- Oct 13, 2019
- 779
I got an email from Emsisoft Cloud that one of my web servers had a detection:
Looks like the IIS worker process triggered a TrojanDownloader behavior block, but then Emsisoft actually automatically wrote a rule to ignore it. I'm 95% sure this is a false positive, though I am concerned that if any of my .NET websites actually got compromised, it would show up as the w3wp process doing something.
Is it normal to have w3wp trigger the behavior blocker?
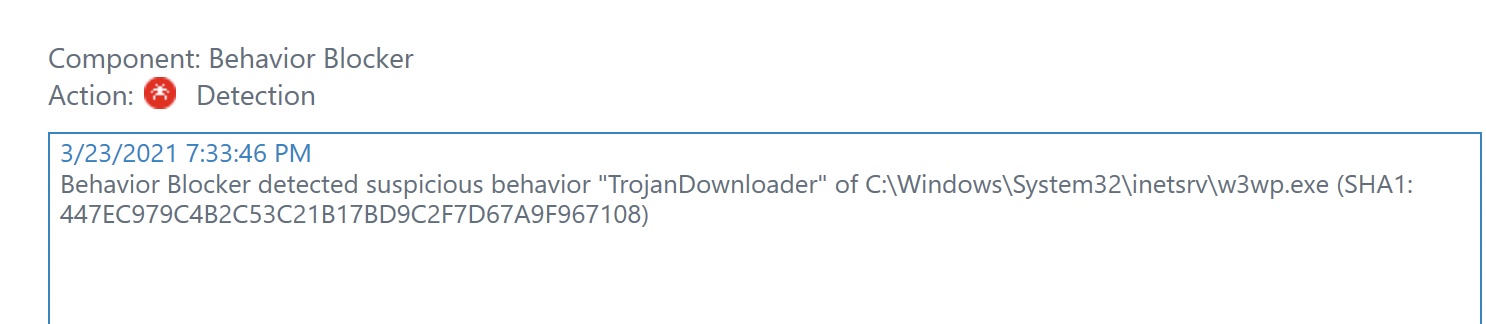
THREAT
Detected object: C:\Windows\System32\inetsrv\w3wp.exe
Category: Downloader
Detected by: Behavior Blocker
REMEDIATION
Action: Excluded, Unknown, Blocked by community
Looks like the IIS worker process triggered a TrojanDownloader behavior block, but then Emsisoft actually automatically wrote a rule to ignore it. I'm 95% sure this is a false positive, though I am concerned that if any of my .NET websites actually got compromised, it would show up as the w3wp process doing something.
Is it normal to have w3wp trigger the behavior blocker?
