[*][Added] Notifications for various actions, e.g. filter updates
#1167
[*][Added] A notification with changelog after an update
#1025
[*][Added] "About" screen
#1135
[*][Added] $cookie modifier support
#961
[*][Added] "Submit a complaint" item to the right-click menu
#1072
[*][Added] Update filter after enabling it
#1181
[*][Added] Show notify when checking for filters update using context menu
#1073
[*][Changed] Wording for manual blocking tool options
#1169
[*][Changed] A forwarder is now used for all links
#1109
[*][Changed] Localizations have been updated
#1174
[*][Fixed] Assistant advanced settings button doesn't respond
#1091
[*][Fixed] $extension modifier prevents first-party URL blocking
#1122
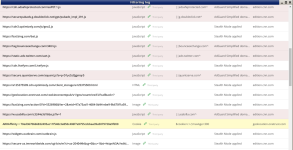
[*][Fixed] Invalid exclusions are created using Filtering Log
#1131
[*][Fixed] "Third-party" icon size in Filtering Log
#1069
[*][Fixed] Some hidden elements are not shown in the Filtering Log
#1123
[*][Fixed] Some requests are not visible in the Filtering Log
#1138
[*][Fixed] While in integration mode, new rules are not imported to the desktop AG User filter
#10
[*][Fixed] Incorrect file types are accepted when you try to import a User filter
#1039
[*][Fixed] AdGuard settings are not fully visible when accessing them from the overflow menu
#970
[*][Improved] $csp rules are now disabled if there's a document-level exception applied to the website
#1093
[*][Improved] Extension is now more friendly towards visually impaired users
#953
[*][Improved] Multiple $replace rules can be applied to a single web request now
#1092
[*][Improved] Network requests excluded by a rule in a custom filter can now be blocked
#1044
[*][Improved] "abp:subscribe" links are now intercepted properly
#1149
except for VoodooShield. Nice setup!