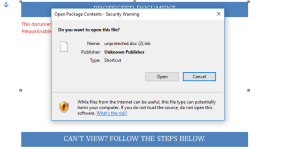
When we talk about that .rtf document, on "
enabling content" therein, it would ask to launch an
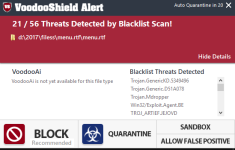
".lnk" file. These link files point to some executable and the executable loaded by the file during the exploit should then be blocked by VDS (since the type is covered by VDS).
View attachment 158381
The recent GoldenEye/NotPetya's payload was that
".dll" file delivered via the infamous ways. These dll files require to be executed by some process right?
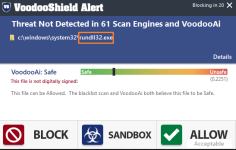
The NotPetya dll was executed via
rundll32.exe by passing necessary parameters (the
perfc.dat flag file that some quick fix guides are talking about).
View attachment 158382
When I tried executing rundll32.exe on my system, VS blocks and alerts about it. And I think it will also state about the parameters passed in case of NotPetya. That alert looks suspicious? Block it.