Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
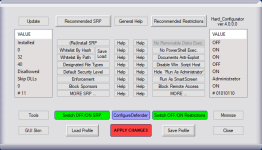
It is worth to know, that pressing the green button <Switch OFF/ON SRP> changes SRP 'Default Security Level' to Unrestricted, and this works even without using <APPLY CHANGES> button. This should allow most updates in the User Space without refreshing the Explorer. Refreshing the Explorer is required to turn OFF other SRP features like: <Block Sponsors>, <Protect Windows Folder>, and <Protect Shortcuts> which usually is not required when updating applications in the User Space.
Last edited: