVANCE
p.s. sorry to the mods if wrong thread
The most reliable PC hardware of 2025, according to Puget Systems
- Gandalf_The_Grey
- Technology News
- Replies: 3
System integrator Puget Systems has released its annual reliability report for 2025, revealing which PC hardware brands and models proved most reliable throughout the year. In the consumer CPU space two series sat above the rest: the AMD Ryzen 9000 and Intel Core 200, but an outright winner wasn't crowned.
Puget writes that it bases its reliability report on internal burn-in results and RMA records. The company stresses that its stricter standards mean the failure rates may be higher than industry standards and the information is based on its own systems, so it doesn't represent the industry as a whole.
Starting with enterprise processors, Intel stole the most-reliable title from AMD's Threadripper and Threadripper PRO lines in 2025. Impressively, none of the Xeon W-2500 or W-3500 processors Puget sold had recorded failures in 2025. The company adds that only a single Xeon W CPU saw a failure in 2024, too.
Moving on to the consumer side, the Ryzen 9000 and Intel Core 200 had almost identical failure rates of 2.52% and 2.49%, respectively. While Team Blue has the lower rate, Puget writes that the difference is too close to be statistically significant.
There were a couple of standouts within the companies' respective lines: Intel's Core Ultra 7 265K, which had a failure rate of just 0.77%, and AMD's Ryzen X3D series, which saw a 1.5% failure rate. It's also noted that the vast majority of these failures were caught before systems shipped to customers.
Puget also looked at the most reliable GPUs of last year. While Asus' ProArt and TUF GPUs were the champions of 2024, Puget did not sell enough models from specific product lines in to consider them individually. Instead, the retailer looked at the manufacturer level.
Featured content
-
Thread 'Free Antivirus Vs Paid Antivirus – Do You Really Need To Pay In 2026?'
- Parkinsond
Replies: 17 -
-
Trending content
-
-
-
N
-
-
