Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
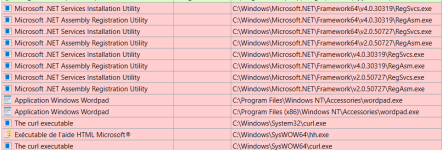
The SysHardener and FirewallHardening rules are similar. The FirewallHardening Blocklist has got some additional important rules, like blocking curl.exe. There are some advantages over SysHardener:I use SysHardener outbound firewall rules. Are they about the same as Recommended H_C rules? Maybe I'm missing something? SysHardener added 71 rules to my firewall. SH is not on my PC anymore, but I kept its rules.
- A few additional rules.
- Log of all blocked outbound connections. This log shows the blocked entries from the FirewallHardening Blocklist + entries blocked by other rules made in Windows Firewall by other applications (also SysHardener).
- The user can add custom rules to the FirewallHardening Blocklist.