Serious Discussion WHHLight - simplified application control for Windows Home and Pro.
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
If I download an Exe, and Smartscreen appears as unrecognized file. And I click run anyway, it will bypass Wdac. Is this a normal behavior?
You have to unblock the file in the properties to get it to run.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
If I download an Exe, and Smartscreen appears as unrecognized file. And I click run anyway, it will bypass Wdac. Is this a normal behavior?
Yes, this can happen for some files.
In some cases the opposite can happen - the file allowed by SmartScreen is blocked by WDAC ISG.
But in most cases, WDAC ISG blocks the file if that file was blocked by SmartScreen and allows the file if it was allowed by SmartScreen.
Last edited:
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
Scripts and many more file types are already blocked by < SWH > settings. These files can be selectively whitelisted in WHHLight (except PowerShell scripts). This is far better protection compared to SAC.Much like SAC can you add wdac policy that blocks scripts that have the mark of the web?
- Apr 5, 2021
- 622
Using Win 11 21H2, my network connection partially crippled shortly after enabling "Block sponsors" in H_C, although I couldn't find any evidence in Events that H_C caused it, and neither did restoring Windows defaults fix it, nor even uninstalling H_C, with several reboots in between. Eventually I did a Network reset to fix it. Oh well, I decided to go back to WHHLight, customizing the WDAC whitelist paths, enabling most of the Firewall Blocklist rules, and setting CF to "High". Everything is working harmoniously again, and I even uninstalled OSArmor because I'm convinced - with a bit of influence from other members in this forum - it's not needed with WHHLight set up the way I have it. Very nice work you've done on this project @Andy Ful 
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
Using Win 11 21H2, my network connection partially crippled shortly after enabling "Block sponsors" in H_C, although I couldn't find any evidence in Events that H_C caused it, and neither did restoring Windows defaults fix it, nor even uninstalling H_C, with several reboots in between.
It was most probably a time coincidence, unrelated to H_C. You can find several examples of such coincidences in this thread, that finally turned out completely unrelated.
But one cannot be sure without a thorough event inspection.
If the issue disappears after restoring Windows default settings (including ConfigureDefender and FirewallHardening) and restarting the system, then you should consider H_C to be involved. In such a case the connection could be impacted by the FirewallHardening or some blocked Sponsors. There should also be blocked events in the H_C or FirewallHardening logs.
Be safe.
Please let me know if you encounter any problems with WHHLight.
Last edited:
- Apr 5, 2021
- 622
You are most likely rightIt was most probably a time coincidence, unrelated to H_C. You can find several examples of such coincidences in this thread, that finally turned out completely unrelated.

Issue still persisted after all those steps, and there was no evidence of Firewall blocks or blocked Sponsors found in any of the Event logs. Only after doing a "Network reset" did the issue disappear, which is why I think it was not caused by H_C or CFIf the issue disappears after restoring Windows default settings (including ConfigureDefender and FirewallHardening) and restarting the system, then you should consider H_C to be involved. In such a case the connection could be impacted by the FirewallHardening or some blocked Sponsors.
Thanks, will do. Actually the more compelling reasons for me switching to WHHLight is I embrace the simplicity of it, while being highly effective, and that it's a current project of yours in active developmentBe safe.
Please let me know if you encounter any problems with WHHLight.

@Andy Ful
When doing a Google search on "Andy Ful" one comes to the following site: AndyFul - Overview. It is the Top alternative. It is like a home site for your products since they are all there, except 1 - WHHLight. So my suggestion is that you add that software to that site to make your portfolio complete on mentioned site. Which, more or less, would make it to a home site. I often recommend people your software and it would be nice if they all would be on the same place. I think others, here and otherwise, that suggest them think the same also.
When all is in 1 place there also is need for a site like gHacks.net, for example, to do a "Review" of the programs and your Github site, a review that shows on Google when searching for reviews. In that way it and they get more valid and legitimate. Now it is more spread and sadly enough there is very few reviews of these excellent little programs that means so much for Windows seurity. So when the mentioned above is done my intention is to get in contact with gHacks to get them/him to do a review article, even if it costs.
What do you say, does not these 2 actions seems good, make sence?
Now your site and the programs are known to just a small group of users, and mostly discussed here on MT and little else. With the above actions the spreed will be a bit better and it will be easier for my followers on the site i recommend the programs to get a better overview
When doing a Google search on "Andy Ful" one comes to the following site: AndyFul - Overview. It is the Top alternative. It is like a home site for your products since they are all there, except 1 - WHHLight. So my suggestion is that you add that software to that site to make your portfolio complete on mentioned site. Which, more or less, would make it to a home site. I often recommend people your software and it would be nice if they all would be on the same place. I think others, here and otherwise, that suggest them think the same also.
When all is in 1 place there also is need for a site like gHacks.net, for example, to do a "Review" of the programs and your Github site, a review that shows on Google when searching for reviews. In that way it and they get more valid and legitimate. Now it is more spread and sadly enough there is very few reviews of these excellent little programs that means so much for Windows seurity. So when the mentioned above is done my intention is to get in contact with gHacks to get them/him to do a review article, even if it costs.
What do you say, does not these 2 actions seems good, make sence?
Now your site and the programs are known to just a small group of users, and mostly discussed here on MT and little else. With the above actions the spreed will be a bit better and it will be easier for my followers on the site i recommend the programs to get a better overview
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
@Andy Ful
When doing a Google search on "Andy Ful" one comes to the following site: AndyFul - Overview. It is the Top alternative. It is like a home site for your products since they are all there, except 1 - WHHLight.
The WHHLight is part of a broad Hard_Configurator project, so it is contained in the Hard_Configurator on GitHub.
But in the future, I do not exclude the possibility of making it an independent project.
What do you say, does not these 2 actions seems good, make sence?
Yes.
Now your site and the programs are known to just a small group of users, and mostly discussed here on MT and little else. With the above actions the spreed will be a bit better and it will be easier for my followers on the site i recommend the programs to get a better overview
WHHLight is in the early development stage. So for now, a small group of users is OK.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
WHHLight vs. Signed Malware
(Smart App Control set to OFF)
In WHHLight, the default WDAC settings are focused on blocking an initial EXE/MSI malware downloaded/executed by the user. The execution is often done with the SmartScreen backend and in most cases WDAC ISG allows files accepted by SmartScreen (even if the same files are blocked by WDAC ISG without SmartScreen backend).
There is an important question: How effective can be SmartScreen against initial EXE/MSI malware?
The answer is not easy because most EXE samples are not initial malware but payloads. Initial malware samples are more frequently signed compared to payloads. The unsigned malware has close to 0 chances to get a positive SmartScreen reputation. The signed files can get it via a highly reputable certificate.
Attack flow:
malspam ----> email attachment ----> user opens an attachment and executes GuLoader (EXE file) ----> GuLoader downloads/executes payloads
GuLoader examples from the past:
https://asec.ahnlab.com/en/55978/
https://www.crowdstrike.com/blog/guloader-malware-analysis/
https://www.trellix.com/blogs/research/guloader-the-nsis-vantage-point/
The attack can be easily stopped by WDAC ISG when the file does not have a Mark of the Web (MotW), because the SmartScreen backend is not triggered. In such a case ISG uses a very restrictive reputation. In another case (EXE file with MotW), ISG will use the SmartScreen reputation, and malware signed with a highly reputable certificate can bypass WDAC ISG.
In my test, I chose the recent samples of GuLoader malware. It is used often as an initial malware to download/execute well-known malware (Remcos, Agent Tesla, Formbook, Lokibot, NanoCore, and more).
I was surprised because 75% of GuLoader samples (35 total samples from February 2024) were digitally signed. Another surprise was that all samples were blocked by SmartScreen (when MotW was added by me) and by WDAC ISG (files with or without MotW).
I checked the certificates. Each sample used a different certificate and all certificates were fake.
Conclusion.
The default WDAC ISG settings in WHHLight can be very efficient in blocking EXE malware (also digitally signed) used in widespread attacks.
It does not mean that similarly high efficiency will be for highly targeted attacks on Enterprises, because of using highly reputable certificates.
Edit.
After adding 24 new samples, the result did not change much (59 total samples, 78% signed, all blocked, all signed with fake certificates).
(Smart App Control set to OFF)
In WHHLight, the default WDAC settings are focused on blocking an initial EXE/MSI malware downloaded/executed by the user. The execution is often done with the SmartScreen backend and in most cases WDAC ISG allows files accepted by SmartScreen (even if the same files are blocked by WDAC ISG without SmartScreen backend).
There is an important question: How effective can be SmartScreen against initial EXE/MSI malware?
The answer is not easy because most EXE samples are not initial malware but payloads. Initial malware samples are more frequently signed compared to payloads. The unsigned malware has close to 0 chances to get a positive SmartScreen reputation. The signed files can get it via a highly reputable certificate.
Attack flow:
malspam ----> email attachment ----> user opens an attachment and executes GuLoader (EXE file) ----> GuLoader downloads/executes payloads
GuLoader examples from the past:
https://asec.ahnlab.com/en/55978/
https://www.crowdstrike.com/blog/guloader-malware-analysis/
https://www.trellix.com/blogs/research/guloader-the-nsis-vantage-point/
The attack can be easily stopped by WDAC ISG when the file does not have a Mark of the Web (MotW), because the SmartScreen backend is not triggered. In such a case ISG uses a very restrictive reputation. In another case (EXE file with MotW), ISG will use the SmartScreen reputation, and malware signed with a highly reputable certificate can bypass WDAC ISG.
In my test, I chose the recent samples of GuLoader malware. It is used often as an initial malware to download/execute well-known malware (Remcos, Agent Tesla, Formbook, Lokibot, NanoCore, and more).
I was surprised because 75% of GuLoader samples (35 total samples from February 2024) were digitally signed. Another surprise was that all samples were blocked by SmartScreen (when MotW was added by me) and by WDAC ISG (files with or without MotW).
I checked the certificates. Each sample used a different certificate and all certificates were fake.
Conclusion.
The default WDAC ISG settings in WHHLight can be very efficient in blocking EXE malware (also digitally signed) used in widespread attacks.
It does not mean that similarly high efficiency will be for highly targeted attacks on Enterprises, because of using highly reputable certificates.
Edit.
After adding 24 new samples, the result did not change much (59 total samples, 78% signed, all blocked, all signed with fake certificates).
Last edited:
The WHHLight is part of a broad Hard_Configurator project, so it is contained in the Hard_Configurator on GitHub.
But in the future, I do not exclude the possibility of making it an independent project.
Yes.
WHHLight is in the early development stage. So for now, a small group of users is OK.
The WHHLight is part of a broad Hard_Configurator project, so it is contained in the Hard_Configurator on GitHub.
But in the future, I do not exclude the possibility of making it an independent project.
Yes.
WHHLight is in the early development stage. So for now, a small group of users is OK.
It is also a fact that your programs have not raised as much attention as they should on the net, besides Configure Defender, it was actually that i meant, but not wrote, when i mentioned "a small group here on MT". It would really be good if many other sites did some "reviews", sites like gHack, WindowsClub etc
Anyway, the site i post some security tips on now and then over the years has a thread with little over 6000 postings but have more or less died since Ms Defender got potent. So instead of people wading through all that to find good tips, info and facts, i thought i should do a summary posting in its end, which is where people usually starts to look in it for mentioned facts. A lot of things has changed also since my last post there since you have been busy. A summary of the facts regarding the "extra" tools that exist to make Ms Defender and its firewall more potent and easier to handle for the benefit for average users.
So that is my aim with this, but for now i will wait until WHHL is not so much "in the early development stage".
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
So that is my aim with this, but for now i will wait until WHHL is not so much "in the early development stage".
Thanks.
WHHLight uses WDAC ISG which is poorly documented and tested. Some practical aspects must be confirmed. I have to be certain that WDAC ISG + SmartScreen can be both useful and strong protection at home. Before the year 2023, ISG had some flaws so in the first version of WHHLight, I used WDAC policy without ISG. After a discussion on another WHHLight thread, I changed my mind to include ISG.
So far, I am not disappointed. Similar problems were with Software Restriction Policies (SWH settings), which I researched and tested for a few years when creating Hard_Configurator.
Last edited:
The WHHLight is part of a broad Hard_Configurator project, so it is contained in the Hard_Configurator on GitHub.
But in the future, I do not exclude the possibility of making it an independent project.
Yes.
WHHLight is in the early development stage. So for now, a small group of users is OK.
Hm. I just downloaded H_C and i could not find WHHL in it. Neither SWH, which i thought would be in it.
Guidance please.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
Hm. I just downloaded H_C and i could not find WHHL in it. Neither SWH, which i thought would be in it.
Guidance please.
https://github.com/AndyFul/Hard_Configurator/tree/master/WindowsHybridHardening
Last edited:
F
ForgottenSeer 107474
@Andy Ful two questions
What is the difference in protection between WDAC-ISG and ConfigureDefender on MAX? (the information I can find is that they share the same backbone infrastructure without explaining differences)
When I run WHHL I get this error (and an usigned program runs fine, even after removing all user space folders), does this mean that WDAC is not installed?
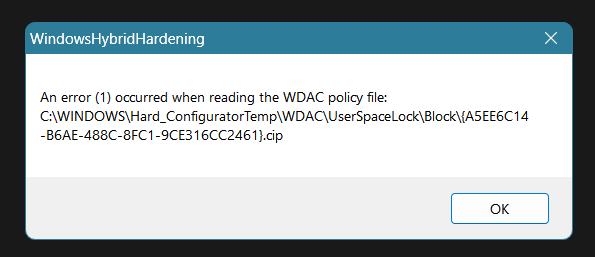
What is the difference in protection between WDAC-ISG and ConfigureDefender on MAX? (the information I can find is that they share the same backbone infrastructure without explaining differences)
When I run WHHL I get this error (and an usigned program runs fine, even after removing all user space folders), does this mean that WDAC is not installed?
Last edited by a moderator:
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
@Andy Ful two questions
What is the difference in protection between WDAC-ISG and ConfigureDefender on MAX? (the information I can find is that they share the same backbone infrastructure without explaining differences)
- Most of the ConfigureDefender settings are related only to Microsoft Defender. WDAC ISG works with other AVs.
- ConfigureDefender MAX settings protect all locations (with a few exclusions). WDAC ISG automatically allows Non-writable locations and WDAC whitelisted locations.
The exclusions made via ConfigureDefender are ignored by WDAC. - The 0-day protection for EXE files in ConfigureDefender MAX settings is mainly related to the ASR rule "Block executable files from running unless they meet a prevalence, age, or trusted list criteria". It works similarly to WDAC ISG without SmartScreen backend and only for a short time (usually 24 hours) from the moment when the sample is recognized for the first time in the Microsoft cloud.
- WDAC ISG policy can block MSI files and DLLs, but ConfigureDefender settings cannot.
- When the Internet connection is turned OFF, WDAC will still block new files. Some ConfigureDefender settings (like the ASR rule from point 3) require an Internet connection.
When I run WHHL I get this error (and an usigned program runs fine, even after removing all user space folders), does this mean that WDAC is not installed?
View attachment 281618
Probably yes. The first version of WHHLight used a different WDAC policy which can produce an error. Another reason can be related to 3rd part security software.
Please use Menu >> Restore Windows Defaults, run WHHLight again, and switch < WDAC > to ON.
Please let me know if there will be any alerts.
Last edited:
F
ForgottenSeer 107474
@Andy Ful
Thanks for the answers.
Ad1. So the benefits of WHHL over ConfigureDefender on MAX (for someone not using third-party security) is that I now also have the cloud whitelist protection for DLL's and MSI's
(I have one unsigned app, which user folder I added to the whitelist. I removed write/delete rights of that folder with ACL for everyone except admins).
Ad2. I restored Windows Defaults and now I did not get an error message. I have tried one of the earliest versions you posted, so your explanation makes sense. WDAC is working
Thanks for the answers.
Ad1. So the benefits of WHHL over ConfigureDefender on MAX (for someone not using third-party security) is that I now also have the cloud whitelist protection for DLL's and MSI's
(I have one unsigned app, which user folder I added to the whitelist. I removed write/delete rights of that folder with ACL for everyone except admins).
Ad2. I restored Windows Defaults and now I did not get an error message. I have tried one of the earliest versions you posted, so your explanation makes sense. WDAC is working
Last edited by a moderator:
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,777
@Andy Ful
(I have one unsigned app, which user folder I added to the whitelist. I removed write/delete rights of that folder with ACL for everyone except admins).
If you removed the write/delete rights of that folder except for admins, then the app should work even if removed from the whitelist (the application folder is Non-writable).
The cons of removing write/delete rights are that this app cannot write anything in the folder. Anyway, many applications can still work well.
the best solution is installing applications in Program Files (if there is such an option).
F
ForgottenSeer 107474
If you removed the write/delete rights of that folder except for admins, then the app should work even if removed from the whitelist (the application folder is Non-writable).
The cons of removing write/delete rights are that this app cannot write anything in the folder. Anyway, many applications can still work well.
the best solution is installing applications in Program Files (if there is such an option).
Could you explain why you choose to enabled the SRP settings also for admins?
Similar threads
- Replies
- 253
- Views
- 34,105
- Replies
- 18
- Views
- 1,113
- Replies
- 23
- Views
- 4,487
