- Mar 29, 2018
- 8,061
Hello Adrian Ścibor,
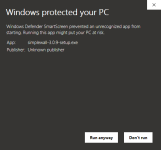
Except when it is important. WD is not like any AV because it is a part of built-in Windows security. For example, Microsoft cannot suggest/force users to install WDBP if they install Chrome. Other AVs can do it.
Not in the real-world scenario, which is most important for the home users who are the main customers of free AVs. The CheckLab testing methodology is interesting but can silently invalidate the protection of some free AVs (WD "Block at First Sight" or Avast CyberCapture).
The testing methodology is questionable for Avast and WD (even with Edge / Chromium), because some important AV features are bypassed in the real-world scenario (CyberCapture and Block at First Sight).
It is obviously not the right point of view for any AV which was made to work with Windows built-in browsers (Edge or IE) protected by SmartScreen.
So, It would be better to not test WD (and probably Avast) in such a test.
If you will drop the web/browser protection part in your test, then it will be similar to the AV-Comparatives "Malware Protection Test". Such a test is focused on the malware delivered from network drives, USB or cover scenarios where the malware is already on the disk.
In this type of test, the AV features (including Avast and WD) are not invalidated.
The CheckLab testing methodology is interesting. But, there is no need to test AVs which does not fit the testing methodology.
Edit.
It is good that someone in my country decided to face in a professional way the extremely complex and demanding AV testing problem.
Thanks for your detailed reply. I always learn so much from your posts.