SWH vs. Magniber JavaScript variant
https://malwaretips.com/threads/mag...ers-via-javascript-files.117780/#post-1007487
https://threatresearch.ext.hp.com/m...geting-home-users-with-fake-software-updates/
Like in the previous Magniber campaign (CPL file), this one is easily blocked by SWH. But, the rest will depend on the user, because Magniber is often promoted as the system (software) update/upgrade, so many users can be fooled to turn off the protection. This is probable especially when they are looking for pirated content.
https://malwaretips.com/threads/mag...ers-via-javascript-files.117780/#post-1007487
https://threatresearch.ext.hp.com/m...geting-home-users-with-fake-software-updates/
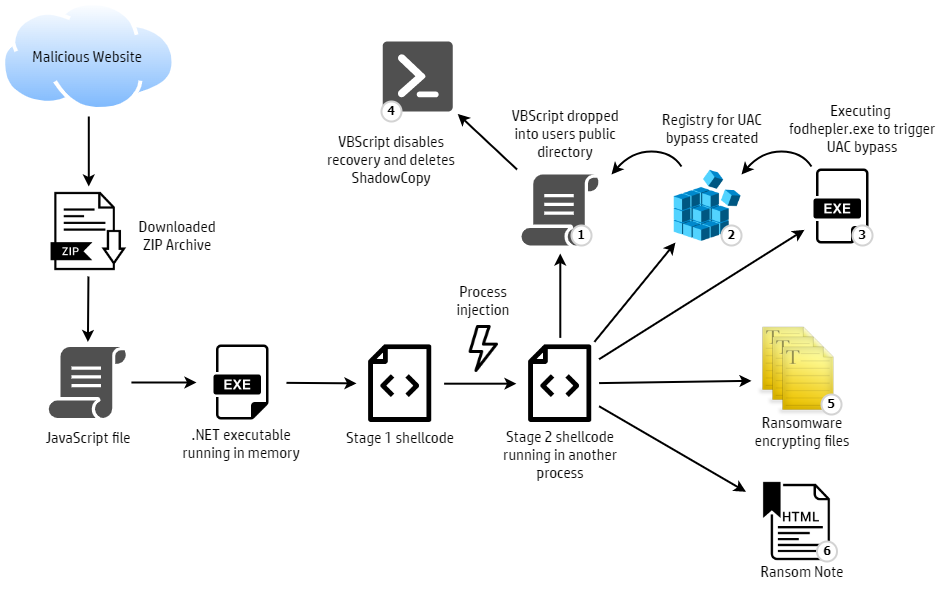
Previously Magniber was primarily spread through MSI and EXE files, but in September 2022 we started seeing campaigns distributing the ransomware in JavaScript files.
The JavaScript files use a variation of the DotNetToJScript technique, enabling the attacker to load a .NET executable in memory, meaning the ransomware does not need to be saved to disk. This technique bypasses detection and prevention tools that monitor files written to disk and reduces artifacts left on an infected system. The .NET code decodes shellcode and injects it into another process. The ransomware code runs from this process – first deleting shadow copy files and disabling Windows’ backup and recovery features, before encrypting the victim’s files (Figure 2).
Figure 2 – Magniber infection chain
Interestingly, the Magniber sample we analyzed in September support different versions of Windows 11, including pre-release versions. This suggests that home users rather than enterprises were the intended targets of the campaign, since enterprises tend to use older operating systems.
Like in the previous Magniber campaign (CPL file), this one is easily blocked by SWH. But, the rest will depend on the user, because Magniber is often promoted as the system (software) update/upgrade, so many users can be fooled to turn off the protection. This is probable especially when they are looking for pirated content.


