Serious Discussion WHHLight - simplified application control for Windows Home and Pro.
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
Would adding WHHLight to cyberlock provide more security?
Such a combo could be slightly stronger than CL or WHHLight alone. But, in my opinion, such a setup would be too complex.
A
Azazel
Would there be a problem if we applied WDAC-ISG Everywhere, even in SystemSpace, (all locations on the SYSTEM-drive that are Non-Writable) since all Microsoft signed files are allowed by default?
F
ForgottenSeer 107474
When you can enable core isolation, then all hardware related stuff will probably work (co-signed by Windows). Make sure you set system restore points and put a link of the WDAC folder on an easy accessible place (so you can remove the CIP easily when you might need to boot into safe mode) and have a image restore ate hand in case all goes wrong.Would there be a problem if we applied WDAC-ISG Everywhere, even in SystemSpace, (all locations on the SYSTEM-drive that are Non-Writable) since all Microsoft signed files are allowed by default?
I did it in steps, I first removed Windows, than Programs Files (assuming 64 bits programs are more recent) and as last the Program Files (x86) from the whitelist.
Last edited by a moderator:
A
Azazel
Whhlight blocks Userpace and allows SystemSpace.When you can enable core isolation, then all hardware related stuff will probably work (co-signed by Windows). Make sure you set system restore points and put a link of the WDAC folder on an easy accessible place (so you can remove the CIP easily when you might need to boot into safe mode) and have a image restore ate hand in case all goes wrong.
I did it in steps, I first removed Windows, than Programs Files (assuming 64 bits programs are more recent) and as last the Program Files (x86) from the whitelist.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
Would there be a problem if we applied WDAC-ISG Everywhere, even in SystemSpace, (all locations on the SYSTEM-drive that are Non-Writable) since all Microsoft signed files are allowed by default?
Yes, it could be a problem. There can be many executables (EXE, MSI, DLL, etc.) in SystemSpace that are not signed by Microsoft.
Here is the warning from Microsoft:
Warning
Binaries that are critical to boot the system must be allowed using explicit rules in your WDAC policy. Do not rely on the ISG to authorize these files.
The ISG option is not the recommended way to allow apps that are business critical. You should always authorize business critical apps using explicit allow rules or by installing them with a managed installer.
An advanced user could prepare a custom policy without whitelisting Non-Writable locations on the SYSTEM-drive, by adding some trusted signers and Publisher rules. This can be done on Windows Pro (via PowerShell or Microsoft's WDAC Wizadrd). But it would be too complicated and unnecessary at home.
Last edited:
A
Azazel
Supposed SRP is totally removed from windows in the future, can Applocker or WDAC replace it by blocking any custom file type as it is possible with SRP.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
No, Applocker and WDAC cannot do it.Supposed SRP is totally removed from windows in the future, can Applocker or WDAC replace it by blocking any custom file type as it is possible with SRP.
F
ForgottenSeer 107474
That is why I posted be careful. Until now everything works well. I am running a nearly vanilla software configuration (Windows11 home + Office2019 + Edge for PDF + Chrome for browsing + data backup + image backup + system cleaner and 1 user program on a HP laptop. In the last 4 ot 5 years I have only added 1 program (the system cleaner which was a giveaway on MT)Yes, it could be a problem. There can be many executables (EXE, MSI, DLL, etc.) in SystemSpace that are not signed by Microsoft.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
That is why I posted be careful. Until now everything works well. I am running a nearly vanilla software configuration (Windows11 home + Office2019 + Edge for PDF + Chrome for browsing + data backup + image backup + system cleaner and 1 user program on a HP laptop. In the last 4 ot 5 years I have only added 1 program (the system cleaner which was a giveaway on MT)
When the WDAC Whitelist is empty in WHHLight, the UserSpace is bigger but SystemSpace is still present. So, removing entries from the Whitelist will not impact the system. Only the processes and software that try to run something in Writable Locations can be blocked.
Applying Core Isolation settings can have a much bigger impact on the system, but Windows has built-in checks that prevent problematic settings.
F
ForgottenSeer 107474
Mhh, not sure I understand correctly (sounds like a wisdom from a Kung Fu movie)When the WDAC Whitelist is empty in WHHLight, the UserSpace is bigger
Last edited by a moderator:
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
Mhh, not sure I understand correctly (sounds like a wisdom from a Kung Fu movie)
Yes. I should not use the term UserSpace but the part of it restricted by ISG.
In WHHLight, ISG can block only UserSpace locations. If the WDAC Whitelist is empty, the ISG can restrict the whole UserSpace.
A few locations in the Windows and Program Files folders can belong to UserSpace, but most of them belong to SystemSpace.
The Non-Writable locations on the SYSTEM-drive (SystemSpace) are always allowed in WHHLight, independently on the WDAC Whitelist. I did it to avoid problems with executables located in Windows and Program Files folders. The only exceptions are blocked LOLBins (recommended by Microsoft).
Post edited.
Last edited:
F
ForgottenSeer 107474
Thanks for your explanation. What nice (and smart) of you to take measures to prevent us shooting in the footYes. I should not use the term UserSpace but the part of it restricted by ISG.
In WHHLight, ISG can block only UserSpace locations. If the WDAC Whitelist is empty, the ISG can restrict the whole UserSpace.
A few locations in the Windows and Program Files folders can belong to UserSpace, but most of them belong to SystemSpace.
The Non-Writable locations on the SYSTEM-drive (SystemSpace) are always allowed in WHHLight, independently on the WDAC Whitelist. I did it to avoid problems with executables located in Windows and Program Files folders. The only exceptions are blocked LOLBins (recommended by Microsoft).
Post edited.
That is what I really appreciate about your utilities. Not only do they make available PRO functionality in an EASIER way, but also automatically implement rules to CLOSE the loopholes Microsoft left in their original design of those pro functionalities. So we also get (a part) of your knowledge and best practices with those utilities.
Examples which I know (but their maybe more):
1. ACL/UAC (user write) holes in System space are closed by WDAC-ISG and SRP-SWH
2. LNK execution bypass loophole is closed by SRP-SWH
3. Additional block rules for email clients and archivers in SWH-SRP to prevent unwanted execution of software
4. The way WDAC-ISG and SRP-SWH work together in user space (SRP-SWH allowing executables but blocking risky file extension, WDAC-ISG allowing only known good to execute)
5. Configure_Defender whitelisting stuff before enabling advanced ASR (also to prevent unwanted blocks)
The more I understand your work, the more I am impressed by the brilliance of it, thank you
(a more than happy WHHL-user applauding your contribution to our digital security
Last edited by a moderator:
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
When is WHHFull release date?
Still a concept. I do not have a clear view of the final product.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
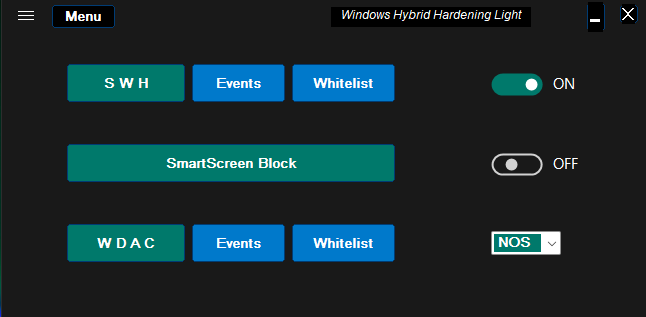
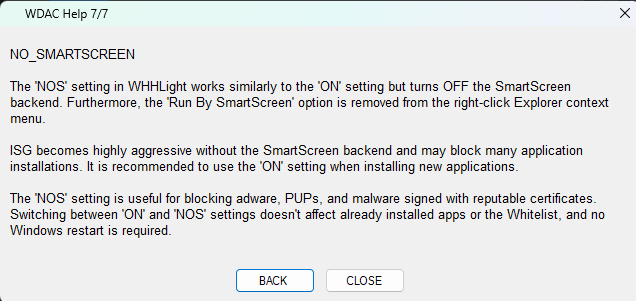
I plan to add the new WDAC setting (in addition to ON and OFF settings):
I recently noticed in Event viewer windows logs (security tab) that since installing WHHL I have audit failure appear with the following info :
The Windows Filtering Platform has blocked a connection.
ProcessID 8908
Application \device\harddiskvolume3\windows\system32\svchost.exe
Direction %%14592
SourceAddress 192.168.0.10
SourcePort 1901
DestAddress 239.255.255.250
DestPort 1900
Protocol 17
InterfaceIndex 10
FilterOrigin Query User Default
FilterRTID 82832
LayerName %%14610
LayerRTID 44
RemoteUserID S-1-0-0
RemoteMachineID S-1-0-0
OriginalProfile %%14644
CurrentProfile %%14644
IsLoopback %%1826
HasRemoteDynamicKeywordAddress %%1826
No blocks listed under FH, SWH or WDAC
Should this be happening ?
Thanks in advance for any help.
The Windows Filtering Platform has blocked a connection.
ProcessID 8908
Application \device\harddiskvolume3\windows\system32\svchost.exe
Direction %%14592
SourceAddress 192.168.0.10
SourcePort 1901
DestAddress 239.255.255.250
DestPort 1900
Protocol 17
InterfaceIndex 10
FilterOrigin Query User Default
FilterRTID 82832
LayerName %%14610
LayerRTID 44
RemoteUserID S-1-0-0
RemoteMachineID S-1-0-0
OriginalProfile %%14644
CurrentProfile %%14644
IsLoopback %%1826
HasRemoteDynamicKeywordAddress %%1826
No blocks listed under FH, SWH or WDAC
Should this be happening ?
Thanks in advance for any help.
- Apr 5, 2021
- 624
It is UPnP protocol. Probably nothing you need unless you are a gamer, in which case it might make things easier for you to connect your console for online gaming. But the flip side of it is it can be a security issue. More info on it here:

 nordvpn.com
nordvpn.com
 forums.tomshardware.com
forums.tomshardware.com
What is UPnP?
UPnP might be convenient but it carries many security risks. Read this blog post to find out what UPnP is, what it's used for, and why you should disable it.
[SOLVED] - Should UPnP be enabled or off?
I game alot and stream so wondering if i need it on?
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
I recently noticed in Event viewer windows logs (security tab) that since installing WHHL I have audit failure appear with the following info :
The Windows Filtering Platform has blocked a connection.
ProcessID 8908
Application \device\harddiskvolume3\windows\system32\svchost.exe
Direction %%14592
SourceAddress 192.168.0.10
SourcePort 1901
DestAddress 239.255.255.250
DestPort 1900
Protocol 17
InterfaceIndex 10
FilterOrigin Query User Default
FilterRTID 82832
LayerName %%14610
LayerRTID 44
RemoteUserID S-1-0-0
RemoteMachineID S-1-0-0
OriginalProfile %%14644
CurrentProfile %%14644
IsLoopback %%1826
HasRemoteDynamicKeywordAddress %%1826
No blocks listed under FH, SWH or WDAC
Should this be happening ?
Thanks in advance for any help.
This event is related to the blocked Inbound connection ( Direction %%14592 ).
Is that kind of block present after switching OFF the WHHLight controls (SWH and WDAC)?
Yes it is. EDIT : Although the issue was not present before installing WHHL and Firewall HardeningThis event is related to the blocked Inbound connection ( Direction %%14592 ).
Is that kind of block present after switching OFF the WHHLight controls (SWH and WDAC)?
The solution by @wat0114 appears to resolve the issue but I had only just configured the solution before reverting back to check if the problem still existed when SWH & WDAC were switched off
Last edited:
Similar threads
- Replies
- 253
- Views
- 38,225
- Replies
- 18
- Views
- 1,495
- Replies
- 24
- Views
- 1,327

