Hi and welcome to MalwareTips!

I'm Fiery and I would gladly assist you in removing the malware on your computer.
PLEASE NOTE: The first 3 posts of ALL new members require approval by mods/admins. Please be patient if you don't see your post immediately after submitting it.
Before we start:
- Note that the removal process is not immediate. Depending on the severity of your infection, it could take a long time.
- Malware removal can be dangerous. I cannot guarantee the safety of your system as malware can be unpredictable. It is possible that we might encounter situations where the only recourse is to re-format and re-install your operating system. Therefore, I would advise you to backup all your important files before we start.
- Please be patient and stay with me until I give you the green lights and inform you that your PC is clean.
- Some tools may be flagged by your antivirus as harmful. Rest assure that ALL the tools we use are safe, the detections are false positives.
- The absence of symptoms does not mean your PC is fully disinfected.
- If you are unclear about the instructions, please stop and ask. Following the steps in the order that I post them in is vital.
- Lastly, if you have requested help on other sites, that will delay and hinder the removal process. Please only stick to one site.
<hr>
On another PC, open notepad and copy & paste the following:
start
HKU\D1DDY\...\Run: [qcgce2mrvjq91kk1e7pnbb19m52fx] - C:\Users\D1DDY\AppData\Local\Temp\vaidqvjcjtbwqfuof.exe [59904 2013-08-11] (Valve) <===== ATTENTION
C:\Users\D1DDY\AppData\Local\Temp\vaidqvjcjtbwqfuof.exe
HKU\D1DDY\...\Run: [SearchProtect] - C:\Users\D1DDY\AppData\Roaming\SearchProtect\bin\cltmng.exe [2852640 2013-05-07] (Conduit)
HKLM-x32\...\Run: [SearchProtectAll] - C:\Program Files (x86)\SearchProtect\bin\cltmng.exe [2852640 2013-05-07] (Conduit)
C:\Users\D1DDY\AppData\Roaming\SearchProtect
C:\Program Files (x86)\SearchProtect
HKU\D1DDY\...\Winlogon: [Shell] cmd.exe [345088 2010-11-20] (Microsoft Corporation) <==== ATTENTION
HKU\D1DDY\...\Command Processor: "C:\Users\D1DDY\AppData\Local\Temp\vaidqvjcjtbwqfuof.exe" <===== ATTENTION!
2013-08-11 07:09 - 2013-08-11 07:09 - 01328194 _____ C:\ProgramData\2433f433
2013-08-11 07:09 - 2013-08-11 07:09 - 01328173 _____ C:\Users\D1DDY\AppData\Local\2433f433
2013-08-11 07:09 - 2013-08-11 07:09 - 01328116 _____ C:\Users\D1DDY\AppData\Roaming\2433f433
C:\Windows\svchost.exe
end
and save it as
fixlist.txt onto your flash drive.
Then, boot to system recovery, plug in your flash drive, open FRST and click
fix. Post the generated log.
Attempt to boot normally. If successful,
Download
Malwarebytes Anti-Rootkit from
here to your Desktop
- Unzip the contents to a folder on your Desktop.
- Open the folder where the contents were unzipped and run mbar.exe
- Follow the instructions in the wizard to update and allow the program to scan your computer for threats.
- Make sure there is a check next to Create Restore Point and click the Cleanup button to remove any threats. Reboot if prompted to do so.
- After the reboot, perform another scan with Malwarebytes Anti-Rootkit to verify that no threats remain. If there are threats, click Cleanup once more and reboot.
- When done, please post the two logs in the MBAR folder(mbar-log.txt and system-log.txt)
Download TDSSkiller from
here
- Double-Click on TDSSKiller.exe to run the application
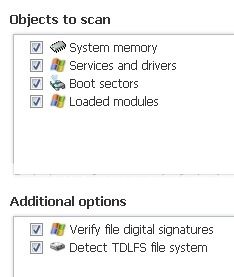
- When TDSSkiller opens, click change parameters , check the box next to Loaded modules . A reboot will be required.
- After reboot, TDSSKiller will run again. Click Change parameters again and make sure everything is checked.
- click Start scan .
- If a suspicious object is detected, the default action will be Skip, click on Continue. (If it saids TDL4/TDSS file system, select delete)
- If malicious objects are found, ensure Cure (default) is selected, then click Continue and Reboot now to finish the cleaning process.
Post the log after (usually
C:\ folder in the form of
TDSSKiller.[Version]_[Date]_[Time]_log.txt