- Sep 2, 2021
- 2,761
I had thought of installing WHHLight with VoodooShield/CyberLock but I'm afraid it would be a duplicate...
No, I do not disable smartscreen. But I like my system to be configurable through Windows Security Center.
Yes, if one can notice it. Anyway, there is no functional difference (except if one chooses to disable SmartScreen).The problem is that "warn" differs from "user" that was set by the high settings of ConfigureDefender, that causes some confusion.
That is my opinion too.I had thought of installing WHHLight with VoodooShield/CyberLock but I'm afraid it would be a duplicate...
No problem, if there is no functional differenceYes, if one can notice it. Anyway, there is no functional difference (except if one chooses to disable SmartScreen).
But all of this is logical. ConfigureDefender does some hardening and WHHLight applies additional restrictions. One cannot expect that ConfigureDefnder settings will be completely independent of WHHLight settings.

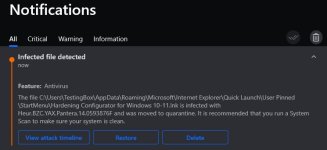
BitDefender detects it as a Trojan and deletes the taskbar shortcut.
(ShellItem Unicode) is malware of type Heur.BZC.YAX.Pantera.14.0593876F
It needs to be fixed.
A workaround is to put the Hardening Configurator on the desktop, unblock it and drag it to the taskbar and pin it there.
Then it works but pinning it from the desktop folder to the taskbar results in the AV deleting the shortcut.
The SRP method in H_C and SimpleWindowsHardening should be changed to allow both UWP apps and desktop apps from the Microsoft Store to be installed. There is no reason to list them as untrusted. It may be better to block apps downloaded from the Internet.WHHLight vs. AppInstaller
https://malwaretips.com/threads/mic...col-handler-abused-in-malware-attacks.127972/
https://www.microsoft.com/en-us/sec...tivated-threat-actors-misusing-app-installer/
The original attacks were performed by abusing the ms-appinstaller protocol handler. This method is now patched - Microsoft disabled that protocol by default.
Anyway, a similar attack can be performed without using ms-appinstaller:
Malicious URL or email attachment (ZIP, ISO, etc.) ---> malicious MSIX package (digitally signed) ---> AppInstaller runs malware from the MSIX package.
SWH default settings in WHHLight block AppInstaller.
View attachment 280828
The blocked event can be seen in the EventViewer (System, Id = 10010).
In WHHLight the APPX and MSIX packages are blocked by Exploit Protection and not by SRP. The ExploitProtection method allows the installation of UWP apps and desktop apps from Microsoft Store. The SRP method (used in H_C and SimpleWindowsHaredening) is more restrictive and allows only UWP apps from Microsoft Store.
What is detected, WHHLight, Hard_Configurator, or the shortcut?
Why the shortcut is on the taskbar?
The SRP method in H_C and SimpleWindowsHardening should be changed to allow both UWP apps and desktop apps from the Microsoft Store to be installed. There is no reason to list them as untrusted. It may be better to block apps downloaded from the Internet.
The Hard Configurator. BitDefender views it as a Trojan and automatically deletes it. Of course its a false positive.
I want to make changes on the fly - easy access to the app on the taskbar.
I run BitDefender Endpoint Security Tools.Which file is detected?
Which edition of Bitdefender do you use?
Install WHHLight, create a shortcut for the installed WHHLight exe like Pin to start, install BD and BD will detect only the shortcut as malware. It won't delete the exe.What is detected, WHHLight, Hard_Configurator, or the shortcut?
Why the shortcut is on the taskbar?
Install WHHLight, create a shortcut for the installed WHHLight exe like Pin to start, install BD and BD will detect only the shortcut as malware. It won't delete the exe.
This "Heur.BZC......" is a Bitdefender heuristic to detect shortcut malware. You may try to create a shortcut, zip the file and upload to VT to check if BD detects it. Then that would be easy for you to report as a false positive without needing to install Bitdefender on a VM.
I run BitDefender Endpoint Security Tools.
The Security Console Antimalware reports:
On-Access scanning has detected a threat. The file has been deleted. C:\Users\User Name\OneDrive\Desktop\WindowsHybridHardeningLight_1011.exe - Shortcut.lnk=>(ShellItem Unicode) is malware of type Heur.BZC.YAX.Pantera.14.0593876F
So, your custom-made shortcut on the taskbar is detected.
I am afraid that there will be a problem. From my experience with Bitdefender, they require the installation of the concrete Bitdefender AV, and ask which concrete Bitdefender feature produces the issue. Another problem is that the issue does not happen due to the WHHLight installation, but due to the user's custom actions and Bitdefender treatment of shortcuts on the taskbar.
Such issues cannot be solved via false positive submissions, but via the developer channel. Unfortunately, it seems that Bitdefender does not use such a channel.
To be fair, you're not to blame. Its not easy to know what situation can trigger a false positive and its annoying when legitimate security software gets flagged as malicious. I mean its ridiculous to delete just the shortcut while the app itself is still on the PC.
Did you try the same with another legal EXE (not from WHHLight tools) copied to the WHHLight folder?Maybe WHHLight.exe's reputation (not seen by BD on enough endpoints) is somehow making Bitdefender detect the shortcut? I don't know how it works. In my case, the shortcut was already created and then a system restart after installing Bitdefender triggered the detection at startup. I'll try to reproduce the scenario on my VM and let you know if I can.
Edit: Reproduced.
View attachment 281574View attachment 281575
Just now did and yes, even those are detected. Copied Norton Power Eraser exe and some other apps, right clicked and selected pin to taskbar and it's blocked.Did you try the same with another legal EXE (not from WHHLight tools) copied to the WHHLight folder?