Don't worry. He wants to know if there are conflicts in Windows, etc. Use the VS website to contact him.I would contact Dan immediately but I am skeptical as I am running the free version and not the Pro.
VoodooShield Latest
- Thread starter vtqhtr413
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Thanks for the tip! Will do.Don't worry. He wants to know if there are conflicts in Windows, etc. Use the VS website to contact him.
Unbelievably rapid reply from Dan below:
Quote
-----------------------------
Hi George,
Sorry about that… I actually just now finished the new CommandLineCloud feature so you will not experience those blocks anymore. If for some odd reason you do, please let me know!
There are a couple of blocks related to Kaspersky and Avira browser plugins that I still need to fix, but other than that we are pretty much good to go on the CommandLineCloud feature.
Thank you,
Dan
-----------------------------
Unquote
It was so nice to see how active and helpful he is, he put a smile on my face.
He deserves purchasing a Pro license the soonest just for that.
Quote
-----------------------------
Hi George,
Sorry about that… I actually just now finished the new CommandLineCloud feature so you will not experience those blocks anymore. If for some odd reason you do, please let me know!
There are a couple of blocks related to Kaspersky and Avira browser plugins that I still need to fix, but other than that we are pretty much good to go on the CommandLineCloud feature.
Thank you,
Dan
-----------------------------
Unquote
It was so nice to see how active and helpful he is, he put a smile on my face.
He deserves purchasing a Pro license the soonest just for that.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Hey Guys, sorry I have been away, I have been finishing up the CommandLineCloud feature, and it is fully up and running now, so command line blocks should be few and far between now.
In this version, the MpSigStub.exe issue is fixed, along with a fix for when a firewall was blocking WLC and VoodooAi.
VS 6.06a
https://voodooshield.com/Download/InstallVoodooShield606a.exe
SHA-256: 22e504f453955d8ca54a1e0157f95168295d00751fdf5f310de5dcd891365589
Thank you guys!
VoodooShield 5.70 – Page 19 – VoodooForums
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Hey guys, here is 6.06b. Just a few small bug fixes.
VS 6.06b
https://voodooshield.com/Download/InstallVoodooShield606b.exe
SHA-256: a1df08121a0beb6309af6994e122f07a0d55a1ea70470c71bb2cb068ba179251
BTW, since we are almost finished working out all of the last few bugs in VS 6.0, and since that is the only thing we discuss on this forum, I was thinking we might want to close the forum and if you guys have any issues, you can just email me directly? What do you guys think? Thank you!
VoodooShield 5.70 – Page 20 – VoodooForums
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
To keep this up to date, VoodooShield version 6.06c released:
Here is a version that should fix the AutoPilot bug that @harlan4096 found, and actually it probably affected other file types than just .jar. The bug was related to when I recently replace VT with WLC in VS's Rules (similar to the bug that @Lenny_Fox recently encountered). It's funny, you can actually disable the one default rule in VS then the .jar file is blocked, so if we would not have had the one default rule, it probably would have been a very long time before we discovered this bug.
I did not have the same .jar file that @harlan4096 tested with, so I used a different sample, but if it is okay with @harlan4096, it might be a good idea to test the first .jar sample again... because if for some reason the bug is not fixed then I would probably need to debug with the actual sample to make sure the bug is completely fixed before we continue testing. Thanks again!
VS 6.06c
SHA-256: 083dd2ac20fa6fb6bed29969fabcdfbdb9caf4094ced85b70563911e85d8545c
Hi guys,
What do you think about adding to VS the autoblock feature for some cases (the custom non-default setting)? For example:
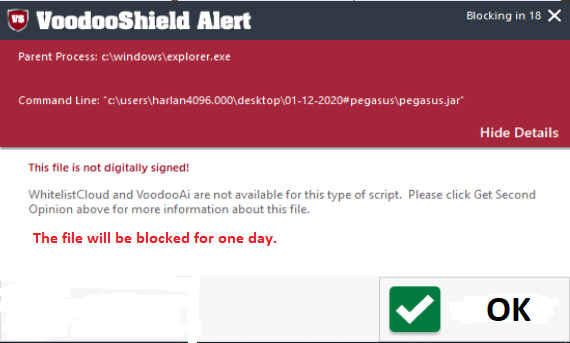
Instead of:
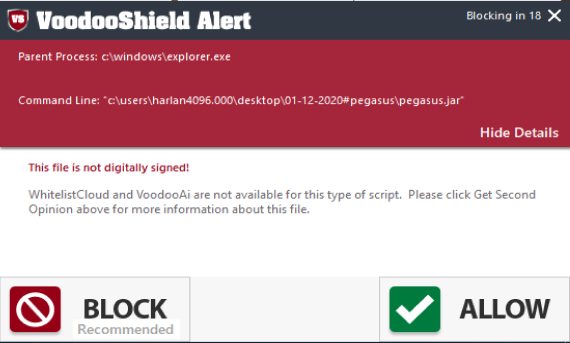
The number of days can be also configured. A similar defense for unsafe files (unknown classification) is applied in Comodo and WD (ASR rule) for EXE files. But in VS it could be applied for cases with unknown classification.
There was discussion about it in the thread:
(1) Q&A - Windows Defender Delay Protection. | MalwareTips Community
What do you think about adding to VS the autoblock feature for some cases (the custom non-default setting)? For example:
Instead of:
The number of days can be also configured. A similar defense for unsafe files (unknown classification) is applied in Comodo and WD (ASR rule) for EXE files. But in VS it could be applied for cases with unknown classification.
There was discussion about it in the thread:
(1) Q&A - Windows Defender Delay Protection. | MalwareTips Community
Last edited:
Thank you Andy, that is a great idea! We might want some kind of work around like maybe a captcha (even though they are a real pain) just in case a file needs to be allowed right away. But either way, creating an additional obstacle of some kind for unknowns would increase VS's overall security dramatically. Maybe we can brainstorm and see what everyone can some up with for an additional obstacle for unknowns.Hi guys,
What do you think about adding to VS the autoblock feature for some cases (the custom non-default setting)? For example:
View attachment 250254
Instead of:
View attachment 250255
The number of days can be also configured. A similar defense for unsafe files (unknown classification) is applied in Comodo and WD (ASR rule) for EXE files. But in VS it could be applied for cases with unknown classification.
There was discussion about it in the thread:
(1) Q&A - Windows Defender Delay Protection. | MalwareTips Community
For me a working way to get possible false positives reported and fixed would be more important. Seeing an "unsafe" for a file for days doesn't help me when I consider it a fp.
One does not exclude another. Every proactive detection has some space between "probably malicious" and "probably safe". This space is usually the largest for scripting attacks (generally for non-PE executables).For me a working way to get possible false positives reported and fixed would be more important. Seeing an "unsafe" for a file for days doesn't help me when I consider it a fp.
For now, there does not exist a good detection method for such cases which could avoid many false positives.
Anyway, the advanced user does not have to use the proposed feature - it will not be obligatory. Of course, it is not an ideal solution, too.
Edit.
One could consider such a feature as a kind of external sandbox. The unsafe file is not executed immediately in the system but delayed by one (or more days) for execution outside the system (computers of other people). In this time the malware is usually recognized by the AV (in the cloud) or classified on Virus Total.
Last edited:
VS already has an obstacle for unknowns, but I like the way @Andy Ful is thinking in that we should be able to enhance this in some way.
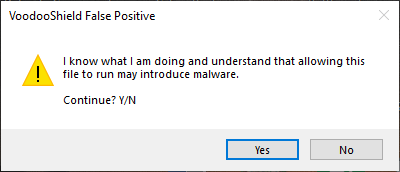
We also already have these options for business users...
- Require admin approval before letting the user allow new, non-whitelisted files (disables left click of VoodooShield)
- Analyze items the user wants to allow with Cuckoo Sandbox and post an alert in the Management Console
When UAC was announced as a new feature before the Windows Vista release in 2006, I was super excited because I was tired of my clients being infected with malware, and I was under the impression that it was going to solve the malware crises. UAC has come a very long way since then, but I personally believe it still lacks a lot of important features, such as file insight and user recommendations. When I first thought of the idea for VS several years later, I immediately realized that it was going to end up being an enhanced version of UAC, that was specifically designed to block malware. From what I remember, Microsoft's main purpose for UAC was to gently persuade devs to stop running everything as Admin, and it was not specifically designed as an antimalware mechanism.
The reason I mention this is because I think a lot of people misunderstand VS's purpose. Modern AV's are going to stop 95-99%+ of all malware. VS is designed to complement the AV by blocking potential malware pre-execution so as to give the user pause and a second chance of blocking malware, especially when they are just clicking away and not paying attention. Combined with an AV, VS provides an additional robust level of protection.
There are 2 possible scenarios that we should consider...
1. VS is blocking an item that the user is trying to run or install. In this case, the user thinks "ohhh, VoodooShield is blocking this thing I am trying to run", and they kind of chuckle. The reason I know this is because even to this day I hear this on the phone when helping a customer via remote when they download the remote software. And believe me, they chuckle. Every single time .
.
2. The user is browsing the web or checking email and VS blocks something out of the blue (especially when just clicking away or not paying attention). The user simply thinks that VS blocked something from infecting their computer, so they just ignore the VS prompt and are happy that VS "saved them".
You can actually configure VS to lock everything down and to block everything without a single prompt, and there are other products that are designed to function this way as well. There are certainly use cases for a total lockdown, for example ATM and voting machines. But for endpoints that the user interacts with on a daily basis, I think most end users want their computer to be as usable as possible.
Having said all that, if anyone can think of a better secondary obstacle, I think it is certainly worth exploring.
We also already have these options for business users...
- Require admin approval before letting the user allow new, non-whitelisted files (disables left click of VoodooShield)
- Analyze items the user wants to allow with Cuckoo Sandbox and post an alert in the Management Console
When UAC was announced as a new feature before the Windows Vista release in 2006, I was super excited because I was tired of my clients being infected with malware, and I was under the impression that it was going to solve the malware crises. UAC has come a very long way since then, but I personally believe it still lacks a lot of important features, such as file insight and user recommendations. When I first thought of the idea for VS several years later, I immediately realized that it was going to end up being an enhanced version of UAC, that was specifically designed to block malware. From what I remember, Microsoft's main purpose for UAC was to gently persuade devs to stop running everything as Admin, and it was not specifically designed as an antimalware mechanism.
The reason I mention this is because I think a lot of people misunderstand VS's purpose. Modern AV's are going to stop 95-99%+ of all malware. VS is designed to complement the AV by blocking potential malware pre-execution so as to give the user pause and a second chance of blocking malware, especially when they are just clicking away and not paying attention. Combined with an AV, VS provides an additional robust level of protection.
There are 2 possible scenarios that we should consider...
1. VS is blocking an item that the user is trying to run or install. In this case, the user thinks "ohhh, VoodooShield is blocking this thing I am trying to run", and they kind of chuckle. The reason I know this is because even to this day I hear this on the phone when helping a customer via remote when they download the remote software. And believe me, they chuckle. Every single time
2. The user is browsing the web or checking email and VS blocks something out of the blue (especially when just clicking away or not paying attention). The user simply thinks that VS blocked something from infecting their computer, so they just ignore the VS prompt and are happy that VS "saved them".
You can actually configure VS to lock everything down and to block everything without a single prompt, and there are other products that are designed to function this way as well. There are certainly use cases for a total lockdown, for example ATM and voting machines. But for endpoints that the user interacts with on a daily basis, I think most end users want their computer to be as usable as possible.
Having said all that, if anyone can think of a better secondary obstacle, I think it is certainly worth exploring.
Hey guys, here is the latest version that includes a few minor bug fixes / refinements that you guys have found, and a few that I always wanted to fix but never got around to doing so.
1. VS will now only display the digital signature file insight for files that can actually be digitally signed. It kind of worked this way before, but VS's list of signable files included files (mainly scripts) that could not actually be signed. (Thank you @McMcbrad!)
2. Some of the WhitelistCloud file types did not scan correctly for manual scans (and possibly on execution scans), but this is fixed now.
3. VS Free users are now limited to creating 3 Rules. I also removed the Rule combo box in the user prompt for Free uses so they do not think it somehow magically disappeared. (Thank you @Lenny_Fox!)
4. The countdown timer in the user prompt is now fixed. Users used to be confused why the countdown would pause at times (due to the mouse hovering on the user prompt), so now it should make more sense to the end user.
5. The VoodooShield Rules should be just about right now, but if you guys find anything, please let me know!
6. Several other small minor refinements
None of these changes should affect the results of the current Malware Hub tests, except for possibly the #2 item above (and it would be a minor issue if it did).
VS 6.06d
SHA-256: f1a21862697589291d7d17511975bfdc291b238672c5f107668502d597c428c6
Thank you guys!
1. VS will now only display the digital signature file insight for files that can actually be digitally signed. It kind of worked this way before, but VS's list of signable files included files (mainly scripts) that could not actually be signed. (Thank you @McMcbrad!)
2. Some of the WhitelistCloud file types did not scan correctly for manual scans (and possibly on execution scans), but this is fixed now.
3. VS Free users are now limited to creating 3 Rules. I also removed the Rule combo box in the user prompt for Free uses so they do not think it somehow magically disappeared. (Thank you @Lenny_Fox!)
4. The countdown timer in the user prompt is now fixed. Users used to be confused why the countdown would pause at times (due to the mouse hovering on the user prompt), so now it should make more sense to the end user.
5. The VoodooShield Rules should be just about right now, but if you guys find anything, please let me know!
6. Several other small minor refinements
None of these changes should affect the results of the current Malware Hub tests, except for possibly the #2 item above (and it would be a minor issue if it did).
VS 6.06d
SHA-256: f1a21862697589291d7d17511975bfdc291b238672c5f107668502d597c428c6
Thank you guys!
RoboMan
Level 38
Verified
Honorary Member
Top Poster
Content Creator
Well-known
High Reputation
Forum Veteran
This hurted my soul3. VS Free users are now limited to creating 3 Rules.
@danb
Regarding the 3 rules in free, I have a question.
Do they overwrite the default rule or are they applied before the default rule?
In the latter (the default rule as a catch all last rule to be applied) drop through logic errors are prevented (e.g. user not defining a rule for certain folders)
Regards Lenny
Regarding the 3 rules in free, I have a question.
Do they overwrite the default rule or are they applied before the default rule?
In the latter (the default rule as a catch all last rule to be applied) drop through logic errors are prevented (e.g. user not defining a rule for certain folders)
Regards Lenny
How funnyThis hurted my soulLuckily I have a premium license

They won't overwrite the default rule, and actually, you can delete the default rule if you want, and add 3 of your own. I really just added the default rule as an example.@danb
Regarding the 3 rules in free, I have a question.
Do they overwrite the default rule or are they applied before the default rule?
In the latter (the default rule as a catch all last rule to be applied) drop through logic errors are prevented (e.g. user not defining a rule for certain folders)
Regards Lenny
You can also move rules up and down with the little arrow icons to the right. I hope that answers your question, but if not just let me know!
Hey guys,
Here is the latest, here is what changed...
1. Added encryption of quarantined files (thanks @harlan4096!)
2. Fixed a bug that Krusty found in the WLC Firewall feature
VS 6.06e
SHA-256: c6721bdb861b9c772f1e1edf67686d75cecd9fe3d0fafb9e264d55b548013b80
Have a great week, thank you guys!
Here is the latest, here is what changed...
1. Added encryption of quarantined files (thanks @harlan4096!)
2. Fixed a bug that Krusty found in the WLC Firewall feature
VS 6.06e
SHA-256: c6721bdb861b9c772f1e1edf67686d75cecd9fe3d0fafb9e264d55b548013b80
Have a great week, thank you guys!
Thanks to be sure I could write three rules in this orderHow funny.
They won't overwrite the default rule, and actually, you can delete the default rule if you want, and add 3 of your own. I really just added the default rule as an example.
You can also move rules up and down with the little arrow icons to the right. I hope that answers your question, but if not just let me know!
1. Allow rule for Microsoft Windows signed system wide
2. Block rule for C:\Users with low AI rating (effectively the default rule reversed: block everything above AI score of 33)
3. Allow rule for C drive
This would have the effect that
a) All Microsoft Windows signed will be allowed everywhere
b) All programs in C:\Windows, C:\ProgramData, C:\Program Files and C:\Program Files (x86) will alows be allowed
c) All programs in C:\Users will have to meet VoodooShield's default
d) All other programs in my other data partitions will also have to meet VS default rule (e.g my F, M and R drive)
Remember I have ConfigureDefender running on MAX (with ASR rules and Cloud level on Zero-Tolerance) and SimpleWindowsHardening blocks execution of scripts in all user folders (C:\Users and other data partitions).
As posted earlier, it would be interesting to see when DanB would launch a zero config VS-variant which is specially tuned as companion for Microsoft Defender. It would be interesting to see whether a mobile app like micro-licensing scheme would work on the desktop market also.
Question to MT-forum users: would you pay for a zero config VS-version which would only cost 1,95 (the price of a hamburger only) yearly?
For a small company like your's Dan selling half a million 2 dollar licenses annual would be a nice extra on top of your VS pro generated licenses? In the mobile market small (often one man band) company's are able to generate enough income using micro-licensing (1 to 5 dollar licenses are also called micro-licenses because the below 5 dollar licenses are paid with micro-payment systems).
Last edited:
Interesting suggestions, thank you! This is kind of how AutoPilot and Smart OFF modes already work, and it gets pretty complicated, but I would like to try to understand the rules you created a little better to see if we can optimize your rules or AutoPilot / Smart OFF better.Thanks to be sure I could write three rules in this order
1. Allow rule for Microsoft Windows signed system wide
2. Block rule for C:\Users with low AI rating (effectively the default rule reversed: block everything above AI score of 33)
3. Allow rule for C drive
This would have the effect that
a) All Microsoft Windows signed will be allowed everywhere
b) All programs in C:\Windows, C:\ProgramData, C:\Program Files and C:\Program Files (x86) will alows be allowed
c) All programs in C:\Users will have to meet VoodooShield's default
d) All other programs in my other data partitions will also have to meet VS default rule (e.g my F, M and R drive)
Remember I have ConfigureDefender running on MAX (with ASR rules and Cloud level on Zero-Tolerance) and SimpleWindowsHardening blocks execution of scripts in all user folders (C:\Users and other data partitions).
As posted earlier, it would be interesting to see when DanB would launch a zero config VS-variant which is specially tuned as companion for Microsoft Defender. It would be interesting to see whether a mobile app like micro-licensing scheme would work on the desktop market also.
Question to MT-forum users: would you pay for a zero config VS-version which would only cost 1,95 (the price of a hamburger only) yearly?
For a small company like your's Dan selling half a million 2 dollar licenses annual would be a nice extra on top of your VS pro generated licenses? In the mobile market small (often one man band) company's are able to generate enough income using micro-licensing (1 to 5 dollar licenses are also called micro-licenses because the below 5 dollar licenses are paid with micro-payment systems).
For your first rule, VS already auto allows Windows System files, except for example we do not want to globally allow wscript (along with many other vulnerable processes). So I guess what I am asking... is VS blocking something in Windows that it should not be blocking? Windows System files are signed with a special catalog (catroot) signature, which is why when you right click on most Windows System files to check the digital signature, that tab is missing. So Windows System files are actually signed, even though they do not have digital signature that you can see in the file properties. I think Microsoft does it this way to make signing of Windows System files easier... they basically sign all of the files when they build Windows.
Having said that, there are a lot of downloadable Microsoft products, such as Process Explorer that is signed by Microsoft with a standard digital signature. Are these the types of files that your first rule is intended to cover?
For your second and third rules, this happens automatically with VS in AutoPilot and Smart OFF modes, even if you delete the one default VS Rule. But if there is a way we can optimize it, please let me know! Please keep in mind that certain folders such as AppData and ProgramData are common hiding spots for malware, so these require special attention.
Maybe the best thing to do is to run VS on AutoPilot for a while, and if blocks anything that it shouldn't, we can figure out if it really should have been blocked or not, and if not, I can fix the block for AutoPilot and Smart OFF modes (these two modes act almost identical to each other). Either way, this should be a lot of help to optimize AutoPilot and Smart OFF and your custom VS Rules. Thank you!
For your first rule, VS already auto allows Windows System files, except for example we do not want to globally allow wscript (along with many other vulnerable processes). So I guess what I am asking... is VS blocking something in Windows that it should not be blocking? Windows System files are signed with a special catalog (catroot) signature, which is why when you right click on most Windows System files to check the digital signature, that tab is missing. So Windows System files are actually signed, even though they do not have digital signature that you can see in the file properties. I think Microsoft does it this way to make signing of Windows System files easier... they basically sign all of the files when they build Windows.
Nope, this is exactly what I had in mind, thanks for the educational explanation
Yes, but I now read that programs with same signer of already whitelisted programs are allowed also. So what I had in mind is already realized, no need to auto allow everything from C and exclude C:\Users wth a blockHaving said that, there are a lot of downloadable Microsoft products, such as Process Explorer that is signed by Microsoft with a standard digital signature. Are these the types of files that your first rule is intended to cover?
For your second and third rules, this happens automatically with VS in AutoPilot and Smart OFF modes, even if you delete the one default VS Rule. But if there is a way we can optimize it, please let me know! Please keep in mind that certain folders such as AppData and ProgramData are common hiding spots for malware, so these require special attention.
Maybe the best thing to do is to run VS on AutoPilot for a while, and if blocks anything that it shouldn't, we can figure out if it really should have been blocked or not, and if not, I can fix the block for AutoPilot and Smart OFF modes (these two modes act almost identical to each other). Either way, this should be a lot of help to optimize AutoPilot and Smart OFF and your custom VS Rules. Thank you!
Well than I will be using the three rules to tighten up my F (files) M (Media) drives, I will keep the default as last. On the F file no execution should ever appear (an slower SSD drive for my Office documents) and on the M-drive also no execution should appear, only with some large updates Microsoft sometimes used the M drive (it is a 2 TB HDD) because it is the drive with the most free space.
User request: maybe you could add a block execution for NON-OS partitions excluding Microsoft Windows and Microsoft hardware/driver co-signing
Marketeer remark: you are bonkers when you implement above request, because VS Free would be a near perfect whitelist solution.
Last edited:
Very cool! Yeah, there are tons of hardcoded rules that makeup AutoPilot and SmartOFF modes that we have tweaked and optimized over the years, and they have become a little complex under the hood. But basically the goal was to essentially do what you were doing with the 3 rules. It would be impossible to recreate everything that AutoPilot does in 3 rules, but if someone really wanted to, they could create 20-30 or so rules to emulate AutoPilot and customize it to their liking. That would take a lot of work though.Nope, this is exactly what I had in mind, thanks for the educational explanation
Yes, but I now read that programs with same signer of already whitelisted programs are allowed also. So what I had in mind is already realized, no need to auto allow everything from C and exclude C:\Users wth a block
Well than I will be using the three rules to tighten up my F (files) M (Media) drives, I will keep the default as last. On the F file no execution should ever appear (an slower SSD drive for my Office documents) and on the M-drive also no execution should appear, only with some large updates Microsoft sometimes used the M drive (it is a 2 TB HDD) because it is the drive with the most free space.
User request: maybe you could add a block execution for NON-OS partitions excluding Microsoft Windows and Microsoft hardware/driver co-signing
Marketeer remark: you are bonkers when you implement above request, because VS Free would be a near perfect whitelist solution.
And yeah, the Rules are really intended to customize VS to your unique system, just like the way you are doing now with blocking all executables on your F & M drives (great rules btw). Most users do not need to use the Rules feature, but it comes in handy for special scenarios that cannot be covered by AutoPilot / Smart OFF modes. For example, I only need to add one rule to allow everything in the Visual Studio source code folder (without file insight).
Believe it or not, AutoPilot and Smart OFF mode already has something quite similar to "block execution for NON-OS partitions excluding Microsoft Windows and Microsoft hardware/driver co-signing". But as I was saying, if you experience an odd block, just let me know and we will investigate and tweak the hardcoded rules as necessary. Unlike allow-by-default products, VS starts with deny-by-default, and over the years we have figured out different features, rules and mechanisms that are able to safely auto allow as many Safe items as possible... this is really what VS is all about.
On the "Marketeer remark"... I see exactly what you mean, and really, I did not necessarily intend for it to work out that way, but now I am happy that it did. See, when VS used to rely on VT for AutoPilot and Smart OFF mode, these modes were pretty secure, but now that WLC has replaced VT, these modes are MUCH more secure. So yeah, with WLC, VS Free works really well for most users. The goal is to expand our user base as much as possible and worry about revenues later
You may also like...
-
Security News Critical Dolby Codec Vulnerability Exposes Android Devices to Code Execution Attacks
- Started by Brownie2019
- Replies: 2
-
New Update F-secure protection introducing firewall in the latest updates?
- Started by RRlight
- Replies: 3
-
SOpera presents Early Bird mode in Opera One to test upcoming features
- Started by Santiago Benavides García
- Replies: 0
-
Hot Take Latest Windows Update Problems and How to Fix Them
- Started by lokamoka820
- Replies: 3
-
