I mean the one that floats above your taskbar.What new icon? All I see are the same VS ones there has always been.
New Update VoodooShield CyberLock 7.0
- Thread starter danb
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
?? if CL why? Does Dan know or agree? I have never heard this before re CL and this Edge "managed by your organization" annoyance is something I take note of.No, it is CL who does that.
Does it?No, it is CL who does that.
The only affected settings were the ability to change DNS over HTTP and Startup Boost which isn't that big of a deal and probably still an Edge update thing.
The Microsoft Edge Secure Network was also greyed but that's been the case for awhile now and never found a workaround though not a feature I use in Edge.
I also keep Startup Boost disabled, and sometimes Edge goes Managed by Organization, and I have to fix it in the Registry. It gets annoying because sometimes when Edge goes MBO, some other settings turn unclickable.Startup Boost which isn't that big of a deal and probably still an Edge update thing.
Yes, when Startup Boost was introduced, there was a conflict between CyberLock and Startup Boost, and the only way to fix the issue was to disable Startup Boost. I figured it was best to disable Startup Boost anyway because there is no good reason to have a web browser running full time, whether the user is using it or not. So Startup Boost is disabled when CyberLock is installed, and it should be automatically re-enabled when CyberLock is uninstalled.

 malwaretips.com
malwaretips.com
I imagine the conflict is resolved now, so we can probably either create an option in CyberLock to enable or disable Startup Boost, or possibly see if there is a way to disable Startup Boost, but not have the option in Edge say "This setting is managed by your organization".

New Update - VoodooShield CyberLock 7.0
I asked on a different forum, but I'll ask here as well. I just looked on the Voodooshield website and could not locate the answer there. Does a VS Pro license work on only 1 PC or can you use it on multiple PC's assuming you own several PC's? Yeah, Trooper is right, it is one license per...
 malwaretips.com
malwaretips.com
I imagine the conflict is resolved now, so we can probably either create an option in CyberLock to enable or disable Startup Boost, or possibly see if there is a way to disable Startup Boost, but not have the option in Edge say "This setting is managed by your organization".
BTW, we just received an email from a long time CyberLock user who was having an issue with CyberLock blocking SuRun.exe. The reason CyberLock kept blocking SuRun.exe was because it was automatically listed as a vulnerable process in CyberLock Settings / Advanced tab.
So if you ever have a process like SuRun that is being blocked by CyberLock, if it is not a vulnerable process, you can uncheck the box in CyberLock Settings / Advanced tab so that it is not considered a vulnerable process, and will no longer be protected by CyberLock.
This probably does not happen that often (especially since this is the first time I have heard of this issue since the anti exploit feature was introduced several years ago), but I figured I would mention it just in case.
So if you ever have a process like SuRun that is being blocked by CyberLock, if it is not a vulnerable process, you can uncheck the box in CyberLock Settings / Advanced tab so that it is not considered a vulnerable process, and will no longer be protected by CyberLock.
This probably does not happen that often (especially since this is the first time I have heard of this issue since the anti exploit feature was introduced several years ago), but I figured I would mention it just in case.
Yes, when Startup Boost was introduced, there was a conflict between CyberLock and Startup Boost, and the only way to fix the issue was to disable Startup Boost. I figured it was best to disable Startup Boost anyway because there is no good reason to have a web browser running full time, whether the user is using it or not. So Startup Boost is disabled when CyberLock is installed, and it should be automatically re-enabled when CyberLock is uninstalled.
Thanks for the clarification
CL is fantastic. Just discovered you can add any of the other apps that connect to the internet as Web Apps if your running in Smart Mode though I usually have it as Always On
Well, it does look as though Win 7 has reached the End-of-Life-Cycle... At least as far as Cyberlock is concerned.
There are two softs which must always be "Allowed": %Windows\surun.exe% and %Windows\System32\sc.exe%. SuRun is the Windows version of *nix "SUDO" and sc.exe "is a Windows process that allows administrative users to establish a program as a Windows service in the Service Control Manager (SCM) database and the Registry, either locally or remotely. It is a tool to assist the Service Control Manager but is not the same" (www,file.net). For context, SuRun is a permissions manager which grants elevated rights in a local (LUA) setting; sc.exe is used almost everywhere under instruction from services.exe, especially to construct command lines. sc.exe is one of many dozen (some hundreds?) unsigned M$ files in the %Windows% folder system. SuRun.exe is (of course) signed, but its helper files (SuRun32.bin, SuRunExt.dll and SuRunExt32.dll) are not.
I do confess to disallowing Whitelist Cloud and Custom Folders because I always treated VS/CL as something that disallowed everything that wasn't in the Whitelist as potentially or actually malicious. I have reinstated the Rules, deleting the provided sample and replacing it with the simple command "Allow all files in Windows". From the early days VS3.0++ onwards I have figured that that is all anyone needs: "VoodooShield is not based on signatures or behavioral analysis ..." (Adrian Ścibor, AVLab - March 2019) under News & Updates; "If you love VoodooShield just add Zemana Free and scan once a week and you are good." NullByte - malwaretips.com. FWIW, I scan monthly alternating EEK and MBAM free scanners, and yes, I do remember to update their signature files before the scan
Despite obtaining advice and simply fiddling with settings, I cannot persuade CL to simply leave these two alone. It is possible that Microsoft has managed to provide signatures for all the System files in the Win10++ series. So the fact that CL is almost certainly behaving just like any other real-time AV is somewhat discouraging. After all, I dropped that technology like a rancid tub of old milk when VS appeared on my screen, shortly after CryptoPrevent entered its bloatware days.
I have apologised for the attachment extravaganza, but I cannot say "sorry". VS/CL no longer does what the labels on the box say.
Dan, if you could see your way back to v3/v4/v5, there are many people like me running older OSs who would return in a shot. Many of us would still be happy to pay an annual even if we don't ever upgrade again. But if not, then perhaps take Win 7 and 8 off the OS compatibility lists on "Download" and "FAQ" pages.
I wish everone here all the best.
Edit: I did try to attach a mountain of evidence, but it seems there is a limit For those who care, I can fix up a dropbox solution, which always worked on the old K-M forums.
For those who care, I can fix up a dropbox solution, which always worked on the old K-M forums.
There are two softs which must always be "Allowed": %Windows\surun.exe% and %Windows\System32\sc.exe%. SuRun is the Windows version of *nix "SUDO" and sc.exe "is a Windows process that allows administrative users to establish a program as a Windows service in the Service Control Manager (SCM) database and the Registry, either locally or remotely. It is a tool to assist the Service Control Manager but is not the same" (www,file.net). For context, SuRun is a permissions manager which grants elevated rights in a local (LUA) setting; sc.exe is used almost everywhere under instruction from services.exe, especially to construct command lines. sc.exe is one of many dozen (some hundreds?) unsigned M$ files in the %Windows% folder system. SuRun.exe is (of course) signed, but its helper files (SuRun32.bin, SuRunExt.dll and SuRunExt32.dll) are not.
I do confess to disallowing Whitelist Cloud and Custom Folders because I always treated VS/CL as something that disallowed everything that wasn't in the Whitelist as potentially or actually malicious. I have reinstated the Rules, deleting the provided sample and replacing it with the simple command "Allow all files in Windows". From the early days VS3.0++ onwards I have figured that that is all anyone needs: "VoodooShield is not based on signatures or behavioral analysis ..." (Adrian Ścibor, AVLab - March 2019) under News & Updates; "If you love VoodooShield just add Zemana Free and scan once a week and you are good." NullByte - malwaretips.com. FWIW, I scan monthly alternating EEK and MBAM free scanners, and yes, I do remember to update their signature files before the scan
Despite obtaining advice and simply fiddling with settings, I cannot persuade CL to simply leave these two alone. It is possible that Microsoft has managed to provide signatures for all the System files in the Win10++ series. So the fact that CL is almost certainly behaving just like any other real-time AV is somewhat discouraging. After all, I dropped that technology like a rancid tub of old milk when VS appeared on my screen, shortly after CryptoPrevent entered its bloatware days.
I have apologised for the attachment extravaganza, but I cannot say "sorry". VS/CL no longer does what the labels on the box say.
Dan, if you could see your way back to v3/v4/v5, there are many people like me running older OSs who would return in a shot. Many of us would still be happy to pay an annual even if we don't ever upgrade again. But if not, then perhaps take Win 7 and 8 off the OS compatibility lists on "Download" and "FAQ" pages.
I wish everone here all the best.
Edit: I did try to attach a mountain of evidence, but it seems there is a limit
If you have been using VS since 3.0 and are still running Windows 7, my best guess is that the issue would be completely resolved if you performed a clean install of CyberLock. Basically, uninstall CyberLock and tell it to delete all of the settings and logs when prompted, then restart the computer and reinstall CyberLock. Once you reinstall CyberLock, then you can uncheck the 2 items in the CyberLock Settings / Advance tab, but leave everything else in its default settings for the time being.
I am quite certain this is the root cause of your issue for several reasons. But honestly I would not know because all I know about your issue is that CyberLock was blocking SuRun.exe, so I suggested that you try to uncheck that item in the Advanced tab. It would have been extremely helpful if you could have sent me more information about the issue, and any blocks you might have experienced.
Either way, if you could either post the evidence or email it to me, I would certainly appreciate it. That way I can research the issue and fix any bugs that might exist. Thank you!
I am quite certain this is the root cause of your issue for several reasons. But honestly I would not know because all I know about your issue is that CyberLock was blocking SuRun.exe, so I suggested that you try to uncheck that item in the Advanced tab. It would have been extremely helpful if you could have sent me more information about the issue, and any blocks you might have experienced.
Either way, if you could either post the evidence or email it to me, I would certainly appreciate it. That way I can research the issue and fix any bugs that might exist. Thank you!
Quick update. I just installed SuRun on a Windows 7 machine with a limited user account, along side a clean install of CyberLock. I am triggering SuRun with a right click / SuRun: Start as Administrator, and so far it is working absolutely perfectly with CyberLock, I actually did not even have to make adjustments in the CyberLock Settings / Advanced tab (thanks to the Attack Chain feature).
So at this point, either there is a different way that you are triggering SuRun, or you simply need to perform a clean install of CyberLock. Please let me know how you are triggering SuRun and I can test further, thank you!
So at this point, either there is a different way that you are triggering SuRun, or you simply need to perform a clean install of CyberLock. Please let me know how you are triggering SuRun and I can test further, thank you!
Hokay. FIRST: CL was fully uninstalled on 2 February 2024, Western Australia time, Zulu plus 8 hours. I have found it necessary to go in with a shovel and pick axe because Windows is notoriously lax when it comes to uninstalling. After a full restart, CL was clean installed, and my standard mods performed: Disable Custom Folders, disable WLC. I deleted the preinstalled Rule and wrote a new Rule, "Allow all files in Windows folder".Either way, if you could either post the evidence or email it to me, I would certainly appreciate it. That way I can research the issue and fix any bugs that might exist. Thank you!
Let's deal with %Windows\System32\sc.exe%, which is as described in my last post, an unsigned Microsoft tool to assist the Service Control Manager. After giving the new install time to play, I took some screen grabs (click to show):
CL-User-Log < CL User Log.png >
CL-Rules < CL Rules.png >
CL-Command-Lines < CL Command Lines.png >
CL-Attack-Chains < CL Attack Chains.png >
CL-Basic-Settings < CL Basic Settings.png >
CL-DeveloperLog-last-2-days < CL DeveloperLog last 2 days.log >
(Look for the triple-asterisks)
In the Developer Log, note the entry "[02-04-2024 01:00:00] [INFO ] - RuleID: 23 | False | c:\windows\system32\sc.exe | c:\windows\system32\sc.exe start w32time task_started | c:\windows\system32\services.exe | 2". In the screenshot "CL-Attack-Chains" you can see clearly that CL seems to not care about sc.exe. But in "CL-Command-Lines" CL does care. It is fairly obvious that CL wants to see a signature on ALL files, something that won't happen in Win 7, and probably won't happen even in Win 11. Yes I can easily reverse the Command Line indicator (Block --> Allow) but that's really a bit late in the day. A bit late in the week, really. Am I going to open CL settings every couple of hours? I don't think so.
SECOND: I have SuRun 1.2.1.2, a fairly old version now, but current for Win 7 at the time. Later versions should not behave very differently from mine. You may want to paste these settings into your edition.
SuRun Settings < SuRunSettings.txt >
So at this point, either there is a different way that you are triggering SuRun
SuRun-invocation < SuRun invocation.png >
SuRun is normally invoked by clicking on "Start as Administrator" from the "Run" Start Menu Command, or from Windows Explorer context menu on an executable; however, as SuRun is primarily concerned with permissions, it also has multitudinous system hooks so it can work on the fly more or less invisibly to elevate user permissions in selected tasks exactly as *nix does, in an LUA context. Kay Bruns wrote the program to do what he considered Microsoft SHOULD have done. Anybody familiar with *nix will understand what SuRun does in Windows, and will understand that SuRun actually BECOMES PART of Windows...
So, almost all the time, I do not see or hear SuRun doing its job. Occasionally I might see a glitch when CL has blocked SuRun. Rarely, SuRun might ask me. There is an icon in the System Tray, but I leave that hidden in my LUA. Of course my Admin account has the icon displayed
Technological progress is normally on the good side. Except when it isn't. As in (for example) putting LEDs on vehicle signalling lights, which have an unpleasant habit of fading right out to invisibility when the sunlight hits at just the perfect angle, which is far more often than you might think. Sometimes incandescent globes do a better job for less cost, especially when the "waste heat" can help solve a micro-climate problem caused by unwise use of the latest low-power globes.
Last edited:
Thank you for the info, there are a total of 2 bocks in your Developer Log.
1) surunext.dll block - this is blocked because it is a Windows Control Panel applet that is not native to Windows. CyberLock is correct in blocking any non-native control panel applets. Simply allow the command line block once and you are good to go. I allowed this block on my test machine earlier today, and just to test, fired up that machine again, and it is being properly and automatically allowed.
2) w32time block – same here, this item needs to be blocked and manually allowed by the user the first time it runs. It should not be blocked after that.
All you need to do is to go into the Command Lines tab in CyberLock Settings and right click each of the two items and choose Allow one time, then they should be automatically allowed in the future. Or you can simply click allow in the user prompt when they are blocked.
On a side note, I have to reset my whitelist and command lines quite often for testing purposes. Each time I do, I have to manually allow one command line block from the backup software I use. I could hardwire that item into CyberLock, but why add it if it only affects a small handful of users?
We are both triggering SuRun the same (with a right click in Windows Explorer), so we are good to go there.
If these are the only two blocks, then CyberLock is performing exactly as expected. In fact, if CyberLock did not initially block these two items, then your computer would not be properly protected.
1) surunext.dll block - this is blocked because it is a Windows Control Panel applet that is not native to Windows. CyberLock is correct in blocking any non-native control panel applets. Simply allow the command line block once and you are good to go. I allowed this block on my test machine earlier today, and just to test, fired up that machine again, and it is being properly and automatically allowed.
2) w32time block – same here, this item needs to be blocked and manually allowed by the user the first time it runs. It should not be blocked after that.
All you need to do is to go into the Command Lines tab in CyberLock Settings and right click each of the two items and choose Allow one time, then they should be automatically allowed in the future. Or you can simply click allow in the user prompt when they are blocked.
On a side note, I have to reset my whitelist and command lines quite often for testing purposes. Each time I do, I have to manually allow one command line block from the backup software I use. I could hardwire that item into CyberLock, but why add it if it only affects a small handful of users?
We are both triggering SuRun the same (with a right click in Windows Explorer), so we are good to go there.
If these are the only two blocks, then CyberLock is performing exactly as expected. In fact, if CyberLock did not initially block these two items, then your computer would not be properly protected.
Last edited:
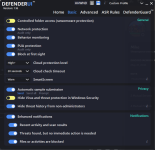
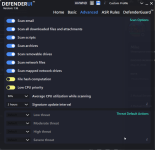
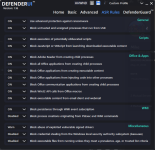
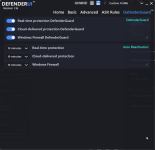
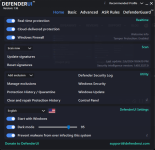
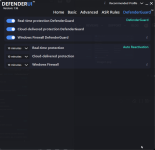
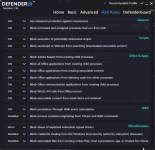
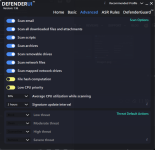
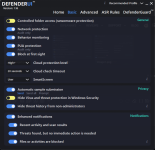
Not something I've experienced at my end. Are you turning on other switches not enabled by default in Recommended Settings?@danb DefenderUI has a bug where after a while reverts from Recommended Profile to Custom profile.
Yeah, pretty much what @ErzCrz said... we just need to figure out what setting is changing, then it will probably make sense why it is happening. There might even be a small bug we need to fix, who knows.@danb DefenderUI has a bug where after a while reverts from Recommended Profile to Custom profile.
If you could set DefenderUI to Recommended, then take screenshots of all 5 tabs. Then once you notice it switching to Custom, simply compare the settings to the screenshots, then we will know which setting changed, and hopefully it will all make sense, or at least give us a clue on what to investigate next.
See, when you set DefenderUI to Recommended, it goes through each setting and sets each one to the recommended setting. If you close DefenderUI, then make a change to Microsoft Defender settings outside of DefenderUI, when you launch DefenderUI again, it will be set to Custom, since the settings do not perfectly match any of the built in profiles. I hope that makes sense, if not please let me know, thank you!
A
Azazel
A
Azazel
Very cool, thank you for finding that! Now we just need to figure out what is causing SmartScreen to revert to Warn. It could be a bug in DefenderUI, but I am thinking it is probably something else. I will keep an eye on it, and if anyone has any insights on this, please let us know.
You may also like...
-
-
App Review Old Norton vs New Norton - Engine Comparatif
- Started by Shadowra
- Replies: 51
-
-
SOpera One R3 arrives with new AI, Google integrations, and more
- Started by Santiago Benavides García
- Replies: 0