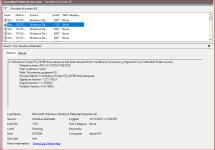
5
509322
What home user is going to genuinely need features like VBScript or local JScript? I cannot think of a single one. I think it is simpler for it to just be disabled and be done with it than relying on ASR which is going to be a risky game of hit'n'miss each time.
It is awesome that Microsoft is adding protections. However, we all know how it goes... it is fiendishly complex, hidden, with little to no documentation. And it takes a lot of effort to figure it out. I can count in excess of 20 pages of ASR discussion spread across multiple threads and PMs. And in an instant parts of it can be undone with the next Windows Update and y'all can sort it out all over again.
I am simple stupid. So if people are like me, then they appreciate simple - stuff that they can master easily (they don't have to necessarily understand it). People are much more apt to use ON\OFF and not use "Deep Dive" security. A user can understand ON blocks and OFF allows. ON blocks all the "user wants to use stuff" stuff and OFF let's them do it. Gee... hey now... we're gettin' really good at this... Voila ! Will you look at that... a user is using something because they "get it," it works, and they didn't have to take a college semester class to just begin to figure it out.