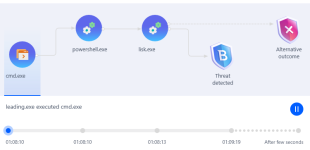
It looks similar to Electron because it is also a Node.js application. But not Electron. It is also correct that the full folder's contents are necessary to run everything. But one could create a standalone executable by creating an SFX with 7zip. If you think this helps you with automatic analysis sandboxes, I can try to create one.
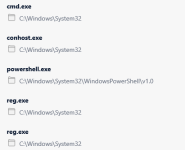
You find the entry point of the application in the package.json. This file mentions first_page.html as main.
View attachment 277024
The malicious code is inside: init/first_page.html
In first_page.html you see obfuscated JavaScript.
View attachment 277023
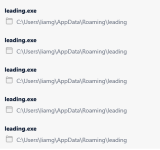
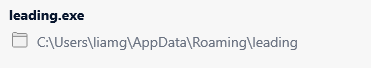
The application creates a folder in %LOCALAPPDATA%\Leading and saves a lot of data there.
You should delete this folder on your friend's system.
View attachment 277021
View attachment 277025
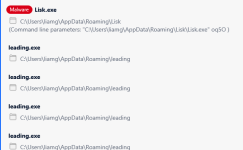
Looks like adware/spyware to me. The folder is full of affiliate and advertising related data.
Didn't have time to deobfuscate the code yet, it looks a bit nasty, and I do not think it is worth sinking hours into it because it does not seem to be a serious threat. It stems likely from a Potentially Unwanted Software download. Make sure to check the installed programs on the system for PUP.