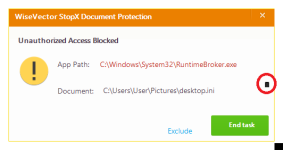
Thanks for the test. I didn't notice that the malicious samples were causing serious damage to the system. For example, I didn't see files being encrypted. Most of the infected items were IEFO hijack registry keys. In addition, i saw a malicious file was found in the startup directory, normally WVSX's behavior blocker will not allow malware to create startup items or malicious IEFO keys. This may be related to the execution of multiple harmful files at the same time. It is worth mentioning that that many old samples do not exhibit malicious behavior because their CC servers were dead.
This massive old samples test is actually a test of the ability to collect malicious samples. I know these are old samples because WVSX will upload files that trigger behavior detection. These samples are about 6 months to 3 years old. The more malware you can collect, the better you can get a good score. I have observed that for some Emotet samples, Kaspersky may not be able to detect it at the first time. But at most no more than 5 hours, it will be detected by its cloud with name :"UDS angerousObject.Multi.Generic". Large companies are well-funded and have more channels to collect malicious samples, so static scans often score 100% in thees tests (vb100, AVC, youtube tests, etc.). The samples that can be collected by these testing are only a subset of samples be collected by these large manufacturers. For security software that uses machine learning, such as WVSX, the biggest advantage is to protect users from zero-day threats, such as malware that have just appeared for a few minutes. But unfortunately, there are too few tests to test zero-day malware, I have only seen MalwareHub which is kind of a test to test zero-day malware. Most of the malware tests are testing a lot of old samples which are very beneficial for the big players.
angerousObject.Multi.Generic". Large companies are well-funded and have more channels to collect malicious samples, so static scans often score 100% in thees tests (vb100, AVC, youtube tests, etc.). The samples that can be collected by these testing are only a subset of samples be collected by these large manufacturers. For security software that uses machine learning, such as WVSX, the biggest advantage is to protect users from zero-day threats, such as malware that have just appeared for a few minutes. But unfortunately, there are too few tests to test zero-day malware, I have only seen MalwareHub which is kind of a test to test zero-day malware. Most of the malware tests are testing a lot of old samples which are very beneficial for the big players.
In fact. Defending against zero-day threats is far more difficult than detecting old threats. It is not difficult to get very good results on such tests, it might not even take a week to make one, you just need a private VT key and do a cloud hash matching for samples being scanned or launched. Samples in these tests are 100% present on VT. If only we knew that these tests had such a strong impact on users, maybe we don't need to spend years developing memory scanning, behavioral defense, instruction tracer, ransomware rollback, etc. We just need a hash checker...
We have decided to change our work plan and add cloud protection asap to achieve better results in such tests.
This massive old samples test is actually a test of the ability to collect malicious samples. I know these are old samples because WVSX will upload files that trigger behavior detection. These samples are about 6 months to 3 years old. The more malware you can collect, the better you can get a good score. I have observed that for some Emotet samples, Kaspersky may not be able to detect it at the first time. But at most no more than 5 hours, it will be detected by its cloud with name :"UDS
In fact. Defending against zero-day threats is far more difficult than detecting old threats. It is not difficult to get very good results on such tests, it might not even take a week to make one, you just need a private VT key and do a cloud hash matching for samples being scanned or launched. Samples in these tests are 100% present on VT. If only we knew that these tests had such a strong impact on users, maybe we don't need to spend years developing memory scanning, behavioral defense, instruction tracer, ransomware rollback, etc. We just need a hash checker...
We have decided to change our work plan and add cloud protection asap to achieve better results in such tests.