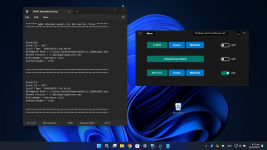
WHHLight vs. Coyote Trojan
(Smart App Control set to OFF)
Sixty-one banking institutions, all of them originating from Brazil, are the target of a new banking trojan called Coyote. "This malware utilizes the Squirrel installer for distribution, leveraging Node.js and a relatively new multi-platform programming language called Nim as a loader to...

malwaretips.com
We will delve into the workings of the infection chain and explore the capabilities of the new Trojan that specifically targets users of more than 60 banking institutions, mainly from Brazil.

securelist.com
Attack flow:
The new aspects of the attack start after malicious DLL side-loading. The hashes of DLLs used in the attacks are included in the Securelist article. But, the initial malware (malicious Squirrel Installer) is skipped. Anyway, I found a few initial malware files on the VitusTotal:
9c6fc9e0854eaf5a0720caab1646f48c7992f6f4051438004598af89102a49eb
096d7765f278bb0de33fbfa0a15413a2432060d09c99f15c6ca900a6a8a46365
aedffb9cf780bb52c68586ceb238fcaf90253524f06a4a338edc6437409e51c5
3cbc282c6a51edff4e762267332e1ff2a503f7ba8a7b2a10c9ff404a7bda913b
All samples are unsigned and can be blocked by SmartScreen and WDAC ISG ( < WDAC > option must be set to ON).