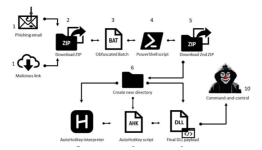
Sometimes there are ways to craft script files or use command lines that can bypass simple user space file blocking. So blocking sponsors is just an additional security layer should that happen. For example you can use a file type not covered by typical SRP such as .svg.
Agreed, and I do use OSArmor along with H_C to cover both scenarios of blocking scripts. But I think I can provide evidence as seen below where in the first partial log snippet from H_C events, H_C blocks the sample.hta script directly, without need to block a command line where the LOLBin might be involved.
Code:
Access to C:\Users\myself\Desktop\sample.hta has been restricted by your Administrator by the default software restriction policy level.In the second log snippet taken from OSArmor's logs, I have temporarily disabled H_C's "Default Deny", and this is where OSA leaps into action blocking "suspicious command line strings". For this part of the test I also disabled in OSA "Block execution of uncommon scripts".
Code:
Rule Name: Block execution of suspicious command-line strings
Command Line: "C:\WINDOWS\System32\WScript.exe" "C:\Users\myself\Desktop\ClsTS.vbs"So isn't WScript in the command line the LOLBin?
Either way, there is lots of overlap with these two utilities - maybe too much even - that can effectively block scripting type attacks.
EDIT
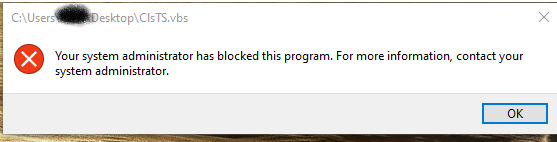
for better clarity, below is the same .vbs file blocked by H_C's SRP settings, where it kicks in before OSA.
Last edited: