Ah, you are not talking about LOL bins, you are talking about malicious dlls downloaded with a false extension, and FIDES will not even know it is a dll. That makes sense.SRP and Bouncer can be used as a default deny because they can differ between a DLL with changed extension (for example, malware.dat) from non-executable file with the same name and extension (malware.dat). FIDES cannot do it. It would be hardly possible (or maybe with much effort) to use FIDES as default-deny in UserSpace.
Hard_Configurator - Windows Hardening Configurator
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
The new icon for Run as SmartScreen actually helps for this issue. The bright green color catches my eye and pulls me away from the more boring Run as Administrator. The more that icon stands out, the better it is, as far as I am concerned.I would not recommend this. Both options "Run As SmartScreen" and "Run as administrator" can be easily confused, and then you will run the unsafe file via "Run as administrator" without SmartScreen check.
@Andy Ful
Two questions:
Two questions:
- Unless I am overlooking something, but I can't find FSC.exe in the list of SPONSORS (it is the F-sharp compiler, when you block C-sharp you might as well block this also).
- With the allow EXE and TMP option, why not use cloud feature as white list?
The C# compiler is installed with .NET Framework, so it is a part of the Windows system. The F# compiler has to be installed by the user as the external programming language, usually as a part of Visual Studio. It seems that blocking F# would not be welcome.
The whitelisting option 'Allow EXE and TMP' was initially prepared for Avast Hardened Mode Aggressive as a kind of default-deny setup.
This option can be used with any executable reputation service, and also with WD Cloud Protection Level set to Block + ASR rule:
"Block executable files from running unless they meet a prevalence, age, or trusted list criteria".
The whitelisting option 'Allow EXE and TMP' was initially prepared for Avast Hardened Mode Aggressive as a kind of default-deny setup.
This option can be used with any executable reputation service, and also with WD Cloud Protection Level set to Block + ASR rule:
"Block executable files from running unless they meet a prevalence, age, or trusted list criteria".
Last edited:
@Andy Ful
Some additional feature requests for Hard_Configurator
a) Disable CMD and Scripts
b) Align HighRiskFileTypes (for mail & attachments) with the Designed File Types of SRP.
c) Disable remote access and shared desktop
Some additional feature requests for Hard_Configurator
a) Disable CMD and Scripts
b) Align HighRiskFileTypes (for mail & attachments) with the Designed File Types of SRP.
c) Disable remote access and shared desktop
You can already disable CMD and Scripts in H_C.@Andy Ful
Some additional feature requests for Hard_Configurator
a) Disable CMD and Scripts
b) Align HighRiskFileTypes (for mail & attachments) with the Designed File Types of SRP.
c) Disable remote access and shared desktop
H_C blocks by default Remote Desktop (remote access), Remote Registry, and Remote Shell.
Windows Desktop Sharing (for Vista and higher versions) is a part of Remote Desktop.
Remote Desktop Services - Wikipedia
For now, those HighRiskFileTypes are included in RunBySmartScreen. Most of them are related to MS Office, and they are protected by Documents Anti-Exploit in H_C or Switch Default Deny tool. But anyway, I could add the 'Paranoid' set of extensions to <Designated File Types> in H_C.
Last edited:
Hello! I have good habits of use on the web and a average knowledge. I've never been infected. I have tested malware in MH before, but I do not have any technical knowledge like you. Although I love technology, computing and security, my area is health.
I use CF (proactive defense), just to use the sandbox in Chrome a few times to access some sites, I practically do not make payments / transactions over the computer. I leave the WD disabled, only CF using 19mb of memory.
What do you recommend me? Just continue with CF? CF + HC or only HC?
Do I have a benefit with one I would not have with another?
Thank you all for the teachings you bring on this topic. :emoji_clap::emoji_clap:
I use CF (proactive defense), just to use the sandbox in Chrome a few times to access some sites, I practically do not make payments / transactions over the computer. I leave the WD disabled, only CF using 19mb of memory.
What do you recommend me? Just continue with CF? CF + HC or only HC?
Do I have a benefit with one I would not have with another?
Thank you all for the teachings you bring on this topic. :emoji_clap::emoji_clap:
The problem with people who never were infected is similar to people who never were victims of a traffic accident. You cannot be sure if this is due to safe habits or luck.Hello! I have good habits of use on the web and a average knowledge. I've never been infected. I have tested malware in MH before, but I do not have any technical knowledge like you. Although I love technology, computing and security, my area is health.
I use CF (proactive defense), just to use the sandbox in Chrome a few times to access some sites, I practically do not make payments / transactions over the computer. I leave the WD disabled, only CF using 19mb of memory.
What do you recommend me? Just continue with CF? CF + HC or only HC?
Do I have a benefit with one I would not have with another?
Thank you all for the teachings you bring on this topic. :emoji_clap::emoji_clap:
The second example can be house contents insurance. You could ask, should I pay such insurance If I never had an occasion to use it? I do not know.... There are many people who probably first die, and will never benefit from such insurance.
I think that users who know what vectors of attack are not covered by such a setup (only CF proactive), and are cautious enough, might use it without a problem. They are not 100% safe, but there are many other, more dangerous things that can happen.
Anyway, such a setup is not recommended for average users.
Last edited:
Try enabling Windows Defender, and see if it bothers you. It has improved a lot. If it still bothers you, disable it again. You lose nothing by trying.Hello! I have good habits of use on the web and a average knowledge. I've never been infected. I have tested malware in MH before, but I do not have any technical knowledge like you. Although I love technology, computing and security, my area is health.
I use CF (proactive defense), just to use the sandbox in Chrome a few times to access some sites, I practically do not make payments / transactions over the computer. I leave the WD disabled, only CF using 19mb of memory.
What do you recommend me? Just continue with CF? CF + HC or only HC?
Do I have a benefit with one I would not have with another?
Thank you all for the teachings you bring on this topic. :emoji_clap::emoji_clap:
From time to time I work on the new icons (the last two are new to compare with the first one):
I tried to use half-spheres (for the new icons) to mimic the letters C and D.
I tried to use half-spheres (for the new icons) to mimic the letters C and D.
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
They are beautiful, but I'm still more into the square ones like the one for Configure Defender below:From time to time I work on the new icons (the last two are new to compare with the first one):
View attachment 214144
I tried to use half-spheres (for the new icons) to mimic the letters C and D.
It can be also a square like:


The problem is: should it be beautiful and fancy or rather simple and straight.
The problem is: should it be beautiful and fancy or rather simple and straight.
Last edited:
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
I prefer simple and straight. Don't know what others prefer...It can be also a square like:
View attachment 214147
View attachment 214149
The problem is: should it be beautiful and fancy or rather simple and straight.
My feeling as well.They are beautiful, but I'm still more into the square ones like the one for Configure Defender below:

I published the Firewall Hardening tool on GitHub:
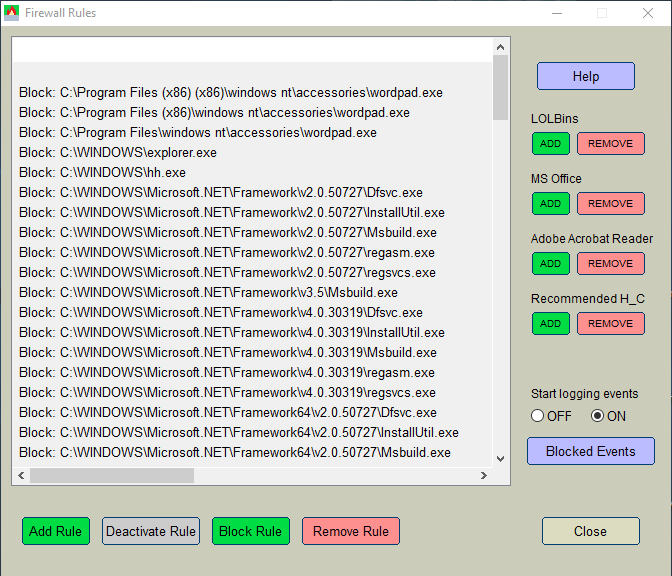
It works, but I did not included the Help text, so please ask if something is not clear. The questions will help me to write the final Help text.
Edit.
The new firewall rules work after restarting Windows.
- for Windows 64-bit: AndyFul/Hard_Configurator
- for Windows 32-bit: AndyFul/Hard_Configurator
- Block (predefined) LOLBins which use outbound Internet connections in attacks.
- Block outbound Internet connections of MS Office applications and Adobe Acrobat Reader.
- Block the outbound Internet connection of any application chosen by the user.
- Turn ON logging of blocking events.
- Display blocked events.
It works, but I did not included the Help text, so please ask if something is not clear. The questions will help me to write the final Help text.
Edit.
The new firewall rules work after restarting Windows.
Last edited:
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
We could/should use this tool next to Hard Configurator?I published the Firewall Hardening tool on GitHub:
What it can do:
- for Windows 64-bit: AndyFul/Hard_Configurator
- for Windows 32-bit: AndyFul/Hard_Configurator
View attachment 214157
- Block (predefined) LOLBins which use outbound Internet connections in attacks.
- Block outbound Internet connections of MS Office applications and Adobe Acrobat Reader.
- Block the outbound Internet connection of any application chosen by the user.
- Turn ON logging of blocking events.
- Display blocked events.
It works, but I did not included the Help text, so please ask if something is not clear. The questions will help me to write the final Help text.
It would be a part of Hard_Configurator. The option <Recommended H_C> is prepared for the usual H_C recommended settings. The LOLBins option can block all SysHardener entries and some other important LOLBins which can run the code from the remote locations.We could/should use this tool next to Hard Configurator?
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Okay thanks. Added LOLBins, MS Office and Recommended.It would be a part of Hard_Configurator. The option <Recommended H_C> is prepared for the usual H_C recommended settings. The LOLBins option can block all SysHardener entries and some other important LOLBins which can run the code from the remote locations.
In blocked events I see Kaspersky Free Antivirus:
Code:
Local Time: 2019/05/25 18:50:21
ProcessId: 4640
Application: C:\program files (x86)\kaspersky lab\kaspersky free 19.0.0\avp.exe
Direction: Outbound
SourceAddress: 192.168.178.171
SourcePort: 49750
DestAddress: 88.221.144.67
DestPort: 80
Protocol: 6
FilterRTID: 68333
LayerName: %%14611
LayerRTID: 48It is not blocked by my tool. You have to look at your firewall settings or Kaspersky settings.Okay thanks. Added LOLBins, MS Office and Recommended.
In blocked events I see Kaspersky Free Antivirus:
How to unblock/allow Kaspersky?Code:Local Time: 2019/05/25 18:50:21 ProcessId: 4640 Application: C:\program files (x86)\kaspersky lab\kaspersky free 19.0.0\avp.exe Direction: Outbound SourceAddress: 192.168.178.171 SourcePort: 49750 DestAddress: 88.221.144.67 DestPort: 80 Protocol: 6 FilterRTID: 68333 LayerName: %%14611 LayerRTID: 48
This address belongs to Akamai International B.V. in Italy....
DestAddress: 88.221.144.67
...
Gandalf_The_Grey
Level 85
Verified
Honorary Member
Top Poster
Content Creator
Well-known
Forum Veteran
Why then did it show up in the log when I pressed Blocked Events? That's not only for your tool?It is not blocked by my tool. You have to look at your firewall settings or Kaspersky settings.
You may also like...
-
Scams & Phishing News Multi-Stage Phishing Campaign Targets Russia with Amnesia RAT and Ransomware
- Started by Parkinsond
- Replies: 22
-
New Update Windows 11 Patch Tuesday December 2025 (KB5072033, KB5071417)
- Started by silversurfer
- Replies: 11
-
-
Malware News New Multi-Stage Windows Malware Disables Microsoft Defender Before Dropping Malicious Payloads
- Started by Brownie2019
- Replies: 4