- Mar 2, 2023
- 1,398
This thread has been so good and informative, I can't wait for the next AV-Comparatives report to be posted 

This test shows how an antivirus behaves with certain threats, in a specific environment and under certain conditions.
We encourage you to compare these results with others and take informed decisions on what security products to use.
Before buying an antivirus you should consider factors such as price, ease of use, compatibility, and support. Installing a free trial version allows an antivirus to be tested in everyday use before purchase.
Seeing that no one knows what samples they use or how they actually perform the tests they are as credible as any other testing site. It's the same as going to auto sites to review a vehicle, you'll get numerous opinions and it's up to you to filter them. I find it somewhat incredulous that anyone bashes these type of sites as 90% of the people doing so have no idea how they test and what it means. They are just one, of many , resources for people to form an educated opinion.Always amazed that AV-Comparatives is still viewed as credible by anyone.
I think it's an okay antivirus.Do you really think that WD is a good antivirus?
Maybe, maybe not. But I wouldn't trust a third-party AV to protect my system either.In a real attack on your device, I highly doubt WD would be able to help you.
Maybe we should all get AV-Comparatives tattoos in anticipation!This thread has been so good and informative, I can't wait for the next AV-Comparatives report to be posted

Why is that an issue for you? The only thing that matters to me with in terms of performance, is if an antivirus is making my computer run noticeably slower. I don't care how much RAM is used, or how many processes it creates, if my computer isn't running slower. If an antivirus was using gigabytes of RAM, but it wasn't affecting performance, I wouldn't care. I don't have any idea how much RAM my antivirus is using, as it's not something I care about. RAM usage only matters to me, when my PC's RAM usage is very high.Regardless of the MB it consumes, the number of processes in RAM is too much. They already have almost the same processes as Mcafee.
I do think AV vendors mislead consumers, in that they make exaggerated claims about their ability to protect users from threats. Ultimately it's up to consumers to decide whether the cost is worth the increased/perception of increased protection (regardless of whether their decision is their own or influenced by a vendor's marketing).
It can but I very rarely hear about AVs getting exploited outside of vulnerability research and corporate environments. Plus Defender has be successfully exploited previously too.
I will test your Microsoft Defender Hardening very soonYour software interests me...

Since the integration of AI Machine Learning, WD has become an excellent antivirus that even manages to outperform many market leaders. By default, it's excellent, and in High or Hard mode, it's like a fortress!
I've already managed to bypass WD by injecting arbitrary code, it works once, but not afterwards...
The technique I was using involved forcibly adding an executable to WD's Exceptions. Microsoft has added Behavior detection to counter this, and it no longer works.
Defender was exploited previously? is there any proof for that

You did it with Administrator privileges? Because if you did then that's perfectly normal and it's not a vulnerability/bypass, as I explained in this document.

Microsoft patches Defender antivirus zero-day exploited in the wild
Microsoft has addressed a zero-day vulnerability in the Microsoft Defender antivirus, exploited in the wild by threat actors before the patch was released.www.bleepingcomputer.com
These methods will create multiple layers of security; also known as defense in depth. Additionally, you can create Kernel-level Zero-Trust strategy for your system.
If there will ever be a zero-day vulnerability in one or even some of the security layers at the same time, there will still be enough layers left to protect your device. It's impossible to penetrate all of them.
Also, zero-day vulnerabilities are patched quickly, so keeping your device and OS up to date, regardless of what OS you use, is one of the most basic security recommendations and best practices you must follow.
Is there a PoC for that?
I'm interested in knowing full details about this
What do you mean? My comparison or my bypass test?
If it's bypass, you've said it all ^^
In fact, he was not late at all, but they put him back to the back of the class, as the people who believed their results did not like him to remain in the first classFirst time I see Avast/AVG acing it and first time I see Kaspersky which used to always lead the pack fall back so much.
just this..View attachment 278614
Its only using like 450mb of ram after a few days, i think first couple of days it was getting used to the system.
this M.T not subreddit................plssssssThey are missing crowd intelligence from the western world, less users is less telemetry and big data.
All people who don't believe them have their reasons, av-comparatives were always manipulating their results, so stop forcefully asking them to believe them@all members bashing AV-comparatives
They have to many quality seals (they have the most out of all professional lab testing organizations) I know for that you don't (just to name one quality certificate of AVC) an ISO certification when you are not transparent and have predictable, repeatable processes in place. AV-comparatives not publishing their processes to the public does not mean that their approach is not checked and certified. Also many Universities have ties with AV-comparatives. In the academic world there are also requirements and regulations how research is performed.
The fact that their results may differ from youtube testers, does not dis-qualify their testing method.
who is he?In fact, he was not late at all, but they put him back to the back of the class, as the people who believed their results did not like him to remain in the first class
I insist, do you really think that WD is a good AV? In a real ransomware attack, it has been proven that WD is no good at protecting. Regardless of whether it is configured, and whether it has AI, all AVs have it. Not all tests are simulations.For Windows, the only winner I see is Microsoft Defender Antivirus.
How many here look at AV-C, online reviews or video tests and think "I should use this AV because of it's performance in this specific test".
All these "tests" are simulations.
I remember 10 years ago, ZeroAccess altered the permissions of Windows Defender and MSE folders (before the Windows Defender in Windows 10 era) and used a trick by placing junctions that completely disabled it. But this was valid for other security software as well. It was a very stubborn and creative malware.Defender was exploited previously? is there any proof for that
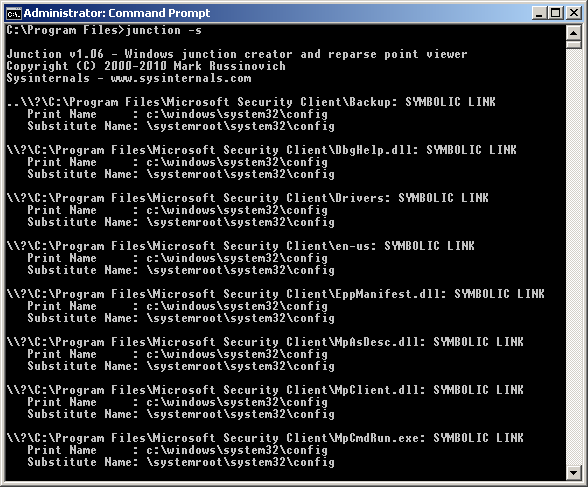
ATTENTION: ====> ZeroAccess. Use DeleteJunctionsIndirectory: C:\Program Files\Windows Defender
Another common trick was to use the IFEO keys in the registry:* ALERT: ZEROACCESS Reparse Point/Junction found!
* C:\Program Files\Windows Defender\MpCommu.dll => <Unknown Target> [File]
* C:\Program Files\Windows Defender\MpTpmAtt.dll => <Unknown Target> [File]
* C:\Program Files\Windows Defender\MsMpCom.dll => <Unknown Target> [File]
* C:\Program Files\Windows Defender\MsMpRes.dll => <Unknown Target> [File]
* C:\Program Files\Windows Defender\NisIpsPlugin.dll => <Unknown Target> [File]
* C:\Program Files\Windows Defender\NisLog.dll => <Unknown Target> [File]
* C:\Program Files\Windows Defender\NisWfp.dll => <Unknown Target> [File]
* C:\Program Files\Windows Defender\ProtectionManagement.dll => <Unknown Target> [File]
* C:\Program Files (x86)\Windows Defender\MpAsDesc.dll => <Unknown Target> [File]
* C:\Program Files (x86)\Windows Defender\shellext.dll => <Unknown Target> [File]
