@NoVirusThanks I have an old computer with free OSArmor 1.4.3.0 installed to this day and it is working, protecting many years ago when I received email attachments and macros, several alert windows popped up and processes were blocked. Very good your products.
NoVirusThanks OSArmor
- Thread starter Evjl's Rain
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Here is the first blog from OSArmor. It is a good one! Always a helpful reminder not to click away at every little thing. Thanks, a nice (and very short) read. 
 blog.osarmor.com
blog.osarmor.com
Of course, it seems crucial to have a content blocker also or the browser configured accordingly.

Searching a Software? Be Aware Where You Click, You May Get Malware | OSArmor Blog
It looks like there is a massive ongoing malvertising campaign on Google Ads of search results that targets users looking to download popular software
Mostly all fake installers we have found were in .ZIP, .RAR, .EXE or .MSI file extensions.
Of course, it seems crucial to have a content blocker also or the browser configured accordingly.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Here is a pre-release test 7 version of OSArmor PERSONAL v1.8.2:

 www.wilderssecurity.com
www.wilderssecurity.com
Here is what's new compared to previous build:
+ Improved Password-protect power options with Windows Admin Credentials
You can install over-the-top, reboot is not needed.
Let me know if you find issues or FPs.
NoVirusThanks OSArmor: An Additional Layer of Defense
Planning to include the build number in the changelog (easier than editing the GUI every time). Perfect, thanks alot! :thumb:
@NoVirusThanks
I have a problem. OSArmor refuses the password to disable protection or access configurator when I am joined to a domain. I have done image restores and tried both account based password as well as plain password. In both cases it refuses to acknowledge the password. I will try test7 and see how it goes. I am still on test6.
EDIT: Just tried out test7. Thanks for the fixes. Now domain accounts work. I can disable protection. However I cannot open configurator from domain standard account. Is that deliberate?
I have a problem. OSArmor refuses the password to disable protection or access configurator when I am joined to a domain. I have done image restores and tried both account based password as well as plain password. In both cases it refuses to acknowledge the password. I will try test7 and see how it goes. I am still on test6.
EDIT: Just tried out test7. Thanks for the fixes. Now domain accounts work. I can disable protection. However I cannot open configurator from domain standard account. Is that deliberate?
Last edited:
G
Guilhermesene
Would be keen on SysHardner multiyear license too
G
Guilhermesene
@NoVirusThanks
I have a question about the product: I use Total Commander as the operating system's file manager, however, when I use OSarmor (activating the list of trusted suppliers), even with this option active, I can run any executable through TCMD normally. that is from an off-list vendor. The question is, does OSarmor (trusted vendor list) only work if you are using Windows Explorer?
I have a question about the product: I use Total Commander as the operating system's file manager, however, when I use OSarmor (activating the list of trusted suppliers), even with this option active, I can run any executable through TCMD normally. that is from an off-list vendor. The question is, does OSarmor (trusted vendor list) only work if you are using Windows Explorer?
We've released OSArmor v1.8.2:
Here is the changelog:
If you have automatic updates enabled then OSArmor should auto-update in the next hours.
Else you can install it "over-the-top" of the installed version, reboot is not needed.
* If you used test builds you should manually update to this final version (install over-the-top is fine).
If you find false positives or issues please let me know.
A few information:
We added this new option "Allow known safe third-party processes behaviors" so users/companies have the option, if required, to disable the internal rules to allow known and safe third-party software behaviors (can be used to create personalized exclusion rules only for the third party software you have installed).
We also added this new option "Do not monitor non critical programs" (may be renamed in future) so users can choose to monitor any program (such as third-party file managers, etc) instead of monitoring only critical programs.
The above two options (enabled by default, at the moment) will help in reducing false positives, especially the first one.
The option "Enable internal rules to allow safe behaviors" now handles only system-related known and safe processes behaviors (highly recommended to have it enabled).
@Victor M
This new version fixed the issue you reported, mainly to make it work:
1) Create two new users in the AD server, e.g Dev-SUA and Dev-Admin
2) On the W10 PC go on Account -> Access work or school -> click on Connect
3) Click on the link "Join this device to a local Active Directory domain"
4) Enter the domain and then enter the username and password for the user that will be SUA (e.g Dev-SUA)
5) Select the account type as Standard User Account
6) Then restart the PC.
Repeat steps from 2 to 6 but for Administrator account (basically, enter username Dev-Admin and set it as Administrator)
Then on OSArmor enable the option "Password-protect power options with Windows Admin Credentials"
From the SUA account, when you are prompted to enter the credentials to unlock OSArmor window/right-click menu/etc, select the username (Administrator account) e.g DOMAIN\Dev-Admin and enter its password.
That will work fine (tested here on a Windows Server 2022 and a Windows 10 and Windows 11 VM).
It is important that you connect both SUA and Admin accounts because OSArmor option "Password-protect power options with Windows Admin Credentials" requires that you enter credentials for an Administrator account (and in this case it must be connected to the AD domain).
@Guilhermesene @Zero Knowledge
We're running some tests with multi-year subscription in these days (2 years plan), if all goes well we should add them very soon.
We're also discussing about discounts for multi-products purchased in a bundle (e.g OSArmor + SysHardener).
Will update here as soon as I can share more details.
@Guilhermesene
The behavior you described is correct for OSArmor <= 1.8.1, now with the final release of OSArmor v1.8.2 we introduced this new option:
"Do not monitor non critical programs" -> If you uncheck it, all programs (also non critical like Total Commander and any other third-party file manager) will be monitored.
At the moment it is enabled by default.

Download OSArmor for Windows 7, 8, 10, 11 (32 & 64-bit) | OSArmor
Download the setup file for OSArmor Personal, Business and Enterprise version for Windows 7, 8, 10, 11 (32 & 64-bit). All executable files are digitally signed and free from adware.
www.osarmor.com
Here is the changelog:
[13-Jan-2023] v1.8.2.0
+ Added option to manually check for updates
+ Added new internal rules to block suspicious behaviors
+ Added more signers to Trusted Vendors list
+ Improved support for high-DPI
+ Do not ask for password when Enable Protection is clicked
+ Added option Allow known safe third-party processes behaviors
+ Added option Do not monitor non critical programs
+ Improved Block execution of Group Policy Editor
+ Improved Password-protect power options with Windows Admin Credentials
+ Fixed all reported false positives
+ Updated NVT License Manager with latest version
+ Renamed Extreme Protection profile in Maximum Protection
+ Updated Help/FAQs file
+ Minor improvements
If you have automatic updates enabled then OSArmor should auto-update in the next hours.
Else you can install it "over-the-top" of the installed version, reboot is not needed.
* If you used test builds you should manually update to this final version (install over-the-top is fine).
If you find false positives or issues please let me know.
A few information:
We added this new option "Allow known safe third-party processes behaviors" so users/companies have the option, if required, to disable the internal rules to allow known and safe third-party software behaviors (can be used to create personalized exclusion rules only for the third party software you have installed).
We also added this new option "Do not monitor non critical programs" (may be renamed in future) so users can choose to monitor any program (such as third-party file managers, etc) instead of monitoring only critical programs.
The above two options (enabled by default, at the moment) will help in reducing false positives, especially the first one.
The option "Enable internal rules to allow safe behaviors" now handles only system-related known and safe processes behaviors (highly recommended to have it enabled).
@Victor M
This new version fixed the issue you reported, mainly to make it work:
1) Create two new users in the AD server, e.g Dev-SUA and Dev-Admin
2) On the W10 PC go on Account -> Access work or school -> click on Connect
3) Click on the link "Join this device to a local Active Directory domain"
4) Enter the domain and then enter the username and password for the user that will be SUA (e.g Dev-SUA)
5) Select the account type as Standard User Account
6) Then restart the PC.
Repeat steps from 2 to 6 but for Administrator account (basically, enter username Dev-Admin and set it as Administrator)
Then on OSArmor enable the option "Password-protect power options with Windows Admin Credentials"
From the SUA account, when you are prompted to enter the credentials to unlock OSArmor window/right-click menu/etc, select the username (Administrator account) e.g DOMAIN\Dev-Admin and enter its password.
That will work fine (tested here on a Windows Server 2022 and a Windows 10 and Windows 11 VM).
It is important that you connect both SUA and Admin accounts because OSArmor option "Password-protect power options with Windows Admin Credentials" requires that you enter credentials for an Administrator account (and in this case it must be connected to the AD domain).
@Guilhermesene @Zero Knowledge
We're running some tests with multi-year subscription in these days (2 years plan), if all goes well we should add them very soon.
We're also discussing about discounts for multi-products purchased in a bundle (e.g OSArmor + SysHardener).
Will update here as soon as I can share more details.
@Guilhermesene
The behavior you described is correct for OSArmor <= 1.8.1, now with the final release of OSArmor v1.8.2 we introduced this new option:
"Do not monitor non critical programs" -> If you uncheck it, all programs (also non critical like Total Commander and any other third-party file manager) will be monitored.
At the moment it is enabled by default.
Last edited:
Here is a pre-release test 2 version of OSArmor PERSONAL v1.8.3:
What's new so far:
You can install over-the-top, reboot is not needed.
Let me know if you find issues or FPs.
Code:
https://downloads.osarmor.com/osa-personal-1-8-3-test2.exeWhat's new so far:
+ Added more signers to Trusted Vendors list
+ Added popup menu option "Copy to Clipboard" on Protections List
+ Added Process Integrity and Parent Process Integrity on Exclusions Helper
+ Added new internal rules to block suspicious behaviors
+ Improved installer and uninstaller scripts
+ Fixed all reported false positives
+ Minor improvements
You can install over-the-top, reboot is not needed.
Let me know if you find issues or FPs.
@NoVirusThanks
currently osarmor has only 3 options for user to respond to alert:
allow always
block always
ignore always
need option to allow and block once
provides more flexibility for advanced, knowledgeable user to control and manage processes on their system
ps - i know advanced, knowledgeable user can write custom rules in osarmor to permit execution by parent, (for process execution monitoring by disallowed parent) but most users will not do that
currently osarmor has only 3 options for user to respond to alert:
allow always
block always
ignore always
need option to allow and block once
provides more flexibility for advanced, knowledgeable user to control and manage processes on their system
ps - i know advanced, knowledgeable user can write custom rules in osarmor to permit execution by parent, (for process execution monitoring by disallowed parent) but most users will not do that
Last edited:
@NoVirusThanks
If I may ask, what does this do?
If I may ask, what does this do?
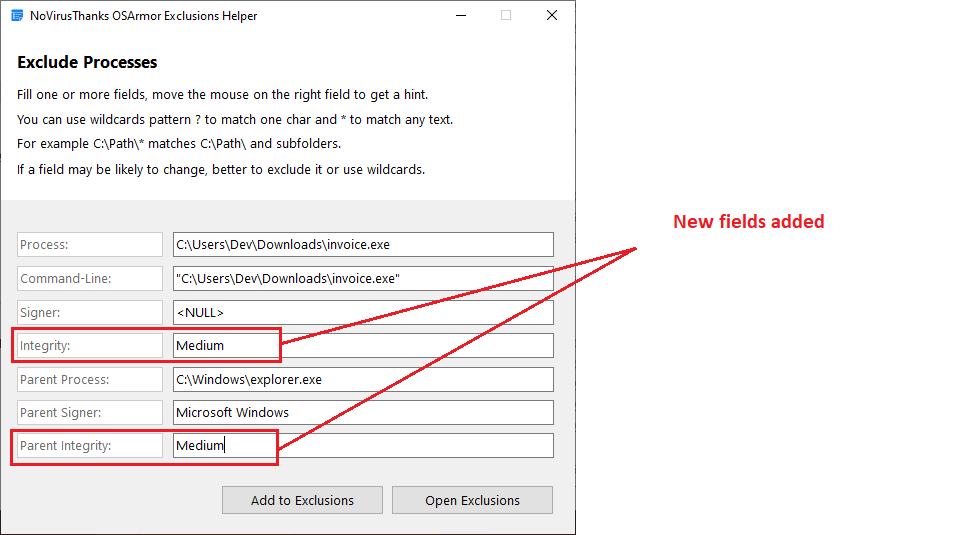
+ Added Process Integrity and Parent Process Integrity on Exclusions Helper
@wat0114
Here is a screenshot (mainly added these two fields to be matched in Exclusions Helper GUI):
@Andrezj
OSArmor by default blocks the process behavior and shows the alert to the user after it has been already blocked.
If we add an "Allow Once" option it would allow the event once but only on the next time the process behavior is detected.
We may discuss about add an option like "Exclude for N minutes" probably, like a temporary exclusion that is not written to Exclusions.db file.
The quick way to handle this scenario at the moment is to like disable protection when installing a safe and trusted application and re-enable protection once done (just an example).
Or can be enabled the option "Passive Logging" so all process blocked events are only logged and not blocked.
Here is a screenshot (mainly added these two fields to be matched in Exclusions Helper GUI):
@Andrezj
OSArmor by default blocks the process behavior and shows the alert to the user after it has been already blocked.
If we add an "Allow Once" option it would allow the event once but only on the next time the process behavior is detected.
We may discuss about add an option like "Exclude for N minutes" probably, like a temporary exclusion that is not written to Exclusions.db file.
The quick way to handle this scenario at the moment is to like disable protection when installing a safe and trusted application and re-enable protection once done (just an example).
Or can be enabled the option "Passive Logging" so all process blocked events are only logged and not blocked.
Oh wow, so it is for Mandatory Integrity Control. I just took a look, which I should have done earlier@wat0114
Here is a screenshot (mainly added these two fields to be matched in Exclusions Helper GUI):
%PROCESSINTEGRITY%,
%PROCESSINTEGRITY% & %PARENTINTEGRITY% can be the following: Untrusted, Low, Medium, Medium Plus, High, System, Protected, Unknown
EDIT
This Parent/Process Integrity option works as I thought it would. Very nice
Last edited:
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
OSArmor v1.8.3 released:

 www.wilderssecurity.com
www.wilderssecurity.com
Download OSArmor for Windows 7, 8, 10, 11 (32 & 64-bit) | OSArmor
Here is the changelog:
+ Added more signers to Trusted Vendors list
+ Added popup menu option "Copy to Clipboard" on Protections tab
+ Added Process Integrity and Parent Process Integrity on Exclusions Helper
+ Added new internal rules to block suspicious behaviors
+ Improved installer and uninstaller scripts
+ Added Block execution of Winget (Windows Package Manager)
+ Updated FAQs (Help.txt) with new questions and answers
+ Fixed all reported false positives
+ Minor improvements
If you have automatic updates enabled then OSArmor should auto-update in the next hours.
Else you can install it "over-the-top" of the installed version, reboot is not needed.
* If you used test builds you should manually update to this final version (install over-the-top is fine).
If you find false positives or issues please let me know.
NoVirusThanks OSArmor: An Additional Layer of Defense
1.8.3 is the latest version. Sorry, I meant 1.8.3. I did edit my post to reflect that. Thanks for catching that. =)
Here is a pre-release test 1 version of OSArmor PERSONAL v1.8.4:
What's new so far:
You can install over-the-top, reboot is not needed.
Let me know if you find issues or FPs.
@LDogg
We've not discussed about it yet, but it is not in the current roadmap.
Code:
https://downloads.osarmor.com/osarmor-personal-1-8-4-test1.exeWhat's new so far:
+ Added more signers to Trusted Vendors list
+ Added option Show a notification when product has been updated
+ Added new internal rules to block suspicious behaviors
+ Fixed all reported false positives
+ Minor improvements
You can install over-the-top, reboot is not needed.
Let me know if you find issues or FPs.
@LDogg
We've not discussed about it yet, but it is not in the current roadmap.
We've released OSArmor v1.8.4:

Here is the changelog:
If you have automatic updates enabled then OSArmor should auto-update in the next hours.
Else you can install it "over-the-top" of the installed version, reboot is not needed.
* If you used test builds you should manually update to this final version (install over-the-top is fine).
If you find false positives or issues please let me know.

Download OSArmor for Windows 7, 8, 10, 11 (32 & 64-bit) | OSArmor
Download the setup file for OSArmor Personal, Business and Enterprise version for Windows 7, 8, 10, 11 (32 & 64-bit). All executable files are digitally signed and free from adware.
www.osarmor.com
Here is the changelog:
[15-Feb-2023] v1.8.4.0
+ Added more signers to Trusted Vendors list
+ Added option Show a notification when product has been updated
+ Added new internal rules to block suspicious behaviors
+ Fixed all reported false positives
+ Minor improvements
If you have automatic updates enabled then OSArmor should auto-update in the next hours.
Else you can install it "over-the-top" of the installed version, reboot is not needed.
* If you used test builds you should manually update to this final version (install over-the-top is fine).
If you find false positives or issues please let me know.
Hello. I have a question about version 1.4.3.
Is it possible in version 1.4.3 to prohibit unsigned programs from direct access to the disk?
If so, how to do it (what rule should I write for this)?
Direct access to the disk is usually needed by encryption programs and programs for low-level disk formatting.
Is it possible in version 1.4.3 to prohibit unsigned programs from direct access to the disk?
If so, how to do it (what rule should I write for this)?
Direct access to the disk is usually needed by encryption programs and programs for low-level disk formatting.
I have no idea if this works but...Hello. I have a question about version 1.4.3.
Is it possible in version 1.4.3 to prohibit unsigned programs from direct access to the disk?
If so, how to do it (what rule should I write for this)?
Direct access to the disk is usually needed by encryption programs and programs for low-level disk formatting.
Here are the steps to create a rule to restrict disk access for unsigned programs in OSArmor:
- Open OSArmor and click on the "Rules" tab.
- Click on the "Add" button to create a new rule.
- In the "Add Rule" window, select "Disk Access" as the rule type.
- Under the "Process" section, select "Unsigned" from the drop-down menu.
- Under the "File/Folder" section, select the drive or folder that you want to restrict access to.
- Under the "Action" section, select "Block" or "Log" depending on how you want OSArmor to respond when an unsigned program tries to access the disk.
- Click on the "Save" button to create the new rule.
You may also like...
-
On Sale! Avast Premium Security 1 Device 1 Year 9.99€
- Started by Brownie2019
- Replies: 0
-
-
Serious Discussion Block Common Attacks: A Beginner's Guide to Windows Firewall
- Started by Divergent
- Replies: 18
-
Privacy News Windows 11 24H2/25H2 Flaw Keeps Task Manager Running After You Close It
- Started by Brownie2019
- Replies: 5