One of my clients had an edr alerts from Ooma Office. After investigation we believe it's a part of an early Supply Chain attack. The process was Dormant until after 5pm business hours when it started spawning lolbins and doing discovery actions.
Vt says 2 engines. Their main installer is signed but the omma office.exe process isn't. Certificate chain issue with the file also. Very low file prevelance and defender flags it with two detections. I'm thinking there may be some hidden shell code in it. This reminds me of the 3cx VoIP hack. ea649ee7430b61db82c8f23470f27f956baf88a245f159af96ea49159c2656e6 | Triage
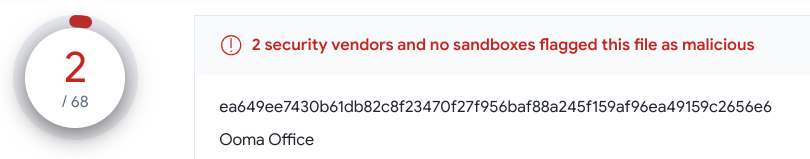
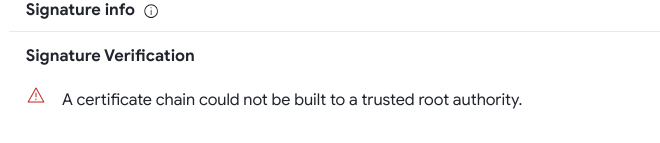
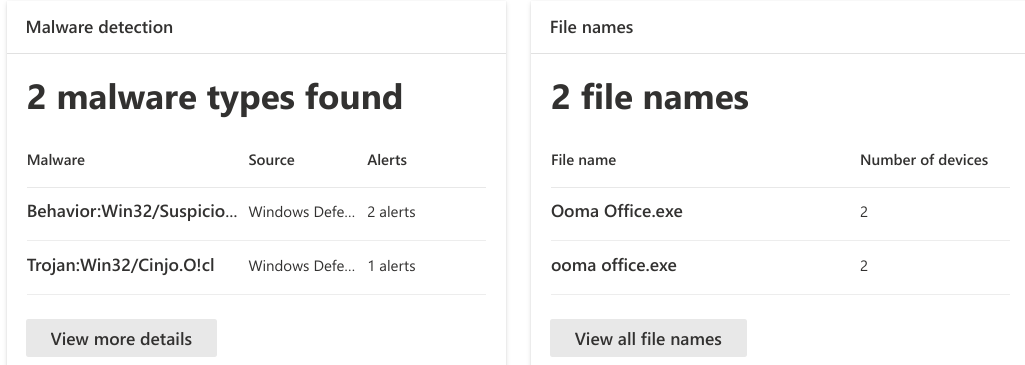
Vt says 2 engines. Their main installer is signed but the omma office.exe process isn't. Certificate chain issue with the file also. Very low file prevelance and defender flags it with two detections. I'm thinking there may be some hidden shell code in it. This reminds me of the 3cx VoIP hack. ea649ee7430b61db82c8f23470f27f956baf88a245f159af96ea49159c2656e6 | Triage