WHHLight vs. LODEINFO (spear-phishing attacks)
https://malwaretips.com/threads/lod...s-and-remote-code-tricks.128638/#post-1073323
DOWNIISSA shellcode:
https://securelist.com/apt10-tracking-down-lodeinfo-2022-part-i/107742/
According to information released by security vendors, APT campaigns using LODEINFO target Japanese media, diplomacy, public institutions, defense industries, and think tanks. It is also suggested that the infamous APT group called APT10 is involved given the similarities in their methods and malwares.
This is not a typical attack against home users, but I used it to show how the WHHLight package can help prevent/mitigate some interesting attack vectors.
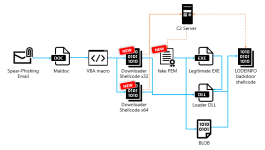
Attack flow:
The attack can be stopped/mitigated by the WHHLight package on several infection stages.
The recommended way is based on hardening MS Office applications.
This can be done manually or by using the DocumentsAntiExploit tool (included in the package).
When using that tool, the VBA code is blocked and the user cannot allow it from the configuration panel of MS Office applications. The attack is prevented at the early infection stage.
In the case of allowed macros, the attack can be prevented by the FirewallHardening settings when blocking outbound connections of MS Office applications.
In this particular case, the macro injects the shellcode into the running Word process (WINWORD.exe). Next, the shellcode uses the URLDownloadToFileA() API function to download the payloads. The download will fail when outbound connections of Word are blocked.
If the shellcode is not mitigated, it decrypts the payload, drops three files in the user Temp folder, and executes one of them (as a child process of WINWORD.exe) to apply DLL Hijacking. This can be blocked if the user applies ConfigureDefender with a HIGH Protection Level (ASR rule blocks the child process).
If the user does not use DocumentsAntiExploit, FireWallHardening, or ConfigureDefender then WHHLight should be configured with
SUPER_SAFE or
TWO_ACCOUNTS setup. If so, then the DLL Hijacking can be blocked by WDAC.