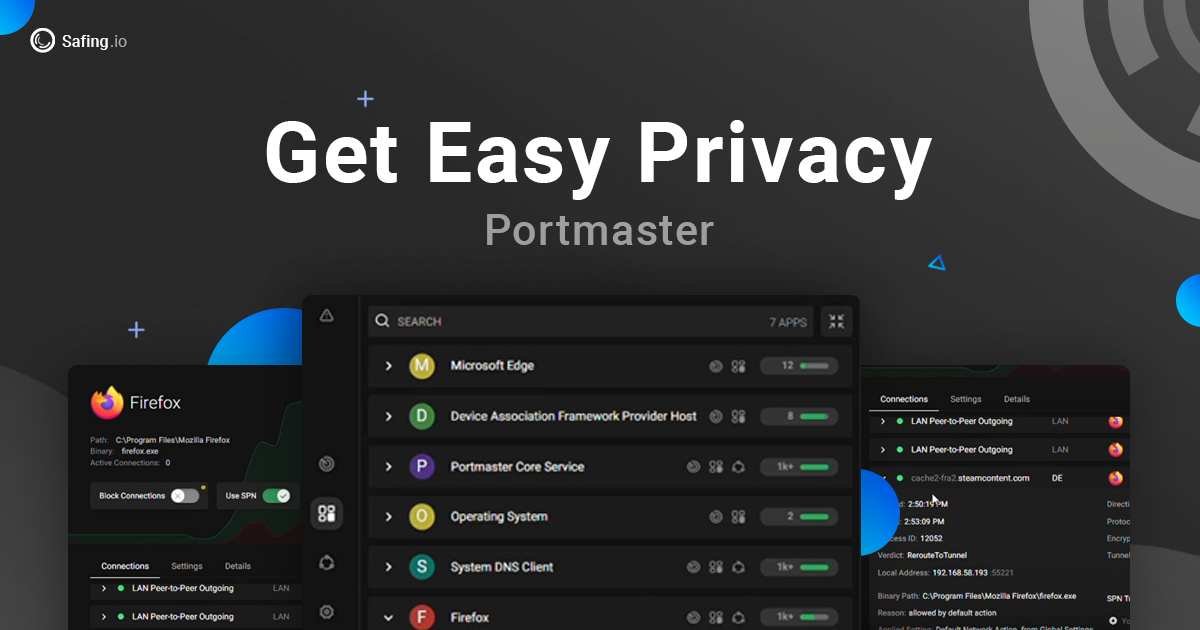
What do you mean by vb codes? Are they related to VBA features of MS Office (Macros, Add-ins, etc.)?
Do the original documents work differently after disabling H_C restrictions?
Most people infected via MS Office thought that the downloaded files were safe. Most of them were infected via MS Office macros or MS Office Add-ins. There are many other ways that can be adopted by the attackers in the near future to bypass the AV protection by using MS Office.
I do not have a convenient solution for you. Most security applications that protect MS Office use parent-child process monitoring, which is insufficient when you allow macros. I can only advise what I already posted:
Be safe.
- Use a safe application as the default program to open documents. So when you open the document, template, Add-in, etc., from the Desktop or Explorer (file explorer) it is not opened/installed via MS Office.
This can be done by the custom configuration of default applications via Windows Settings >> Apps & features >> Default apps >> Set defaults by app. Next, choose MS Office Word, Excel, PowerPoint, and change the default application that can open the listed file types to a safe application.- You can still open your documents by opening the MS Office application and using File >> Open from the application menu.
- If you must edit an unsafe document, then do not do it at once. Check it online and if it looks clean, then open it in MS Office after one or more days.
- You can additionally use Defender with ASR rules or anti-exploit solutions related to MS Office.
- Harden your firewall to block LOLBins' connections or use H_C to block popular LOLBins.
- Learn to recognize phishing attempts.

for example a VB code, but when I applies, and open my document, this type of VB codes don't work anymore...
I have to make a copy one to restore that primary restore the values on H_C.