- Sep 22, 2014
- 1,767
Thanks.
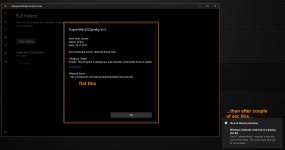
If I correctly read your attachment, then the scripts (RunNotepad.vbs, RunPowerShell.vbs)successfully ran the executables (notepad.exe, powershell.exe), and next, Defender recognized the RunPowerSell.vbs script as dangerous and put it in Quarantine.
If so, then indeed, the executables that are already on the disk are not blocked by this ASR rule (D3E037E1-3EB8-44C8-A917-57927947596D). Your malware test suggests, that the rule is activated when the script can download executable to the disk and tries to execute it. That is a good news.
Anyway, your Defender settings are somewhat more aggressive, because I can run the same script with no Defender intervention.
Could you post the Defender details about the quarantined script (or details from Windows Event Viewer)?
This would help to ensure everyone, that ASR rules have nothing to do with detecting the RunPowerSell.vbs script.
I can't find anything in WD accept I already post it in last msg.
In Event Viewer also can't find nothing, maybe you can tell me where to look?