This sample was found @McMcbrad
We, that is @upnorth, @McMcbrad and me, have already started looking into this. We decided to continue in a public forum thread. I will use this first post as compilation what we found so far and keep updating it with new information.
@McMcbrad extracted the following URL from a weaponized document which is were the sample is from: VirusTotal
Unfortunately we don't have this document. The first part of the infection chain that I found is a dropper.
The malware has a rather long infection chain. Outline:
1. Trojan Dropper: Browes.exe
Overview
VT: VirusTotal
File type: PE32, SFX file
Compile time: 2020-03-26 10:02:47
First submission: 2020-10-26 07:57:33
Behaviour
Dropper for 1.exe
2. Trojan Dropper: 1.exe
Overview
VT: VirusTotal
File type: Windows Cabinet file
Compile time: 2013-10-14 06:48:22
First submission: 2020-10-26 11:33:06
Behaviour
Dropper for cheats.exe and a CryptoTab Setup file
CryptoTab setup: VirusTotal
^This file is not malicious and probably used as a lure.
3. Downloader cheats.exe
Overview
VT: VirusTotal
File type: PE 32
Compiler: JPHP
Any.run: cheats.exe (MD5: DAE90AE7FE103FC7E1866B4E13389101) - Interactive analysis - ANY.RUN
SHA256: 0161540edfceb643389a28ebe7d1092639596325e8f40defe52192ab999d3d36
Behaviour
Downloads klient.exe, saves it in :
4. Backdoor klient.exe
Overview
URL: hxxp://malina1306.zzz(.)com.ua/klient(.)exe
File type: PE 32
Compiler: JPHP
Compilation date: 2020-10-17 10:55:16
SHA256: cebee34d5f0292befca058537bf2320dd1492afa26fb9af471155c9332046320
VT: (3/71) VirusTotal
Malware type: Backdoor, controlled via C&C
C&C servers: hxxp://malina1306.zzz.com(.)ua and hxxp://bests.zzz.com(.)ua
Behaviour
Will check files on C&C server and do actions depending on their contents.
Downloads, among others, klip.exe (coinminer downloader) and stel.exe (stealer).
Similar samples
VT relations tab shows that at least 2 more files have been provided by that URL. They are slightly different versions of the same threat.
Files provided by hxxp://malina1306.zzz(.)com.ua/klient(.)exe
(3/69) VirusTotal
(4/69) VirusTotal
5. Coinminer downloader klip.exe
Overview
This was the first sample we analyzed, but it is not the main sample.
Hosting URL: hxxp://malina1306.zzz(.)com.ua/klip.exe
File type: PE 32
Compiler: JPHP
Compilation date: 2020-11-05 19:28:34
SHA256: 06a10cf99cc7c2d2ebc3e41300404e8f5816eb31a869d22835ade3a381199c0b
Any.Run:
 app.any.run
Malware type: Coinminer downloader
app.any.run
Malware type: Coinminer downloader
Behaviour
The sample downloads and drops this coinminer: VirusTotal
The download URL: hxxp://malina1306.zzz(.)com.ua/p/Winlogin(.)exe
The drop location: %TEMP%/Winlogin.exe
Downloads the coinminer's config (JSON file):
MMMMMM.MMMM --> c0a3b67b4056aeefd086edbe0c6ccb5fa7835505ef4ebe6220e5f914012e9e32
Also downloads and drops WinRing0.sys VirusTotal
Download URL: hxxp://malina1306.zzz(.)com.ua/p/WinRing0x64(.)sys
This file is no malware in itself but it seems to be abused by malware.
6. Stealer stel.exe
Overview
VT: (49/70) VirusTotal
Hosting URL: hxxp://malina1306.zzz(.)com.ua/stel.exe
File type: PE 32
Compiler: PyInstaller
Compilation date: 2020-08-08 12:30:37
Contact URLs: rudy.zzz(.)com.ua and malina1306.zzz(.)com.ua
Malware type: Credential stealer
Behaviour
Steals credentials:
7. Attribution
@upnorth suspects a relationship to Olympic Destroyer due to the file name for the dropped file: Winlogin.exe
Comparing with Checkpoint research: New Strain of Olympic Destroyer Droppers - Check Point Research
Note: I removed attribution info that has no proof for a connection.
8. Older versions
klip.exe:
http://invalid666.zzz.com.ua/klip.exe - Interactive analysis - ANY.RUN
IceRat.exe:
 app.any.run
hxxp://quarini.zzz.com(.)ua/Ice/
app.any.run
hxxp://quarini.zzz.com(.)ua/Ice/
--> we took the name of this malware from this sample
JPHP Decompilation Notes
JPHP is a PHP implementation for the Java VM. Github page: jphp-group/jphp
There is no decompiler for this, afaik.
What I found out you can do:
9. Hosting Domain
URL: hxxp://malina1306.zzz(.)com.ua
WHOIS: Whois Lookup Captcha
Translation of picture below (see spoiler):
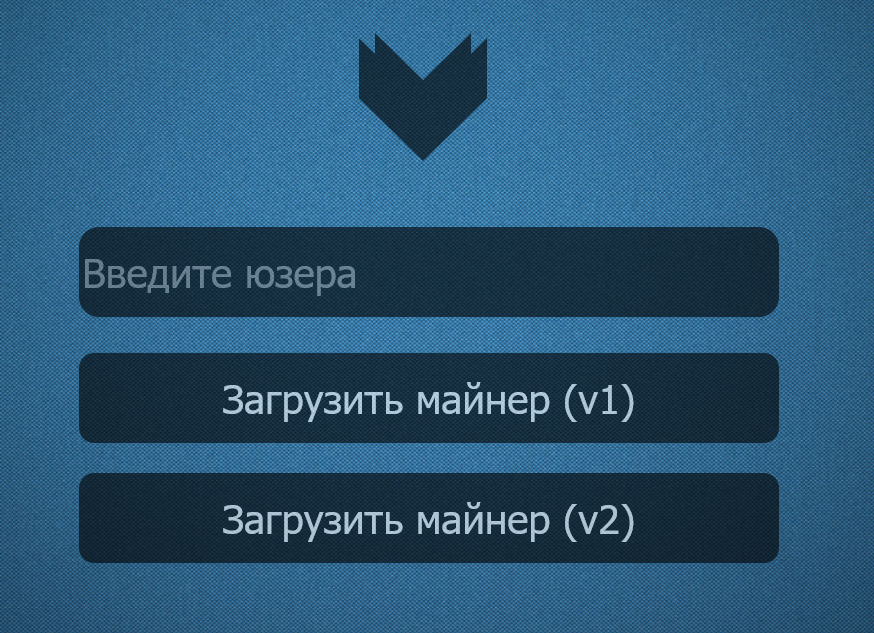 More files hosted on that page:
More files hosted on that page:
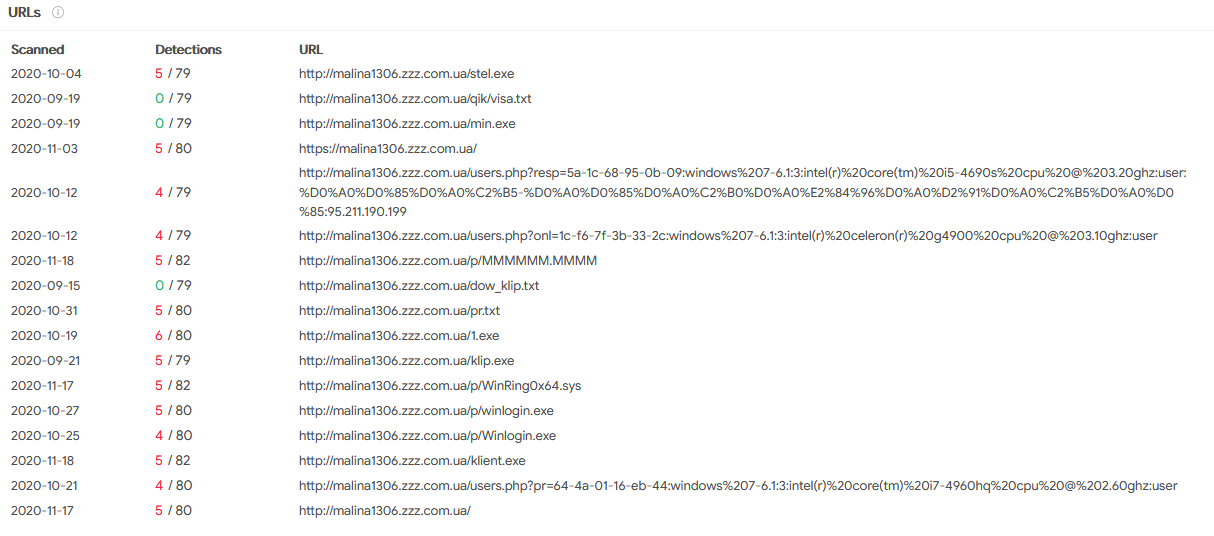
I freshly downloaded those:
visa.txt: empty
min.exe: NA
1.exe: (2/71) VirusTotal
klient.exe: (3/71) VirusTotal
klip.exe: 06a10cf99cc7c2d2ebc3e41300404e8f5816eb31a869d22835ade3a381199c0b (our sample)
winlogin.exe: NA
Winlogin.exe: (41/72) VirusTotal (coinminer)
stel.exe: (49/70) VirusTotal (PyInstaller compiled stealer)
MMMMMM.MMMM: c0a3b67b4056aeefd086edbe0c6ccb5fa7835505ef4ebe6220e5f914012e9e32 (JSON file with miner configuration)
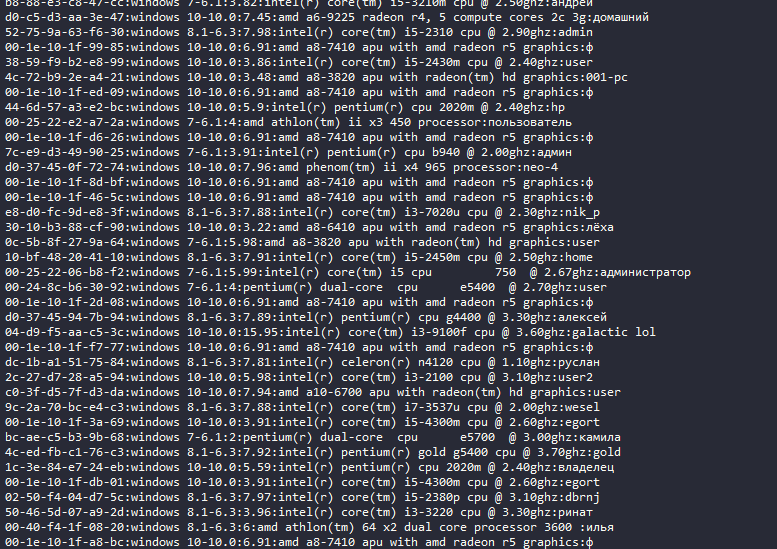
dow_klip.txt: ba049d910ceccfd69af1df754fa4d9a23c7b9165cb2eb66b375ca195531bee2a (infected client data)
pr.txt: dd34bde50b956333b0d154ef88036b5b596b3952311ac46d8b98470590da96e2 (infected client data)
--> both files contain a listing with tuplets of of MAC address, operating system, RAM, processor, username (a lot of them Russian). I suspect these are infected clients.
We, that is @upnorth, @McMcbrad and me, have already started looking into this. We decided to continue in a public forum thread. I will use this first post as compilation what we found so far and keep updating it with new information.
@McMcbrad extracted the following URL from a weaponized document which is were the sample is from: VirusTotal
Unfortunately we don't have this document. The first part of the infection chain that I found is a dropper.
The malware has a rather long infection chain. Outline:
Code:
Browes --> 1.exe --> cheats.exe --> klient.exe --> stel.exe
| |
CryptoTabSetup klip.exe --> Winlogin.exe
| \
MMMMMM.MMMM WinRing0x64.sys1. Trojan Dropper: Browes.exe
Overview
VT: VirusTotal
File type: PE32, SFX file
Compile time: 2020-03-26 10:02:47
First submission: 2020-10-26 07:57:33
Behaviour
Dropper for 1.exe
2. Trojan Dropper: 1.exe
Overview
VT: VirusTotal
File type: Windows Cabinet file
Compile time: 2013-10-14 06:48:22
First submission: 2020-10-26 11:33:06
Behaviour
Dropper for cheats.exe and a CryptoTab Setup file
CryptoTab setup: VirusTotal
^This file is not malicious and probably used as a lure.
3. Downloader cheats.exe
Overview
VT: VirusTotal
File type: PE 32
Compiler: JPHP
Any.run: cheats.exe (MD5: DAE90AE7FE103FC7E1866B4E13389101) - Interactive analysis - ANY.RUN
SHA256: 0161540edfceb643389a28ebe7d1092639596325e8f40defe52192ab999d3d36
Behaviour
Downloads klient.exe, saves it in :
- %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\<random_name>.exe
- %TEMP%\<random_name>.exe
- System
- WindowsShell
- exploler
- antiDrw
- antiSsl
- ADB
- Microsoft
- system
4. Backdoor klient.exe
Overview
URL: hxxp://malina1306.zzz(.)com.ua/klient(.)exe
File type: PE 32
Compiler: JPHP
Compilation date: 2020-10-17 10:55:16
SHA256: cebee34d5f0292befca058537bf2320dd1492afa26fb9af471155c9332046320
VT: (3/71) VirusTotal
Malware type: Backdoor, controlled via C&C
C&C servers: hxxp://malina1306.zzz.com(.)ua and hxxp://bests.zzz.com(.)ua
Behaviour
Will check files on C&C server and do actions depending on their contents.
Downloads, among others, klip.exe (coinminer downloader) and stel.exe (stealer).
Similar samples
VT relations tab shows that at least 2 more files have been provided by that URL. They are slightly different versions of the same threat.
Files provided by hxxp://malina1306.zzz(.)com.ua/klient(.)exe
(3/69) VirusTotal
(4/69) VirusTotal
5. Coinminer downloader klip.exe
Overview
This was the first sample we analyzed, but it is not the main sample.
Hosting URL: hxxp://malina1306.zzz(.)com.ua/klip.exe
File type: PE 32
Compiler: JPHP
Compilation date: 2020-11-05 19:28:34
SHA256: 06a10cf99cc7c2d2ebc3e41300404e8f5816eb31a869d22835ade3a381199c0b
Any.Run:

Analysis klip.exe (MD5: CEBD4B8468EE89E804BE61D091247540) Malicious activity - Interactive analysis ANY.RUN
Interactive malware hunting service. Live testing of most type of threats in any environments. No installation and no waiting necessary.
Behaviour
The sample downloads and drops this coinminer: VirusTotal
The download URL: hxxp://malina1306.zzz(.)com.ua/p/Winlogin(.)exe
The drop location: %TEMP%/Winlogin.exe
Downloads the coinminer's config (JSON file):
MMMMMM.MMMM --> c0a3b67b4056aeefd086edbe0c6ccb5fa7835505ef4ebe6220e5f914012e9e32
Also downloads and drops WinRing0.sys VirusTotal
Download URL: hxxp://malina1306.zzz(.)com.ua/p/WinRing0x64(.)sys
This file is no malware in itself but it seems to be abused by malware.
6. Stealer stel.exe
Overview
VT: (49/70) VirusTotal
Hosting URL: hxxp://malina1306.zzz(.)com.ua/stel.exe
File type: PE 32
Compiler: PyInstaller
Compilation date: 2020-08-08 12:30:37
Contact URLs: rudy.zzz(.)com.ua and malina1306.zzz(.)com.ua
Malware type: Credential stealer
Behaviour
Steals credentials:
- Firefox
- Yandex browser
- Filezilla
- Chrome
- Amigo
- kometa
- Orbitum
- Chromium
- K-Melon
7. Attribution
@upnorth suspects a relationship to Olympic Destroyer due to the file name for the dropped file: Winlogin.exe
Comparing with Checkpoint research: New Strain of Olympic Destroyer Droppers - Check Point Research
Note: I removed attribution info that has no proof for a connection.
8. Older versions
klip.exe:
http://invalid666.zzz.com.ua/klip.exe - Interactive analysis - ANY.RUN
IceRat.exe:

Analysis IceRat.exe (MD5: 5E864667D91E3867A29DF90DBCADB6B2) Malicious activity - Interactive analysis ANY.RUN
Interactive malware hunting service. Live testing of most type of threats in any environments. No installation and no waiting necessary.
--> we took the name of this malware from this sample
JPHP Decompilation Notes
JPHP is a PHP implementation for the Java VM. Github page: jphp-group/jphp
There is no decompiler for this, afaik.
What I found out you can do:
- Use 7zip to extract contents
- open files with .phb extension in a hex editor
- delete data up to the 0xCAFEBABE magic bytes, save result as .class file
- use, e.g., Fernflower to decompile .class files to Java code
9. Hosting Domain
URL: hxxp://malina1306.zzz(.)com.ua
WHOIS: Whois Lookup Captcha
Translation of picture below (see spoiler):
Enter User
Download miner (v1)
Download miner (v2)
I freshly downloaded those:
visa.txt: empty
min.exe: NA
1.exe: (2/71) VirusTotal
klient.exe: (3/71) VirusTotal
klip.exe: 06a10cf99cc7c2d2ebc3e41300404e8f5816eb31a869d22835ade3a381199c0b (our sample)
winlogin.exe: NA
Winlogin.exe: (41/72) VirusTotal (coinminer)
stel.exe: (49/70) VirusTotal (PyInstaller compiled stealer)
MMMMMM.MMMM: c0a3b67b4056aeefd086edbe0c6ccb5fa7835505ef4ebe6220e5f914012e9e32 (JSON file with miner configuration)
dow_klip.txt: ba049d910ceccfd69af1df754fa4d9a23c7b9165cb2eb66b375ca195531bee2a (infected client data)
pr.txt: dd34bde50b956333b0d154ef88036b5b596b3952311ac46d8b98470590da96e2 (infected client data)
--> both files contain a listing with tuplets of of MAC address, operating system, RAM, processor, username (a lot of them Russian). I suspect these are infected clients.
Last edited: