ConfigureDefender utility for Windows 10/11
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
@Andy Ful ASR rule "Block executable files from running unless they meet a prevalence, age, or trusted list criterion" used to block this installer, librewolf.106.x.x when downloading a fresh release. Today, neither the download nor installation was blocked but the process, i.e. opening LibreWolf, was blocked.
This seems like new behavior by Defender, or at least I've never experienced this before that I can remember. Or, is it dependent on Defender Cloud Protection Level, i.e. High+/Block vs Default? Now I'm thinking it's the latter.
\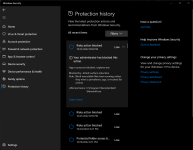
This seems like new behavior by Defender, or at least I've never experienced this before that I can remember. Or, is it dependent on Defender Cloud Protection Level, i.e. High+/Block vs Default? Now I'm thinking it's the latter.
\

Last edited:
That is rare behavior, but it may be caused by a strange installation of LibreWolf. After the installation, the application executable, and most files have got a strange date 01.01.2010 ??? Furthermore, in the file properties, there is no info about the application details. So, the executable may look very suspicious. Let's wait one or two days, to see what will happen.@Andy Ful ASR rule "Block executable files from running unless they meet a prevalence, age, or trusted list criterion" used to block this installer, librewolf.106.x.x when downloading a fresh release. Today, neither the download nor installation was blocked but the process, i.e. opening LibreWolf, was blocked.
This seems like new behavior by Defender, or at least I've never experienced this before that I can remember. Or, is it dependent on Defender Cloud Protection Level, i.e. High+/Block vs Default? Now I'm thinking it's the latter.
@Andy Ful The ASR rule "Block abuse of exploited vulnerable signed drivers" blocks KVRT.exe, whereas Core Isolation>MS Vulnerable Driver Blocklist does not, which suggests to me that the two protection mechanisms aren't identical. Any ideas as to the difference? 
@Andy Ful The ASR rule "Block abuse of exploited vulnerable signed drivers" blocks KVRT.exe, whereas Core Isolation>MS Vulnerable Driver Blocklist does not, which suggests to me that the two protection mechanisms aren't identical. Any ideas as to the difference?
KVRT.exe is allowed to run - only the klmd.sys driver is blocked by the ASR rule. I am not sure if this driver is also on the Vulnerable Driver Blocklist. The drivers are distributed with several file names, so the driver's Authentihash would be required. I cannot test Core Isolation.
Anyway, I think that the ASR rule can be the best updated one.
Yes, but after the driver is blocked, the app crashes and cannot continue. OTOH, the driver isn't blocked and the app is able to run with built-in Vulnerable Driver Blocklist enabled. I'm trying to understand the difference between the the two protection methods.KVRT.exe is allowed to run - only the klmd.sys driver is blocked by the ASR rule.
Yes, it's possible to harden your OS further with the settings, either with one of the other built-in profiles or your own custom configuration. BTW, any questions about H_C should be posted in Hard_Configurator - Windows Hardening Configurator@Andy Ful how to leave the Hard_Configurator settings more hardened or at maximum? is it possible? or only in the recommended settings?
The Core Isolation would block the klmd.sys driver even if it had been already installed. If you enabled Core Isolation and the driver has been installed, then it is not on the Blocklist.Yes, but after the driver is blocked, the app crashes and cannot continue. OTOH, the driver isn't blocked and the app is able to run with built-in Vulnerable Driver Blocklist enabled. I'm trying to understand the difference between the the two protection methods.
If I correctly recall the ASR rule will block the driver only on installation (the already installed drivers are not blocked).
@Andy Ful In DefenderUI there is a option to disable "File hash computation" so I would like to know if that option is available in your ConfigureDefender utility.
@Andy Ful In DefenderUI there is a option to disable "File hash computation" so I would like to know if that option is available in your ConfigureDefender utility.
No. It is disabled by default in Windows. It can be enabled via GPO, but at some performance cost.
ConfigureDefender is focused on real-time protection. This feature is related only to file scanning and does not have an impact on real-time protection.
I contacted Bitdefender staff (several months ago) and explained to them that Bitdefender blocks PowerShell as a child process of ConfigureDefender. I suggested a solution but they did manage to remove the issue.
Anyway, running ConfigureDefender is not necessary when BitDefender is an active AV.
Yes, their Advanced Threat Protection is slightly dumb. But, it is not harmful and can be efficient anyway.
In some way they are right. Running ConfigureDefender is unwanted in this particular situation.
In some way they are right. Running ConfigureDefender is unwanted in this particular situation.
Yes, it was by chance that when I went to access ConfigureDefender I installed the BD yesterday, and it had been years since I had tested it, but I did not uninstall Hard_Configurator.Anyway, running ConfigureDefender is not necessary when BitDefender is an active AV.
Andy the name itself says it all ConfigureDefender, not ConfigureBitdefender.In some way they are right. Running ConfigureDefender is unwanted in this particular situation.
The problem is slightly more complex when someone used Defender with ConfigureDefender, before using Bitdefender. Let's consider the situation when H_C is uninstalled for some reason when using Bitdefender. In this case, the uninstallation will fail to remove the advanced Defender settings (due to Bitdefender blocks). The user can be surprised after uninstalling Bitdefender because Defender will not work on default settings. This was my concern when I discussed the issue with the Bitdefender staff.Andy the name itself says it all ConfigureDefender, not ConfigureBitdefender.
Just enter this in Terminal as administrator and restart the system to make MD log hash of detected malware:@Andy Ful In DefenderUI there is a option to disable "File hash computation" so I would like to know if that option is available in your ConfigureDefender utility.
You'll be able to see the hash in ConfigureDefender log. Andy added the option to log this event in the past when I asked for it as a feature request.reg add "HKLM\SOFTWARE\Policies\Microsoft\Windows Defender" /v "ThreatFileHashLogging" /t REG_DWORD /d "1" /f
Usually, anything that's not trusted/whitelisted by Bitdefender and tries to make changes to MD will get detected by Bitdefender. Generally, only malicious programs will try to tamper with MD's settings. So in that case, Bitdefender's approach is understandable. It's just unfortunate that it seems ConfigureDefender is not whitelisted by BD. But as Andy already said, a user doesn't need ConfigureDefender with a third-party AV installed. So it's not a big deal.
Wow, that one suited me personally, I think Andy unknowingly lambasted me.The problem is slightly more complex when someone used Defender with ConfigureDefender, before using Bitdefender.
This is why I registered here on MT, there are many experienced, veteran and intelligent people here. That's good to know, now I am prepared I created a backup image in Macrium and then installed RBX, just restore a snapshot or restore the image, thank you very much for clarifying on this, I hope people don't use ConfigureDefender with Bitdefender and with any other third party product it is just together with Microsoft Defender/Windows Defender just to reinforce Windows security and a hardening in MD settings.Let's consider the situation when H_C is uninstalled for some reason when using Bitdefender. In this case, the uninstallation will fail to remove the advanced Defender settings (due to Bitdefender blocks). The user can be surprised after uninstalling Bitdefender because Defender will not work on default settings. This was my concern when I discussed the issue with the Bitdefender staff.
Yes, I added all Windows folders and Hard_Configurator in exclusions in BD afterwards, and it still got blocked by Bitdefender. BD even created the generic name for threat, I won't post it because I know the tool so it is reliable new people can be thoughtful, I never want to tarnish anyone's reputation here. I will even apologize to Andy, because a picture can be worth a thousand words, good thing I did not post it, he knows my intention was not that.It's just unfortunate that it seems ConfigureDefender is not whitelisted by BD.
Yes, that's right, I removed the BD. What difference it made in my machine after removing Bitdefender is quite remarkable, now it is much lighter, I don't understand why there are people who complain that MD is heavy around. Despite the bug that day 13 even so MD managed to win me and after the test that @Shadowra did, changed my view on the AV of Windows 10/11.But as Andy already said, a user doesn't need ConfigureDefender with a third-party AV installed. So it's not a big deal.
It was getting detected by the behavior blocker so the exclusions had to be made for Advanced Threat Defense not the Antivirus component.Yes, I added all Windows folders and Hard_Configurator in exclusions in BD afterwards, and it still got blocked by Bitdefender. BD even created the generic name for threat
But it's not your fault. It's not obvious the way it is designed. I know about it only because I have experience with it.
Anyway, for using window's built-in security, it's better to stick to Microsoft Defender. So, enjoy MD+H_C combination
You may also like...
-
Windows 11 Defender Tuning: Safer Settings That Don’t Hurt Performance
- Started by Bot
- Replies: 1
-
Hot Take Microsoft finally admits almost all major Windows 11 core features are broken
- Started by Brahman
- Replies: 18
-
-
New Update Windows 11 Patch Tuesday January 2026 (KB5074109, KB5073455)
- Started by silversurfer
- Replies: 18
-
AExtending Bluetooth® LE Audio on Windows 11 with shared audio (preview)
- Started by Amanda Langowski
- Replies: 0


