Yes EAM. detecto.6 of 9 malwares.Comodo Sandbox if detected. the malware was less than 10 days.
Comodo doing Bad things to Bad Rabbit!
- Thread starter Fel Grossi
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
- Status
- Not open for further replies.
Can you try disable the sandbox in Comodo and use its HIPS+BB to detect again? ThanksYes EAM. detecto.6 of 9 malwares.Comodo Sandbox if detected. the malware was less than 10 days.
D
Deleted member 178
1- be sure they are real malware, because a "malware" that sit and does nothing isn't a malware.
2- be sure to run dynamic tests.
3- gives the VT links.
2- be sure to run dynamic tests.
3- gives the VT links.
Malware are my only mistake was that I deleted it without wanting to do it. I always keep malware for a couple of days. But it has been so.1- be sure they are real malware, because a "malware" that sit and does nothing isn't a malware.
2- be sure to run dynamic tests.
3- gives the VT links.
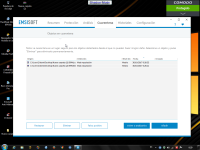
Well: I've been looking for where I downloaded the malware. and I do not know if they are the same, but this time there have been two that the behavior detector has failed, but the Comodo Sandbox firewall does not. : Here are the links of the two malwares:
Antivirus scan for ddf4a2ef4597033f7b9cd8f487e7a9ddbf7fffc16dc5e50e676af046c7f2ba41 at 2017-10-29 14:31:56 UTC - VirusTotal
Antivirus scan for abbd035fffd42facc51a33d3dcf015d858a0d5eb570cb4ae9907a8303352497a at 2017-10-29 13:44:30 UTC - VirusTotal
Antivirus scan for ddf4a2ef4597033f7b9cd8f487e7a9ddbf7fffc16dc5e50e676af046c7f2ba41 at 2017-10-29 14:31:56 UTC - VirusTotal
Antivirus scan for abbd035fffd42facc51a33d3dcf015d858a0d5eb570cb4ae9907a8303352497a at 2017-10-29 13:44:30 UTC - VirusTotal
Attachments
The behavioral detection module works inside the sandbox .. You can get out it. it is called viruscope..I do not remember if it was in advanced configuration or in the container.
The behavior modules are not perfect.
Bribon I was watching your images. BBs do not work when scanning. They work with samples LIVE .. You have to execute them for the modules to work ...
So you must put yourself at risk for them to run. If they do not work, you become infected.
The behavior modules are not perfect.
Bribon I was watching your images. BBs do not work when scanning. They work with samples LIVE .. You have to execute them for the modules to work ...
So you must put yourself at risk for them to run. If they do not work, you become infected.
Last edited:
Friend Klaklen: It's what I did. I clicked on it. and nothing happened and Comodo if I actThe behavioral detection module works inside the sandbox .. You can get out it. it is called viruscope..I do not remember if it was in advanced configuration or in the container.
The behavior modules are not perfect.
Bribon I was watching your images. BBs do not work when scanning. They work with samples LIVE .. You have to execute them for the modules to work ...
So you must put yourself at risk for them to run. If they do not work, you become infected.
Bribon ... shhh. They will think that we are working together. XD
Ok is that it seemed analysis ..
BB failure emisoft XD ..
And if you deactivate the sandbox .. Which part of comfortable act ??? .. Hip or just the firewall.
Ok is that it seemed analysis ..
BB failure emisoft XD ..
And if you deactivate the sandbox .. Which part of comfortable act ??? .. Hip or just the firewall.
I forgot according to my experience .. Comodo acts before the antivirus .. Therefore if you run a file usually comodo blocks it before ..
To make cash you have to disable Comodo XP ..
that's why it's ideal to make your own suiT XD.
To make cash you have to disable Comodo XP ..
that's why it's ideal to make your own suiT XD.
I forgot according to my experience .. Comodo acts before the antivirus .. Therefore if you run a file usually comodo blocks it before ..
To make cash you have to disable Comodo XP ..
that's why it's ideal to make your own suiT XD.
That if possible.
D
Deleted member 178
Please guys when you do malware testing, use only one solution at the time...I've disabled Sandbox VirusEscope, website filters. And in this case it has worked! It looks like the Comodo Firewall sandbox advances before the EAM detector.
View attachment 171206
D
Deleted member 178
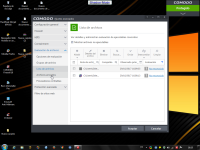
You have to know that when you use various software, Windows gives a number to each software's drivers, which is like a "queue" number called Altitude; so if one software's drivers has a lower number, it will react first.
Allocated Altitudes
(note that the driver of emsisoft mentioned there is old, we use another one since, which isn't listed, the list seems obsolete)
Allocated Altitudes
(note that the driver of emsisoft mentioned there is old, we use another one since, which isn't listed, the list seems obsolete)
Last edited by a moderator:
D
Deleted member 178
So unless your name is Umbra and you are a combo masterchef, don't use combos without researching first 
And i believe i was among the first to combine EAM + Comodo FW / IS years ago
And i believe i was among the first to combine EAM + Comodo FW / IS years ago
Last edited by a moderator:
Yes and I visited your blog. what a scare I have taken.So unless your name is Umbra and you are a combo masterchef, don't use combos without researching first
And i believe i was among the first to combine EAM + Comodo FW / IS years ago
D
Deleted member 178
lol you find my old blog, i thought they would delete it since i didn't used it since a whileYes and I visited your blog. what a scare I have taken.
Comodo takes protection by denial.
The antivirus or BB, both use signatures although in different ways .. BB seeks behavior by generally assigning malware.
Comodo was based on old school protection. With alerts of actions of the applications.
A home user usually only uses the browser (facebook, mail) and office, do not install, do not test things ... with a lock configuration and 0 notifications = 100% SECURE AND WILL NOT DARE the comodo.
Also comodo is 100% free without advertising .... XD
The antivirus or BB, both use signatures although in different ways .. BB seeks behavior by generally assigning malware.
Comodo was based on old school protection. With alerts of actions of the applications.
A home user usually only uses the browser (facebook, mail) and office, do not install, do not test things ... with a lock configuration and 0 notifications = 100% SECURE AND WILL NOT DARE the comodo.
Also comodo is 100% free without advertising .... XD
I'm not saying having a sb is no good. I'm questioning the use practicality aspect of it. IMO a HIPS(heuristics-based) + BB(behavioral-based) is a better and more practical approach than using a sb noting that each technology (sb, HIPS, BB) has its limitations
For me the primary limitation if there is one is the user requirement to see the alert and choose to run restricted. However and as mentioned, Comodo will sandbox unrecognized/unsigned or improperly signed without an alert with an alteration of the settings from those used in the video (I think the Comodo default may actually be to not see the privilege escalation alert...can't recall). @cruelsister simply uses this run restricted option with no alert.
I run some unsigned software, so I use the alerts to allow them, knowing the risk. At any rate, for me, this is where I would like to see Comodo become the name to trust for recognition of sketchy signatures. I mean, the company issues digital signatures themselves, so being known this way would be of value to the company. I want to trust Cloud Lookup but so far I choose to trust the av (avast or Qihoo) to provide more information on the unsigned programs I am without question going to run. It's working so I am happy with the arrangement. Mostly this is because I only run software that I know I can trust. Maybe more CCleaner episodes are out there but I haven't been hit yet.
Comodo's BB is weak. Can it compare to BB from EAM, BitDefender, Norton etc?
For me, BB response is like a specialized HIPS response. It can be more sophisticated than HIPS, of course, but this is how I think of BB. Well, in Comodo, what about its heuristic command line monitoring...is this not BB? When I examine the authority in methodologies of protection, heuristic command line monitoring is the one that comes to my mind as the single absolutely indispensable element of security that must be on every system. Comodo does have this going for it, even if Viruscope is still non-functional/non-existent.
Overall, I guess if I would point to an area where Comodo can improve, I would say it might be in settings packages that are easy to understand. Difficult challenge maybe, but I do feel this would add to the program. One other thing would be to make the alerts match the risk a little bit better.
- Status
- Not open for further replies.
You may also like...
-
-
Advice Request Help: Comodo 2025 - cmdguard.sys - boot fail with newer Nvidia drivers
- Started by Something-x2
- Replies: 33
-
Serious Discussion Why does the Comodo "Disappearing HIPS rules" bug require a complete source code rewrite?
- Started by bazang
- Replies: 421
-
By Staff What is really going on in the Comodo threads?
- Started by Jack
- Replies: 201
-