If your router is using DNS over TLS, does it still make sense to use DNS over HTTPS in the browser?
Advice Request CleanBrowsing DNS vs NextDNS vs ControlD DNS
- Thread starter SohanRay
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Please provide comments and solutions that are helpful to the author of this topic.
No, you are just bypassing the router at that point. The only reason you’d want to do that is if you wanted that browser to use a different DNS than the router.If your router is using DNS over TLS, does it still make sense to use DNS over HTTPS in the browser?
UBlock on my PC's FireFox and also on my Android's is blocking Youtube ads.No dns blocking can ever block YouTube ads. That's not possible. You'll require specific https filtering extension or app for that.
But obviously you can not block the ads inside the YT app. For that I would recommend "NewPipe" which is amazing.... but since it does not have any trackers therefore, the suggestions will not be as it is in the official YT app.
Privacy is always give and take.
If some network is blocking the use of encrypted DNS, what are your choices? Anything on the software level, like an adblocker, what can prevent them for seeing the websites you visit?
- May 26, 2014
- 1,378
- 9,319
- 2,288
If some network is blocking the use of encrypted DNS, what are your choices? Anything on the software level, like an adblocker, what can prevent them for seeing the websites you visit?
I dont think that is possible to block encrypted DNS on a network level without blocking "everything" (ex: DNS over HTTPS); nothing besides a VPN or a Tor browser (not recommended) can prevent that kind of snoop.
With DNS over HTTPS (DoH), DNS queries and responses are encrypted and sent via the HTTP or HTTP/2 protocols. DoH ensures that attackers cannot forge or alter DNS traffic. DoH uses port 443, which is the standard HTTPS traffic port, to wrap the DNS query in an HTTPS request. DNS queries and responses are camouflaged within other HTTPS traffic, since it all comes and goes from the same port.
I use a network that it shows in the Wifi settings "This network doesn't allow the use of cryptographed DNS", when I use NextDNS, I get no internet.I dont think that is possible to block encrypted DNS on a network level without blocking "everything" (ex: DNS over HTTPS); nothing besides a VPN or a Tor browser (not recommended) can prevent that kind of snoop.
- May 26, 2014
- 1,378
- 9,319
- 2,288
I use a network that it shows in the Wifi settings "This network doesn't allow the use of cryptographed DNS", when I use NextDNS, I get no internet.
Did you tried DNS Over HTTPS (DoH) ?
The other methods can be blocked, DoH cant.
Try to use NextDNS directly in your browser or via YogaDNS client with the appropriate configuration.
All you need is the destination IP address to block DoH. The packet has to be going somewhere even if you can’t read it.I dont think that is possible to block encrypted DNS on a network level without blocking "everything" (ex: DNS over HTTPS); nothing besides a VPN or a Tor browser (not recommended) can prevent that kind of snoop.
It's an iPhone. How to change NextDNS to DoH? I don't know which encryption it uses by default.Did you tried DNS Over HTTPS (DoH) ?
The other methods can be blocked, DoH cant.
Try to use NextDNS directly in your browser or via YogaDNS client with the appropriate configuration.
It uses DoHIt's an iPhone. How to change NextDNS to DoH? I don't know which encryption it uses by default.
- May 26, 2014
- 1,378
- 9,319
- 2,288
All you need is the destination IP address to block DoH. The packet has to be going somewhere even if you can’t read it.
This is more theoretical than pratical, DoH is camouflaged within other HTTPS traffic.
- May 26, 2014
- 1,378
- 9,319
- 2,288
No you just use an ip table list of DoH providers and block packets heading to those IPs through port 443. It’s cumbersome, but organizations are definitely capable if they want to deal with the hassle.This is more theoretical than pratical, DoH is camouflaged within other HTTPS traffic.
The default is DoT no?
- May 26, 2014
- 1,378
- 9,319
- 2,288
No you just use an ip table list of DoH providers and block packets heading to those IPs through port 443. It’s cumbersome, but organizations are definitely capable if they want to deal with the hassle.
By this method?
How to block DNS over HTTPS using IPtables
I've recently started using iptables for the first time on my OpenWrt, Linux based router. Out of the box the OpenWrt firewall is very good, however, after wanting to do more advanced things with the
Dont seen that effective.
- May 26, 2014
- 1,378
- 9,319
- 2,288
iOS devices only support DoH natively. And as he is using an Apple Configuration Profile, it has to be DoH.
Are you sure? I am not an iOS user, but I read about Dot support.
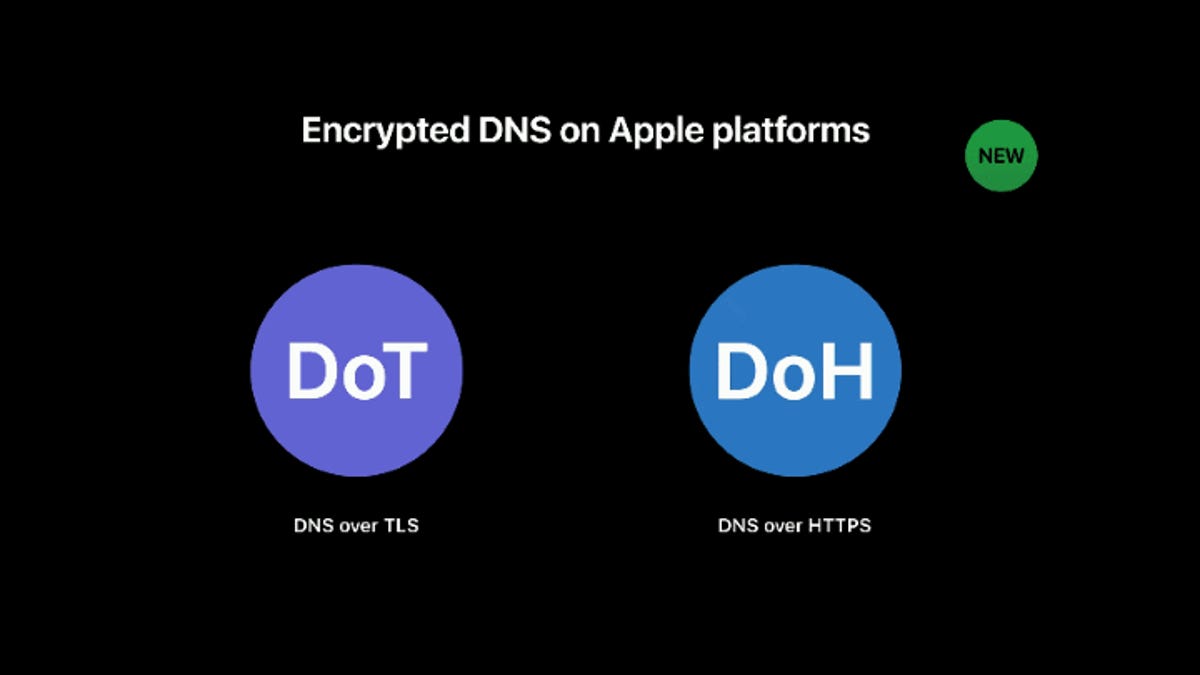
Apple adds support for encrypted DNS (DoH and DoT)
Apple said this week that iOS 14 and macOS 11 will support the DNS-over-HTTPS and DNS-over-TLS protocols.
 www.zdnet.com
www.zdnet.com
It's effective to block, ineffective to redirect because it breaks the encryption. You would just have no ability to resolve anything and have to maintain the IP tables.By this method?
How to block DNS over HTTPS using IPtables
I've recently started using iptables for the first time on my OpenWrt, Linux based router. Out of the box the OpenWrt firewall is very good, however, after wanting to do more advanced things with theserverfault.com
Dont seen that effective.
Okay, before I spread any false information I will just share this here:Are you sure? I am not an iOS user, but I read about Dot support.

Apple adds support for encrypted DNS (DoH and DoT)
Apple said this week that iOS 14 and macOS 11 will support the DNS-over-HTTPS and DNS-over-TLS protocols.www.zdnet.com
test.nextdns.io
Here he can check wether he is using DoH or DoT
Anyway, sorry to derail the conversation. The point is it can be blocked, easily by corps with the resources to do it. But it would be noticeable and very difficult to redirect. One would know they are being blocked.
You may also like...
-
Battle How Adguard compares to NextDns and ControlD regarding blocking malicious domains?
- Started by Parkinsond
- Replies: 9
-
Poll Paid vs Free Antivirus in 2026: What are you using, and is it worth paying for?
- Started by Bot
- Replies: 96
-
Battle Chrome vs. Firefox vs. Edge in 2026 — Which Browser Should Home Users Trust?
- Started by Bot
- Replies: 275
-