The old CIS use to prompt you to restart your machine after making such changes but not the case these days. Just with other applications, you need to restart for those changes to actually be set.BETA Caution
When you change the Auto Containment rules, not only do you need to click Apply, you also need to Exit CIS. Or else the rule changes will not stick. And thus your Configuration File Save will not have the settings you changed.
App Review COMODO Internet Security 2024 BETA
- Thread starter Shadowra
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
It is advised to take all reviews with a grain of salt. In extreme cases some reviews use dramatization for entertainment purposes.
- Content created by
- Shadowra
But Xcitium Comodo Internet Security current version does not require that.Just with other applications, you need to restart for those changes to actually be se
Perhaps but that's endpoint rather than consumer and CIS/CF although similar looking, I presume CIS/CF's policies are locally set compared to being remotely managed. Anyway, with CIS/CF you need to restart the pc, much like you do when you change the CF/CIS configuration say to Proactive.But Xcitium Comodo Internet Security current version does not require that.
Attached is my CIS 2024 Beta config file, you can Import it at Settings / Configuration / Import Button. Don't forget to Activate it.
Particulars about this config:
. No Auto Containment Rule changes; all the default rules were kept; no additions.
. HIPS Rules were added:
... RuntimeBroker set to Custom Ruleset: Limited Application
... LogonUI set to Custom Ruleset: Limited Application. ( the reason: my red team guest attacked this, and made configration changes such that Logins are impossible. Restricting it to Limited Application protects LogonUI.
... TaskHostw. set to Custom Ruleset: Limited Application. My Xcitium CIS OpenEDR reported attacks against this. So setting it to Limited Application for protection.
. HIPS Settings
... Do not show popup alerts: Block Request ( no adverse effects noticed, so I am playing it safe )
... Block all unknown requests ... ( no adverse effects noticed, so I am playing it safe )
. HIPS Protected Objects
... Blocked Files
...... Powershell and Powershell_ise (these 2 are not frequently used by me. And attackers usually want to execute these 2 to perform fileless attacks.
...... cmd, blocked for the same reason as Powershell
...... mmc is the base application for Group Policy Editor, Local Security Policy, Device Manager and some others. If an attacker can reach this, they can disable a lot of defenses.
...... MoUsoCoreWorker is part of Windows Update. I don't run Windows Update, because last year 2023 I was attacked via Windows Update because a MS Certificate Leak allow hackers to sign malware posing as win updates. The leaked cert should be revoked by now, but I have gotten used to going to MS Update Catalog site to manually download and verify updates.
...... Drvinst is blocked for the same reason as Win Updates, drvinst installs drivers
...... wuauclt is part of Win Update
...... BitLocker, BitLockerToGo I do not encrypt the hard drive nor USB sticks. My 12 yr old Core i5 is already slow as is, and nobody is going steal a 5 lb laptop.
....... SSH is blocked because it is a known hacker TTP to setup a backdoor using this, source OSINT.
...... WerFault is blocked because I don't send error reports to MS
. Firewall
... Application Rules. Only contains a select few Windows exe's that are necessary for MS Account sign in , Outlook and smartscreen etc.
So because of the HIPS blocks, you will need to turn off HIPS protection if you want to use any of the above blocked exe's.
To download the config file, just click on the Play button inside the Spoiler.
Particulars about this config:
. No Auto Containment Rule changes; all the default rules were kept; no additions.
. HIPS Rules were added:
... RuntimeBroker set to Custom Ruleset: Limited Application
... LogonUI set to Custom Ruleset: Limited Application. ( the reason: my red team guest attacked this, and made configration changes such that Logins are impossible. Restricting it to Limited Application protects LogonUI.
... TaskHostw. set to Custom Ruleset: Limited Application. My Xcitium CIS OpenEDR reported attacks against this. So setting it to Limited Application for protection.
. HIPS Settings
... Do not show popup alerts: Block Request ( no adverse effects noticed, so I am playing it safe )
... Block all unknown requests ... ( no adverse effects noticed, so I am playing it safe )
. HIPS Protected Objects
... Blocked Files
...... Powershell and Powershell_ise (these 2 are not frequently used by me. And attackers usually want to execute these 2 to perform fileless attacks.
...... cmd, blocked for the same reason as Powershell
...... mmc is the base application for Group Policy Editor, Local Security Policy, Device Manager and some others. If an attacker can reach this, they can disable a lot of defenses.
...... MoUsoCoreWorker is part of Windows Update. I don't run Windows Update, because last year 2023 I was attacked via Windows Update because a MS Certificate Leak allow hackers to sign malware posing as win updates. The leaked cert should be revoked by now, but I have gotten used to going to MS Update Catalog site to manually download and verify updates.
...... Drvinst is blocked for the same reason as Win Updates, drvinst installs drivers
...... wuauclt is part of Win Update
...... BitLocker, BitLockerToGo I do not encrypt the hard drive nor USB sticks. My 12 yr old Core i5 is already slow as is, and nobody is going steal a 5 lb laptop.
....... SSH is blocked because it is a known hacker TTP to setup a backdoor using this, source OSINT.
...... WerFault is blocked because I don't send error reports to MS
. Firewall
... Application Rules. Only contains a select few Windows exe's that are necessary for MS Account sign in , Outlook and smartscreen etc.
So because of the HIPS blocks, you will need to turn off HIPS protection if you want to use any of the above blocked exe's.
To download the config file, just click on the Play button inside the Spoiler.
]
Last edited:
The new HIPS has a protection block, This allows you to block LoLBins. Because CIS Beta does not allow you to virtualize Windows exe's. But HIPS Rules allow you to restrict a Windows exe somewhat.The added value over a HIPS is questionable when you also apply containment through sandboxing. It is possible to disable the HIPS, so forget that module also.
Last edited:
Regarding LoLBins, far too often folk will block legitimate Windows executables in the hope of preventing malicious actions- this is often seen by totally blocking things like wscript and/or powershell, both of which, although created for high and noble purposes can obviously be exploited in many ways. Such blanket blocks may indeed prevent malicious actions to proceed, but may also lead to the OS not functioning properly.The new HIPS has a protection block, This allows you to block LoLBins. Because CIS Beta does not allow you to virtualize Windows exe's. But HIPS Rules allow you to restrict a Windows exe somewhat.
The best method of preventing a LoLbin infection is to prevent the malicious action that can arise from a valid Windows exe and not the actual exe itself. The containment module of Comodo will do just that without the need for excessive HIPS blocking rules being created.
An example would be something like certutil.exe, which can be used to configure Certificate services and to verify certificates. It can also be used for various nasty things, most commonly in Ransomware to encrypt files.
To see how Comodo containment would deal with a potentially malicious action arising from certutil.exe. consider this (and this is TOTALLY safe to do):
We can add a command to certutil to direct it to download something from somewhere (trojans love this)- for example let's have certutil connect out and download 7Zip from the 7Zip website and save it---
Copy this to Notepad and save it as test.bat-
"certutil.exe -urlcache -split -f http://7-zip.org/a/7z1604-x64.exe 7zip.exe"
Plop that batch file in a directory and run it with containment disabled. You will see a connection out and the 7zip application downloaded to that directory. Also note that no FW alert will be seen if the FW module is in Safe Mode as certutil is trusted.
Now try it with Comodo Containment enabled at any level. The potentially malicious will be prevented without the need for totally block on certutil itself, no fancy Rules needed which would restrict legitimate Windows functions without added to malware protection.
m
Depends on the environment and needs of the users. A lot of times it doesn’t lead to any breakage on business environments that are focused on performing a set of tasks. Problem is more emphasised with home users who are unpredictable.but may also lead to the OS not functioning properly
I still use CF .8012 Stable when I run it since containment and firewall element hasn't changed. Beta 3 still being worked on so will wait for a stable before changing versions though betas ran okay when I tested them apart from sometimes leaving some leftover drivers.
@cruelsister
Hi,
I think you're the best person to ask. I am trying to install Sumo Logic SIEM collector on a PC. I have tried adding several Fie Groups to a firewall rule to make the Connector installer talk with the Sumo Logic server, Executables, Applications, and Temp Files; all using the Allowed Application rule for the installer.exe. But it always fails. Finally I decided to try turning off Comodo CIS Beta 2024's firewall and use Windows Firewall with it's default Outbound Allow policy and that worked. Am I doing something wrong? Or doesn't CIS BETA 2024 recognize the temp exe's that are created as children of the installer and not letting them go outbound ?
Hi,
I think you're the best person to ask. I am trying to install Sumo Logic SIEM collector on a PC. I have tried adding several Fie Groups to a firewall rule to make the Connector installer talk with the Sumo Logic server, Executables, Applications, and Temp Files; all using the Allowed Application rule for the installer.exe. But it always fails. Finally I decided to try turning off Comodo CIS Beta 2024's firewall and use Windows Firewall with it's default Outbound Allow policy and that worked. Am I doing something wrong? Or doesn't CIS BETA 2024 recognize the temp exe's that are created as children of the installer and not letting them go outbound ?
I have used Comodo Internet Security, but I'm no expert. I would suggest enabling "Custom Ruleset or Create Rules for Safe Applications or Training Mode" for the firewall to solve your problems.I am trying to install Sumo Logic SIEM collector on a PC. I have tried adding several Fie Groups to a firewall rule to make the Connector installer talk with the Sumo Logic server, Executables, Applications, and Temp Files; all using the Allowed Application rule for the installer.exe. But it always fails. Finally I decided to try turning off Comodo CIS Beta 2024's firewall and use Windows Firewall with it's default Outbound Allow policy and that worked. Am I doing something wrong? Or doesn't CIS BETA 2024 recognize the temp exe's that are created as children of the installer and not letting them go outbound ?
Edit: You can also check excluding your software under "Miscellaneous: Don't detect shellcode injections in these applications" to solve the problem.
Last edited:
Do you have further details of what's specifically being blocked? I might be worth installing Sumo before installing CIS but if you can provided further details, that'll help identify what the issue is.@cruelsister
Hi,
I think you're the best person to ask. I am trying to install Sumo Logic SIEM collector on a PC. I have tried adding several Fie Groups to a firewall rule to make the Connector installer talk with the Sumo Logic server, Executables, Applications, and Temp Files; all using the Allowed Application rule for the installer.exe. But it always fails. Finally I decided to try turning off Comodo CIS Beta 2024's firewall and use Windows Firewall with it's default Outbound Allow policy and that worked. Am I doing something wrong? Or doesn't CIS BETA 2024 recognize the temp exe's that are created as children of the installer and not letting them go outbound ?
Let's try something simple first- As shutting off the Comodo firewall will allow the app to connect out, the issue is obviously with CF. So delete all the Rules you made, then put the Firewall in "Custom Ruleset". Now open the problem application, note the FW popups and allow them.
Change the FW setting back to Safe Mode.
Reboot (you really don't have to do this, but I'm in a talkative mood). Now open the app you are having issues with and see if all is fine.
Really hope this helped!
Change the FW setting back to Safe Mode.
Reboot (you really don't have to do this, but I'm in a talkative mood). Now open the app you are having issues with and see if all is fine.
Really hope this helped!
We can add a command to certutil to direct it to download something from somewhere (trojans love this)- for example let's have certutil connect out and download 7Zip from the 7Zip website and save it---
Copy this to Notepad and save it as test.bat-
"certutil.exe -urlcache -split -f http://7-zip.org/a/7z1604-x64.exe 7zip.exe"
Not using Comodo, but fwiw I did try this and SRP utilized in @Andy Ful 's WHHL hardening tool blocked it. After I created a path rule to allow it, Windows Security blocked it.
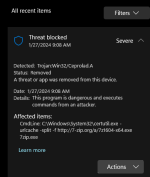
Blocked my MD and CL/VS if in Download folder
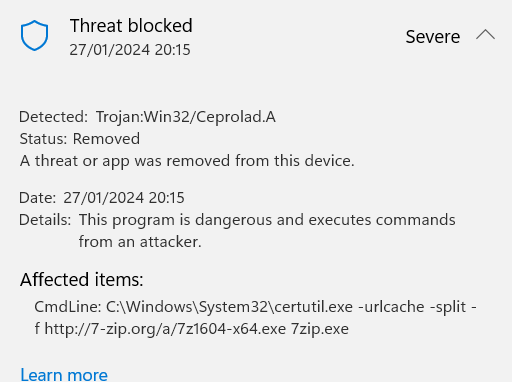
Blocked by Cyberlock/VS in User directory
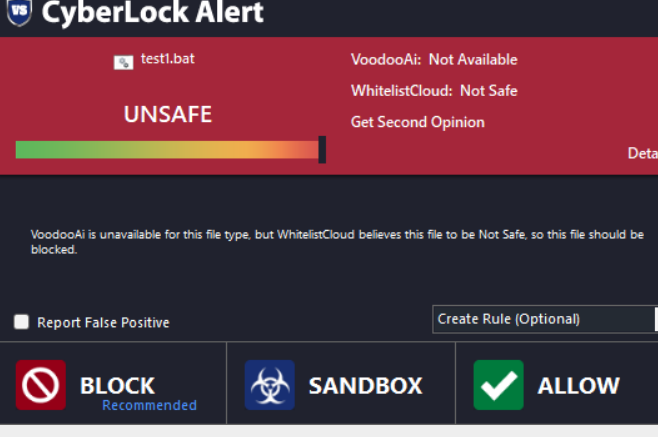
But if find CF is faster at blocking no matter where on the system and for some reason I had to restart before CL/VS blocked it but I don't always shutdown/restart my machine unless I'm installing something. Very useful little test though, thanks @cruelsister
Blocked by Cyberlock/VS in User directory
But if find CF is faster at blocking no matter where on the system and for some reason I had to restart before CL/VS blocked it but I don't always shutdown/restart my machine unless I'm installing something. Very useful little test though, thanks @cruelsister
@cruelsister , latest development. Sumo Logic released a new installer for their agent. And it has an unpacker, which I could not get past. I have disabled Comodo's AV and VirusScope, and I have disabled Windows Defender real time protection, and added the installer to Windows Defender's exclusions. None has helped. And I had stupidly deleted the previous installer which didn't have such a problem.
So I have written to Sumo Logic complaining about this. Lets see what the new week brings.
So I have written to Sumo Logic complaining about this. Lets see what the new week brings.
The only thing that I miss when comparing CIS 2024 Beta to Xcitium's CIS is that each Containment Rule has a Enable/Disable slider in Xcitium. And 2024 Beta doesn't. I have notified them.
Last edited:
You may also like...
-
App Review DrWeb Security Space BETA
- Started by Shadowra
- Replies: 11
-
App Review COMODO Internet Security 2025 Premium
- Started by Shadowra
- Replies: 106
-
App Review PCMatic Antivirus Home 2026
- Started by Shadowra
- Replies: 12
-
App Review ArcaBit Internet Security 2025
- Started by Shadowra
- Replies: 11
-
App Review Malwarebytes Anti-Malware Premium BETA
- Started by Shadowra
- Replies: 44

