What mode are you using on your Voodoo ?i don't know about that.This is only for Voodoo or for all softwares I recommend?
VS (and anti-exe) Discussion
- Thread starter DardiM
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
I don't us Voodoo.I have SecureAPlus xDWhat mode are you using on your Voodoo ?
But way you asking ?
Last edited:
L
Lucent Warrior
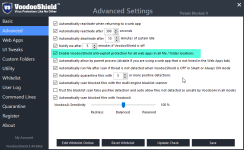
So what you are saying, is this setting here is null and void..VS won't protect against a browser exploit that abuses whitelisted Windows processes to bypass application whitelisting. A ransomware *.tmp will inherit whitelist status from the trusted Windows process run sequence and run unrestricted...
It's only a mistake, I though you were using VoodooShield, after one of your post, and was curious to see what mode you usedI don't us Voodoo.I have SecureAPlus xD
But way you asking ?
H
hjlbx
So what you are saying, is this setting here is null and void..
View attachment 117577
I have no idea what that setting does. Does anyone really know? All I know is that I watched the video on kafan.cn about 6 months ago and application whitelisting bypass was used after the IE exploit. I watched carefully and saw it with my own two eyes - and that's all the proof I need. NVT ERP, VS, SpyShelter, Bitdefender,... I can't remember them all... were bypassed. AppGuard was not bypassed in Protected Mode...
With that last sentence, the rest is history with me... 1 + 1 = 2
I will recommend you auto pilotIt's only a mistake, I though you were using VoodooShield, and was curious to see what mode you used
I have test and us all secure software
L
Lucent Warrior
Im sure the Developer doesI have no idea what that setting does. Does anyone really know?
It would be my understanding that it protects against exploits, how long this has been applied to the product im not sure, as i just started using it roughly over a month ago.
AppGuard was not bypassed in Protected Mode...
With that last sentence, the rest is history with me... 1 + 1 = 2
They have strengths and weaknesses, all products do. Appguard in protected mode, will let any signed application walk in, how far depends on what it does of course.
I know that i have hammered VS with tons of malicious website links, as well as samples placed strategically through out the system, and i have not bypassed it.
H
hjlbx
Im sure the Developer does
It would be my understanding that it protects against exploits, how long this has been applied to the product im not sure, as i just started using it roughly over a month ago.
They have strengths and weaknesses, all products do. Appguard in protected mode, will let any signed application walk in, how far depends on what it does of course.
I know that i have hammered VS with tons of malicious website links, as well as samples placed strategically through out the system, and i have not bypassed it.
I don't know what changes were made. I saw a tidbit when I dropped-in to take a "look-see" and I gathered that browsers are now hard-coded not to have any child processes - other than what is necessary to use the browser - when VS is ON. If that is the case, then issue should be solved.
You have to find an exploit page that is specifically followed by an application whitelist bypass attack.
Despite what others will say, I'm not bashing VS; actually I hope the issue has been fixed.
I bash AppGuard everyday - and bring, at least some folks, near to tears. I've been told I'm a scathing pain-in-the-ass. I take that as a compliment.
Can you fine video what you watch about bypassing NVT ERP, VS, SpyShelter, Bitdefender,... ?I have no idea what that setting does. Does anyone really know? All I know is that I watched the video on kafan.cn about 6 months ago and application whitelisting bypass was used after the IE exploit. I watched carefully and saw it with my own two eyes - and that's all the proof I need. NVT ERP, VS, SpyShelter, Bitdefender,... I can't remember them all... were bypassed. AppGuard was not bypassed in Protected Mode...
With that last sentence, the rest is history with me... 1 + 1 = 2
H
hjlbx
Can you fine video what you wach about bypassing NVT ERP, VS, SpyShelter, Bitdefender,... ?
Search for it on kafan.cn.
It is on ChineseSearch for it on kafan.cn.
H
hjlbx
It is on Chinese
Use Google translator browser plug-in (Chrome), navigate to kafan.cn, translate kafan.cn to English, then search for Voodooshield, NVT ERP, etc.
They use English names of softs in the threads.
It was a jokeUse Google translator browser plug-in (Chrome), navigate to kafan.cn, translate kafan.cn to English, then search for Voodooshield, NVT ERP, etc.
They use English names of softs in the threads.
H
hjlbx
It was a jokeNot good. But sorry I can fine video.I will love to fine and post on video reviews.
Watch out for bad links...
If you make regular Backups no you should not be worried about ransomware. 
Never got a ransomeware attack EVER. Haven't really used an adblocker and not really going to start. I shouldn't be worried about ransomeware but more inexperienced people should.
L
Lucent Warrior
It is a mistake to think that experience and knowledge will save your skin every time 100%, this is because nothing ever stays the same in cyber security, always evolving, meaning there is always more to learn, and sometimes the hard way.... Back ups are the solution, your fail safe, should anything ever happen.Never got a ransomeware attack EVER. Haven't really used an adblocker and not really going to start. I shouldn't be worried about ransomeware but more inexperienced people should.
It was with this sample, 5/53 at this moment ( and 40/54 now)It was a jokeNot good. But sorry I can fine video.I will love to fine and post on video reviews.
https://www.virustotal.com/en/file/...34f271da8432c338fa446d9c/analysis/1453695171/
H
hjlbx
I take this approach. I keep nothing on my system that I am not willing to lose. Data loss comes in all forms - hardware meltdowns, OS crashes, soft malfunctions, user mistakes, etc, etc.
Data loss due to malware (and more specifically ransomware) is only a tiny fraction of what and why data loss happens on a day-to-day basis in real-world IT...
Data loss due to malware (and more specifically ransomware) is only a tiny fraction of what and why data loss happens on a day-to-day basis in real-world IT...
H
hjlbx
It was with this sample, 5/53 at this moment ( and 40/54 now)
https://www.virustotal.com/en/file/...34f271da8432c338fa446d9c/analysis/1453695171/
The sample distributed wasn't static; the malc0der(s) distributed new, undetected variants every few hours...
You may also like...
-
-
Serious Discussion Do you use default-deny approach in your system?
- Started by RoboMan
- Replies: 24
-
Serious Discussion Firefox 145 and new Anti-fingerprint protections.
- Started by Sampei.Nihira
- Replies: 47
-
Poll The Trifecta Threat. Comodo vs. ESET vs. McAfee - Which Security Suite Wears the Crown?
- Started by Divergent
- Replies: 31