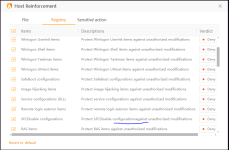
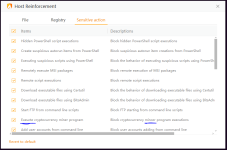
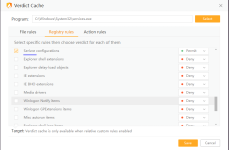
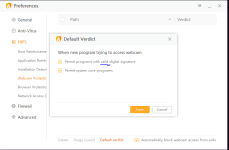
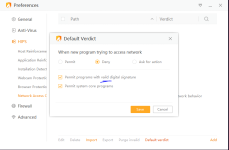
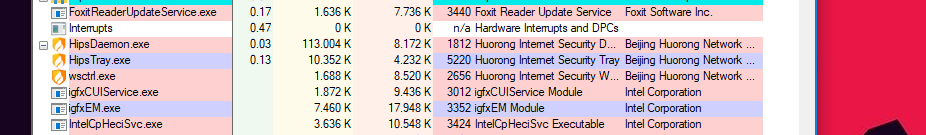
I would think twice before installing Chinese software, especially AV. That's a big red flag.
New Update Huorong Internet Security (Updates)
- Thread starter Petrovic
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
LOL, as a matter of fact, I fully understand you. Huorong is something different, perhaps you can try it in VM and it may somehow change your mind :-DI would think twice before installing Chinese software, especially AV. That's a big red flag.
Release Note for 5.0.44.0 (05/19/20)
Dear velvet users,
Hello! Thank you all for using velvet security software 5.0.
The following is today's update:
New features:
1. [Remote Login Protection] Support adding IP whitelist.
Program optimization:
1. Optimized pop-up interception library.
Program defect repair:
1. Fix the problem of slow scanning of GCC compiler.
2. Fix the problem that the log processing result is displayed incorrectly.
3. Fix the problem that search words and prompt text overlap.
4. Fixed the problem that the automatic upgrade caused the virus processing to fail.
5. Fixed the problem of black screen caused by importing wrong rules.
6. Fixed the issue that the official introduction function of the missing scan patch details page is invalid.
7. Fixed the problem that java component cannot be installed when real-time file monitoring is enabled.
8. Fixed the problem that the installation package automatically exits when the registry configuration item is an invalid directory.
9. Fixed the problem that the page will crash when importing custom rules without selecting the file point to open.
10. Fixed the issue that explorer.exe crashed after installing Tinder in 64-bit Citrix virtual environment.
11. Fixed the problem that the txt file containing system attributes in the root directory of the U disk will be scanned as a hidden file.
With your help, velvet is improving every day, thank you for your support!
Tinder operating team
May 19, 2020
@vardyh
Hey i saw u fix hard configurator conflict with Huorong. I would ask if is possible for u to implement in builtin/internal rules one for services.exe for allow it to manage service configuration under hips. I made a rule verdict but would be more helpfull (for others too) if u whitelist it program side. For what i understand services.exe is "made" for manage service configurations.
Another suggestion, i saw in default deny u cant install programs that u dont have installed already, so u have to allow all or use it. Is possible to implement a new way, like give a chance to install from a valid signed installer?
Hey i saw u fix hard configurator conflict with Huorong. I would ask if is possible for u to implement in builtin/internal rules one for services.exe for allow it to manage service configuration under hips. I made a rule verdict but would be more helpfull (for others too) if u whitelist it program side. For what i understand services.exe is "made" for manage service configurations.
Another suggestion, i saw in default deny u cant install programs that u dont have installed already, so u have to allow all or use it. Is possible to implement a new way, like give a chance to install from a valid signed installer?
Last edited:
@vardyh
Found some translation errors, hope are all. Will be good if u can fix them.
Found some translation errors, hope are all. Will be good if u can fix them.
Attachments
procexp64 is more accurateLol... it's lightweight is insane.
it's using private memory like most AVs doHere not scanning.
It doesn't seem Fire velvet Terminal Security Management System has anything special over SPEM.
That's really not true since WiseVector is chinese also! (But just to be fair and honest, never install anything "state/government owned"!)
Is this free and is it AV and firewall?Release Note for 5.0.44.0 (05/19/20)
I use an on-premise AV(SEP Managed by SPEM) with all telemetry disabled.That's really not true since WiseVector is chinese also! (But just to be fair and honest, never install anything "state/government owned"!)
Since many banks/Governments Worldwide use it in pretty sure it's good in terms of privacy.
it's free. av+firewall+hipsIs this free and is it AV and firewall?
@Petrovic can u modify thread name, cause is stable version now, no public beta.
Why do you in all places and by all ocasions compare everything to Symantec? We know that you are fan of it but sometime it's already boring and gives no profit to discuss.I use an on-premise AV(SEP Managed by SPEM) with all telemetry disabled.
Since many banks/Governments Worldwide use it in pretty sure it's good in terms of privacy.
@vardyh
Have another suggestion. Can u implement this function under custom rules. This will help create more efficient rules too. For example an anti-exe rule may need this.
Have another suggestion. Can u implement this function under custom rules. This will help create more efficient rules too. For example an anti-exe rule may need this.
Attachments
Last edited:
Usually I don't like Chinese AVs *COUGH Qihoo 360 COUGH* (no offense to anyone using them or the developers) but with all the positive praise this is getting, it seems pretty good.
I dont think av is strong (need improvement), but hips are good and give u the possibility to create custom rules, the firewall is good.Usually I don't like Chinese AVs *COUGH Qihoo 360 COUGH* (no offense to anyone using them or the developers) but with all the positive praise this is getting, it seems pretty good.
I am giving a try because the only 2 suite free are this and comodo.
Last edited:
Ok thanks, I do seem to remember giving this a once over a year or so ago! Can you disable AV and just firewall?it's free. av+firewall+hips
@Petrovic can u modify thread name, cause is stable version now, no public beta.
NopeOk thanks, I do seem to remember giving this a once over a year or so ago! Can you disable AV and just firewall?
You may also like...
-
-
New Update Huorong Internet Security v6.x
- Started by Dreams&Visions
- Replies: 1
-
App Review Huorong Internet Security v6.0.7.12 (Modified Setting)
- Started by janx
- Replies: 22
-
Serious Discussion A Habit-Based Guide to Internet Security
- Started by Divergent
- Replies: 2