Ahh, "Manage exclusions"....so, stored locally vs. timed exclusion. Thanks
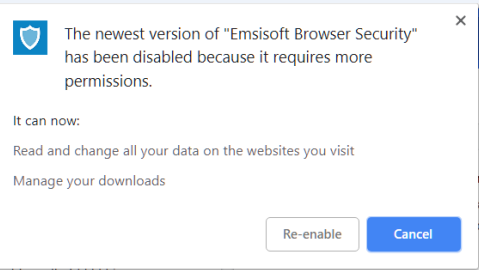
New Update Emsisoft Browser Security
- Thread starter Fabian Wosar
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Correct. The exclusions are also synched if you have syncing enabled in your browser.Ahh, "Manage exclusions"....so, stored locally vs. timed exclusion. Thanks
Is this extension gonna stay free to use in future aswell, without having to purchase something from emsisoft?
Installed on chrome, and looking forward antimalware, competing with zemana
Installed on chrome, and looking forward antimalware, competing with zemana
Hope Zemana will develop an extension soonIs this extension gonna stay free to use in future aswell, without having to purchase something from emsisoft?
Installed on chrome, and looking forward antimalware, competing with zemana
We have no plans to monetise it now or in the future. So unless something drastic or unexpected happens, it will continue to be free.Is this extension gonna stay free to use in future aswell, without having to purchase something from emsisoft?
Quick question: I installed Emisoft browser ext. and so far, it resides nicely in Firefox/Sandboxie, no slowdowns, etc. Decided to test via AMTSO dummy phishing page, and the page opened. Noticed that Emsisoft is not among the vendors that specifically support this AMTSO function. So, are there instances where Emsisoft would NOT react and be the first responder? For example, I tried another dummy page, and this time, Firefox showed its red teeth warning about a malware site. Nothing (yet) from Emsi.
I think alongside a couple of privacy/adblockers, this would make a great addition once it's refined.
I think alongside a couple of privacy/adblockers, this would make a great addition once it's refined.
@Fabian Wosar
First thanks for providing a cloud based URL-block web extension. Nice touch to use hashes for privacy, but from a marketing perspective I have some doubts on the idea (and success) of this new extension . . .
When so many people don't seem to care about their privacy, why target a new product sor such a small (possibly minor) user group? Taking into consideration that the timing is at best late for providing a free extension (read diffusion of innovation of E. M. Rogers)
I don't have user segment data to proof it, but my guess is that most privacy aware people are also security aware. So you are providing a benefit (privacy) and a disappointment (no payload download protection) simultaneously when comparing this extension with extensions from other security companies.
I know you explained Evjl's Rain that it us supposed to not block payloadsm but testing agencies like AV-lab test extensions on this feature also! IMO you don't need to be a marketing guru (like me ) to predict that this extension will NOT be installed on many PC's. So here is a free tip.
) to predict that this extension will NOT be installed on many PC's. So here is a free tip.
Why not provide two modes. The 'full URL' mode works like the current functionality en is intended to be used by people who are already using EMSISOFT security products. The easy explanation(rational) is that EMSISOFT ANTIMALWARE will deal with the downloaded payload anyway.
For all other users (non EMSISOFT customers) the extension works in 'partial URL' mode. The URL is only hashed until the first /. So payloads listed in VX-VAULT URL are blocked because all downloads from the hosting websites are blocked: e.g.
HTTP(S)://www.malware_hosting_website.com/payload_page/malware.exe
This has the disadvantage that the webpage of hacked websites which are clean are also blocked. When downloads of malware hosting or infected websites are blocked, you could also show a small info bar at the bottom of the warning prompt (or call to action: want to access this website safely? install etc).
Regards Kees
First thanks for providing a cloud based URL-block web extension. Nice touch to use hashes for privacy, but from a marketing perspective I have some doubts on the idea (and success) of this new extension . . .
When so many people don't seem to care about their privacy, why target a new product sor such a small (possibly minor) user group? Taking into consideration that the timing is at best late for providing a free extension (read diffusion of innovation of E. M. Rogers)
I don't have user segment data to proof it, but my guess is that most privacy aware people are also security aware. So you are providing a benefit (privacy) and a disappointment (no payload download protection) simultaneously when comparing this extension with extensions from other security companies.
I know you explained Evjl's Rain that it us supposed to not block payloadsm but testing agencies like AV-lab test extensions on this feature also! IMO you don't need to be a marketing guru (like me
Why not provide two modes. The 'full URL' mode works like the current functionality en is intended to be used by people who are already using EMSISOFT security products. The easy explanation(rational) is that EMSISOFT ANTIMALWARE will deal with the downloaded payload anyway.
For all other users (non EMSISOFT customers) the extension works in 'partial URL' mode. The URL is only hashed until the first /. So payloads listed in VX-VAULT URL are blocked because all downloads from the hosting websites are blocked: e.g.
HTTP(S)://www.malware_hosting_website.com/payload_page/malware.exe
This has the disadvantage that the webpage of hacked websites which are clean are also blocked. When downloads of malware hosting or infected websites are blocked, you could also show a small info bar at the bottom of the warning prompt (or call to action: want to access this website safely? install etc).
Regards Kees
Last edited:
They are not doing it to gain a million users. They are doing to improve the detection of EAM and they will eventually probably offer to install it on installation of EAM. That implies that they need to have the same privacy requirements as their main product or they will lose clients.@Fabian Wosar
First thanks for providing a cloud based URL-block web extension. Nice touch to use hashes for privacy, but from a marketing perspective I have some doubts on the idea (and success) of this new extension . . .
When so many people don't seem to care about their privacy, why target a new product sor such a small (possibly minor) user group? Taking into consideration that the timing is at best late for providing a free extension (read diffusion of innovation of E. M. Rogers)
I don't have user segment data to proof it, but my guess is that most privacy aware people are also security aware. So you are providing a plus (privacy) and a disappointment (no payload download protection) simultaneously.
You don't need to be a marketing guru to predict that this extension will NOT be installed on many PC's. So here is a free tip.
Why not provide two modes. The 'full URL' mode works like the current functionality en is intended to be used by people who are already using EMSISOFT security products. The easy explanation(rational) is that EMSISOFT ANTIMALWARE will deal with the downloaded payload anyway.
For all other users (non EMSISOFT customers) the extension works in 'partial URL' mode. The URL is only hashed until the first /. So payloads listed in VX-VAULT URL are blocked because all downloads from the hosting websites are blocked: e.g.
HTTP(S)://www.malware_hosting_website.com/payload_page/malware.exe
This has the disadvantage that the webpage of hacked websites which are clean are also blocked. When downloads of malware hosting or infected websites are blocked, you could also show a small info bar at the bottom of the warning prompt (or call to action: want to access this website safely? install etc).
Regards Kees
The privacy focus of EAM and this extension markets really well to the older clientele they have, so it makes no sense for them to move away from it.
Last edited:
They are not doing it to gain a million users. They are doing to improve the detection of EAM and they will eventually probably offer to install it on installation of EAM. That implies that they need to have the same privacy requirements as their main product or they will lose clients.
The privacy focus of EAM and this extension markets really well to the older clientele they have, so it makes no sense for them to move away from it.
For this extension to improve detection od EAM, it needs to be installed by non-EAM users also (url blocking is a numbers game). So it still does not make any sense, because (non-EAM) users will compare it with MalwareBytes, Avira Browser Safety, Bitdefender, Windows Defender Browsing protection and choose for extenstions with better protection stats.
If you expect to get the url from users then you have already lost the game both detecting and also selling. There are many other sources to improve your detection than relying on users to report one.For this extension to improve detection od EAM, it needs to be installed by non-EAM users also (url blocking is a numbers game). So it still does not make any sense, because (non-EAM) users will compare it with MalwareBytes, Avira Browser Safety, Bitdefender, Windows Defender Browsing protection and choose for extenstions with better protection stats.
The developer already told you how this improves detection.
Extension - Emsisoft Browser Security
I don't think they care about non EAM users mate. I told you my assumption on the previous reply.
Last edited:
If you expect to get the url from users then you have already lost the game both detecting and also selling. There are many other sources to improve your detection tha relying on users to report one.
The developer already told you how this improves detection.
Extension - Emsisoft Browser Security
I don't think they care about non EAM users mate. I told you my assumption on the previous reply.
1. When other sources are sufficient, why develop an extension. Because Google and Microsoft collect more info from more devices they score better in URL blocking, as said URL blocking is a numbers game and for ANTIVIRUS protection it also is very important (For machine learning you need to feed/train the machine with data samples, more samples is more accurate recognition, it is as simple as that).
2.The more detailed nformation collection still works for EAM users in full URL mode. For collecting more detailed information the extension needs to be installed in the first place. That is not going to happen for most users when it fails in comparison to simular extensions of other AV's That is why I suggested the partial URL block mode, The fact is that people take payload downloads into accounts when comparing extensions (look at AV-test lab extension and @Evjl's Rain tests as example). It is user (customer) perception that counts, not the product developers purpose.
3. One rotten apple spoils the whole barrel impression
When the small Mercedes A felt over in the famous Goose test, it did not influence hard core brand addicts of Mercedes (mostly the more expensive bigger models). But it did impact cross-car-brand purchases. The people targeted by Mercedes (who bought smaller cars of competing brands like Audi and BMW) laughed about this incident and did not want to buy this car. It is a classic example how brand names can be affected by new products bearing the same brand name. How many people would be inclined to take the main EMSISOFT product into buying consideration when the extension of EMSISOFT is outperfomed in protection by extensions of other AV's. User perception does not need to be right and correct, but is the thing that counts for (buying/using) consideration.
Last edited:
Yes.It is. Fabian has posted it in this thread.Is this extension free?
~LDogg
It depends on how those mechanisms are implemented. The way the extension works is that when a webpage is loaded either in a browser window or any kind of frame, we will check it in the background whether it is malicious or not. The way most of the phishing filters that are part of the browser work is that they check before the website is loaded, so those will be consulted first. It's also the reason why most testers turn it off when testing security products. Products that use a local blocklist, like uBlock for example, will also intercept requests. The problem with intercepting requests, in general, is that it becomes difficult to differentiate between a website and resources on a website (like the pictures on a website for example). If your database is purely local, then verifying every single resource is fine, because it is incredibly fast. Via cloud that becomes an issue, as we essentially add about 50 - 100ms for the check on most systems. Given that pages often include 100 - 150 resources (pictures, CSS, JavaScript, etc.), adding 10 - 15 seconds of online lookups becomes unfeasible.Quick question: I installed Emisoft browser ext. and so far, it resides nicely in Firefox/Sandboxie, no slowdowns, etc. Decided to test via AMTSO dummy phishing page, and the page opened. Noticed that Emsisoft is not among the vendors that specifically support this AMTSO function. So, are there instances where Emsisoft would NOT react and be the first responder? For example, I tried another dummy page, and this time, Firefox showed its red teeth warning about a malware site. Nothing (yet) from Emsi.
The extension is solely developed to improve phishing detection in EAM. EAM will install it on the system or suggest installing it on the system, depending on the browser. We are well aware that it won't become a big hit with non-EAM users. So that's completely fine. The protection would be identical whether we send whole URLs to the server compared to what we do now. So why send the whole URL to the server?When so many people don't seem to care about their privacy, why target a new product sor such a small (possibly minor) user group? Taking into consideration that the timing is at best late for providing a free extension (read diffusion of innovation of E. M. Rogers)
We will just add the download handler to the next version of the extension. It will be missing on Edge, since Edge doesn't support the required interfaces, but that is probably okay. It looks like Microsoft stopped approving extensions for Edge anyways, probably because the upcoming switch to Blink/Chromium.I know you explained Evjl's Rain that it us supposed to not block payloadsm but testing agencies like AV-lab test extensions on this feature also! IMO you don't need to be a marketing guru (like me) to predict that this extension will NOT be installed on many PC's. So here is a free tip.
Pretty much, yes.They are not doing it to gain a million users. They are doing to improve the detection of EAM and they will eventually probably offer to install it on installation of EAM. That implies that they need to have the same privacy requirements as their main product or they will lose clients.
Because the only way to access the URL data without messing with all your SSL/TLS connections is as part of the browser.1. When other sources are sufficient, why develop an extension.
It is.Is this extension free?
OK, I rest my KeesWe are well aware that it won't become a big hit with non-EAM users. So that's completely fine
(probably only Dutch & Flemish understand
It's cool to see that they have a browser extension now. Now just improving the lists that Surf Protection uses.
We released an update to the extension today. The following things changed:
- During downloads, we now check the URL the file is being downloaded from and block the download if the source is considered malicious
- When submitting a URL, the user now gets a confirmation message and is prevented from submitting the same URL again for the rest of the browser session
- You can no longer report browser-internal pages like chrome://version or about:config anymore.
- Current status of the extension is now reflected in the icon (coloured icon if protection is on, monochrome when turned off)
Chrome >
Version 2018.12.0.10
Updated December 27, 2018
Version 2018.12.0.10
Updated December 27, 2018
Last edited:
Fabian,
Up front: great job, many thanks, I installed the extension. I am sure this valuable will make surfing on Internet even more secure.
That said, for me, to be honest, the "It appears that Browser Security is not enabled. ..etc" came as a surprise.
Huh!? .. Were there any changes to my browser? Have I not been surfing in a not-secure way then? What..?
Did I ignore notifications? Where to find additional information?
The extension-site that is showing up after clicking on 'Install now' provides a bare minimum on information (1 line).
I agree, that is the case with most extensions: they often leave the user with questions like in what way the extension works.
As for the Emsisoft extension, a Google search brought me to this site.
Your announcement at the top clearly outlines how it works.
Allow me to make a positively meant suggestion. IF... if at all possible, could you then add the 2 paragraphs of your announcement to the extension site?
It merely says there 'Blocks dangerous websites that distribute malware and prevents phishing attacks.'
Maybe add 'Learn more'to the pop-up, or change 'Install now' into 'Learn more'? After all, users will end up on the extension site either way.
Again, just an idea.
BTW, heading over to 'Related' I see a number of 'ad blocking' extensions.
Take it there are no conflicts with uBlock Origin?
Keep up the good work!
Up front: great job, many thanks, I installed the extension. I am sure this valuable will make surfing on Internet even more secure.
That said, for me, to be honest, the "It appears that Browser Security is not enabled. ..etc" came as a surprise.
Huh!? .. Were there any changes to my browser? Have I not been surfing in a not-secure way then? What..?
Did I ignore notifications? Where to find additional information?
The extension-site that is showing up after clicking on 'Install now' provides a bare minimum on information (1 line).
I agree, that is the case with most extensions: they often leave the user with questions like in what way the extension works.
As for the Emsisoft extension, a Google search brought me to this site.
Your announcement at the top clearly outlines how it works.
Allow me to make a positively meant suggestion. IF... if at all possible, could you then add the 2 paragraphs of your announcement to the extension site?
It merely says there 'Blocks dangerous websites that distribute malware and prevents phishing attacks.'
Maybe add 'Learn more'to the pop-up, or change 'Install now' into 'Learn more'? After all, users will end up on the extension site either way.
Again, just an idea.
BTW, heading over to 'Related' I see a number of 'ad blocking' extensions.
Take it there are no conflicts with uBlock Origin?
Keep up the good work!
You may also like...
-
Security News Zoom Stealer browser extensions harvest corporate meeting intelligence
- Started by Brownie2019
- Replies: 4
-
-
New Update Osprey Browser Protection discussion and updates
- Started by Gandalf_The_Grey
- Replies: 505
-
Malware News DarkSpectre Browser Extension Campaigns Exposed After Impacting 8.8 Million Users Worldwide
- Started by Gandalf_The_Grey
- Replies: 2