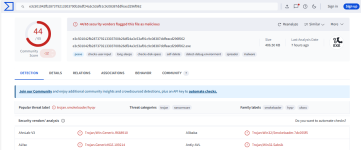
If u disable Cloud then how will Xcitium rate the files as Malicious or Safe?
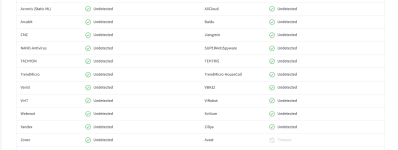
The signature detection still works, so malicious files are detected. All other files will be Unrecognized for Comodo, except files Trusted by the user or Trusted Vendor.
Such a setup is common in Enterprises where AppLocker or Windows Defender Application Control is applied.
Will it be Unknown forever?
Yes, except when the user adds the vendor to the Trusted Vendors or Trusted files.
Of course, the user can enable Cloud Lookup from time to time if necessary.