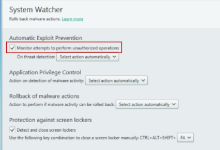
Automatic Exploit Prevention: technology protects your computer from malicious programs that use vulnerabilities in the most commonly used applications.
- Control of executable files started from vulnerable applications and web browsers (for example, when a program designed for viewing documents tries to run an executable file).
- Control of suspicious actions performed by vulnerable applications (for example, if the rights of a running vulnerable application are enhanced and it writes itself into the other processes' system memory).
- Monitoring of previous program starts (for example, whether the program was started by the user or by an exploit).
- Tracking of sources of malicious code (for example, a web browser that started download of an infected file; remote web address).
- Preventing malware from using application vulnerabilities.
Kaspersky Anti-Virus 2015 tracks executable files run by vulnerable applications.
If Kaspersky
Anti-Virus 2015 detects an attempt to run an executable file from a vulnerable application that has not been initiated by the user, the application blocks this attempt (the user can select a different action to be performed upon threat detection).
Information about blocked executable files is logged in the Exploit Prevention report.
To ensure maximum protection, the
lists of applications with detected vulnerabilities are updated together with
Kaspersky Anti-Virus 2015 antivirus databases.