Gandalf_The_Grey
Level 85
Thread author
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
It does when you clear all caches and update the filters.
Yeah, it was removed and might be added again later.Did you notice that the filters "AdGuard Tracking Protection" have moved from the Privacy section to Custom? Or is this not a global change? (uBlock Origin)
Yeah, it was removed and might be added again later.
- Firefox: Submission pending
- Chromium: Submission pending
- Edge: Install from Microsoft Store: Microsoft Edge Addons
- The Microsoft Store version of uBO is published by Nicole Rolls
- Opera: Submission pending
Fixes / changes
- Prevent context menu entries on non-HTTP documents
- Ignore compilation hints when applying exception cosmetic filters
- Add support for regex-based values as target domain for static extended filters
- Add support for regex-based values for domain=/from=/to= options
- Rewrite static filtering parser
- uBO doesn't reject cosmetic filters with invalid pseudo-classes/pseudo-elements
- Make the logger entry dialog modeless
- Fix missing regex flags
- Import version 1.2.0 of RegexAnalyzer
- Set charset to utf-8 for Blob-based injected scriptlets
- Disallow -abp-... filters if not using #?#
- Work related to keyboard shortcuts for page reload
- New network filter option: to=[list of domain names]
- New network filter option: method=...
Release notes
Refer to log.txt to see filters which could not be converted due to MV3 incompatibility. At the moment not all discarded filters are necessarily reported in there
- Updated filter lists
- Translation work
no-csp-reports: * true
no-large-media: behind-the-scene false
no-popups: * true
no-strict-blocking: 192.168.0.1 true
* * 3p block
* * 3p-frame block
* * 3p-script block
* com * noop
* eu * noop
* info * noop
* io * noop
* net * noop
* org * noop
* uk * noop
behind-the-scene * * noop
behind-the-scene * 1p-script noop
behind-the-scene * 3p noop
behind-the-scene * 3p-frame noop
behind-the-scene * 3p-script noop
behind-the-scene * image noop
behind-the-scene * inline-script noop
Static Filters:
! Block beacons, plugins and websockets everywhere
||*$ping,object,websocket
! Block potentially unsafe third-party content to unencrypted websites
|HTTP://*$third-party,~document,~stylesheet,~image,~media
! Block opening webpages on top level domains and countries I never visit
||*$document,~stylesheet,~image,~media,~script,~subdocument,~xmlhttprequest,domain=~com|~info|~io|~eu|~net|~org|~uk
I guess you'd call it Easy Hard mode.I run it in a variation of Hard Mode. Takes some whitelisting but works pretty well for me. The pop-up rule can get annoying but it does block bad pop-ups
Dynamic rules:
Hehe yeah but works. Kind of used to it blocking stuff. The TLD filter saved me a few times but my no-popup dynamic rule is my longestI guess you'd call it Easy Hard mode.

 malwaretips.com
malwaretips.com
Thanks and sorry for going OT. I've not tweaking my filters for quite awhile. Will have a read through and maybe a fresh approach@ErzCrz
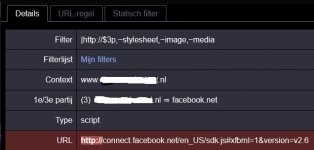
This thread isn't meant to discuss about filter rules, but I have to warn you that next rule doesn't block anything, because of the exception ~document.
! Block potentially unsafe third-party content to unencrypted websites
|HTTP://*$third-party,~document,~stylesheet,~image,~media
Edit: Here the result of a correct rule. As intended, the 3p script is blocked.
View attachment 273119
My advice would be to read next thread very well.

New Update - uBlock0rigin in Medium mode for Lighter and Stronger Protection, with Less websites breakage and hassle
Why a seperate thread? I got a few questions of the uB0 settings I posted in Old School's uB0 tips and tricks. In stead of stealing that thread I thought it might be better to create a new thread to explain these settings. I also got a question how to apply this on other browsers, so I left out...malwaretips.com
Yes, but I don't know if this setting is enabled at default. For me this setting is enough and I don't use a filterrule to block risky content on a http site. But let's not go further OT.Most browser nowadays block HTTP content on HTTPS websites, is this correct?
I learned it from JanWilly
Manifest V3 was the reason I converted uBO dynamic rules in static rules. Normally I keep using uBO in medium mode with noop rules for regular domainextensions and sometimes for a specific site to unbreak it.while JanWilly and I like to implement it with static rules
Thanks. I haven't checked the Wiki is a long time so I'll check it out.When you read the uBO wiki (and also ABP basic rules explanation) it is relatively easy to convert dynamic rules to static rules. With the new uBO FROM and TO static rules it is even easier to convert dynamic rules to static rules (* domain3p * block becomes ||*$third-party,to=domain3p and website1p domain3p * block becomes ||*$third-party,from=website1p,to=domain3p)