Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
The TROUBLESHOOTING manual section has been updated. It contains info how to use Autoruns, Windows Event Log, and SRP logging to identify problems with running programs. That info may be useful for anyone, so I put it in this post.
TROUBLESHOOTING
Please read this paragraph carefully, because it can be helpful when in trouble, after installing any security software.
Hard_Configurator troubleshooting.
Using Sysinternals Autoruns.
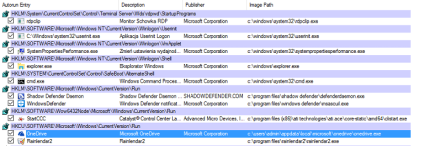
Some processes can be loaded at the boot time from the User Space (= outside ‘Windows’, ‘Program Files’, ‘Program Files (x86)’ ). They should be whitelisted by path in SRP to load properly. Autoruns allows to find the paths of those processes. It is very useful because stopping something important from loading at the boot time may hang the system (see the picture attached to this post).
We can see that OneDrive is starting from the User Space at the boot time.
SRP Event Log.
When an SRP rule is applied, it can be seen in the application event log. The event ID between 865 and 868 shows the details of the process that triggered the SRP rule. It is good to look at it to see if the SRP restrictions block something important. The information about events are very short, but sufficient in most cases to identify the problem.
There is also a nice NirSoft tool FullEventLogView, that can be used for quick event checking.
Verbose trace logging of SRP.
If someone would like enhanced logging of running processes, then the following registry setting must be added:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\safer\CodeIdentifiers]
"LogFileName"="c:\\Windows\\Hard_Configurator\\SRP_events.log"
LogFileName is a REG_SZ type. SRP will put more info about running processes to the file ‘SRP_events.log’. This can be used to identify the problems with blocked application, too. Simply, run the blocked application with "Run As Administrator" or "Run As SmartScreen", and then look at the last entry in the log.
For example, when ‘dllexplorer_setup.exe’ is run with "Run As SmartScreen", then the entries in the log will look like:
"RunAsSmartscreen(x64).exe (PID = 2100) identified C:\Windows\Hard_Configurator\dllexplorer_setup.exe as Unrestricted using default rule, Guid = {11015445-d282-4f86-96a2-9e485f593302}
dllexplorer_setup.exe (PID = 5236) identified C:\Users\Admin\AppData\Local\Temp\is-PPQV9.tmp\dllexplorer_setup.tmp as Unrestricted using default rule, Guid = {11015445-d282-4f86-96a2-9e485f593302}"
So, we know that dllexplorer_setup.exe is using dllexplorer_setup.tmp to execute in temporary folder ‘C:\Users\USERNAME\AppData\Local\Temp\is-ASDAD.tmp\’.
Now, dllexplorer_setup.tmp can be whitelisted, and the problem is solved.
TROUBLESHOOTING
Please read this paragraph carefully, because it can be helpful when in trouble, after installing any security software.
- Check if you have operational bootable media to access a Command Prompt, in the case when the system hangs or is unbootable.
- Some computers can have problems with a bootable media or recovery partition after upgrading the system (especially to Windows 10).
- Before installing any security program, make the system restore point.
- Sometimes system becomes unbootable from another cause. It is recommended to unplug all external devices (pendrives, USB disks, printers, headphones, USB DVD, etc.) and restart the system.
- Having a bootable media, gives you access to Command Prompt. And then, using Regedit or Sysinternals Autoruns, the Registry can be loaded for offline editing. From Autoruns you can disable some autostart entries that may cause problems.
Hard_Configurator troubleshooting.
- If the system hangs after reboot, then it can be a sign, that SRP or one of program restrictions has blocked something important from loading at the boot time.
- The simplest method to solve this problem is using one of system restore points.
- Another solution is using bootable media to access a Command Prompt, and then editing the Registry offline. In most cases the problem would be with SRP, so one must edit the key:
HKLM\SOFTWARE\Policies\Microsoft\Windows\Safer\CodeIdentifiers DefaultLevel change hexagonal value to 40000 - If the above did not help, then it is possible to edit or remove any registry changes made by Hard_Configurator. The Registry keys altered by the program are enumerated in this manual at the end of each paragraph.
Using Sysinternals Autoruns.
Some processes can be loaded at the boot time from the User Space (= outside ‘Windows’, ‘Program Files’, ‘Program Files (x86)’ ). They should be whitelisted by path in SRP to load properly. Autoruns allows to find the paths of those processes. It is very useful because stopping something important from loading at the boot time may hang the system (see the picture attached to this post).
We can see that OneDrive is starting from the User Space at the boot time.
SRP Event Log.
When an SRP rule is applied, it can be seen in the application event log. The event ID between 865 and 868 shows the details of the process that triggered the SRP rule. It is good to look at it to see if the SRP restrictions block something important. The information about events are very short, but sufficient in most cases to identify the problem.
There is also a nice NirSoft tool FullEventLogView, that can be used for quick event checking.
Verbose trace logging of SRP.
If someone would like enhanced logging of running processes, then the following registry setting must be added:
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\safer\CodeIdentifiers]
"LogFileName"="c:\\Windows\\Hard_Configurator\\SRP_events.log"
LogFileName is a REG_SZ type. SRP will put more info about running processes to the file ‘SRP_events.log’. This can be used to identify the problems with blocked application, too. Simply, run the blocked application with "Run As Administrator" or "Run As SmartScreen", and then look at the last entry in the log.
For example, when ‘dllexplorer_setup.exe’ is run with "Run As SmartScreen", then the entries in the log will look like:
"RunAsSmartscreen(x64).exe (PID = 2100) identified C:\Windows\Hard_Configurator\dllexplorer_setup.exe as Unrestricted using default rule, Guid = {11015445-d282-4f86-96a2-9e485f593302}
dllexplorer_setup.exe (PID = 5236) identified C:\Users\Admin\AppData\Local\Temp\is-PPQV9.tmp\dllexplorer_setup.tmp as Unrestricted using default rule, Guid = {11015445-d282-4f86-96a2-9e485f593302}"
So, we know that dllexplorer_setup.exe is using dllexplorer_setup.tmp to execute in temporary folder ‘C:\Users\USERNAME\AppData\Local\Temp\is-ASDAD.tmp\’.
Now, dllexplorer_setup.tmp can be whitelisted, and the problem is solved.
Attachments
Last edited: