D
Deleted member 178
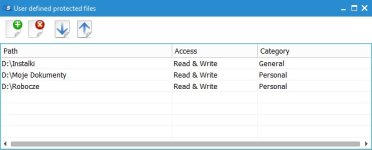
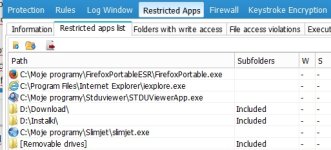
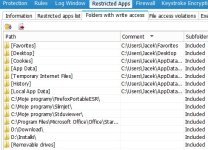
Many companies uses classic suites like everybody else but the enterprise version which gives more control over the system and allow management of several machine at same time, they do because it is simple to setup, also all depend on how skilled is the sysadmin, the security requirement of the company, the financial resources allowed on security, etc...@Umbra Is this config used by company's like Emsisoft or they create their special one.
I just want to know how industry uses protection suites nothing else.
I know some companies using only Windows Enterprise's built-in security, setting it via Group Policies and Applocker (an SRP) to secure each machine and using hardware appliances to secure the whole network. Those company won't use any AV or security softs.
Last edited by a moderator: