Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
I don't quite understand.Being a lefty forced to write with my right hand at schools (yes I am that old), I tend look differently at things than most people. Not surprisingly I have figured out a light intermediate mode, which breaks less websites as medium mode (blocking third-party frames) and a dare to say is safer than the default medium mode many people use.
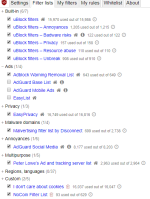
My Rules
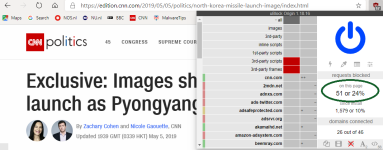
With advanced mode enables you can see what domains are blocked. In case you want to allow a HTTP website
----
no-cosmetic-filtering: * true
no-large-media: behind-the-scene false
no-scripting: behind-the-scene false
* * * noop
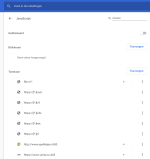
My Filter
The idea is to block third-party request of all unsecure/unencryptes HTTP websites. When you have a look at
hXXp://vxvault.net/URL_List.php or hXXps://www.malwaredomainlist.com/mdl.php you see that most of the malware comes from HTTP websites. So blocking third-party requests from unsecure websites is good practise.
----
HTTP://*^$third-party,object,script,subdocument,ping,websocket,xmlhttprequest
Filterlists
As an advocate of light blocklists, I only have enabled Disconnect Malvertising list. This is the reason why I have disabled cosmetic filtering also (so please remove " no-cosmetic-filtering: * true" when you do use cosmetic filtering).
How do you block scripts and frames now?
Do you allow 3rd party by * * * noop ?
The only rule now is the filter HTTP://*^$third-party,object,script,subdocument,ping,websocket,xmlhttprequest ?